Etcd REST API unauthorized access vulnerability
According to securityaffairs reports recently, security researcher Giovanni Collazo discovered through the Shodan search engine that nearly 2,300 servers installed with the etcd component were exposed on the Internet, using some simple scripts to obtain login credentials from them, such as cms_admin, mysql_root, Postgres, etc… Currently, Collazo has successfully tested and retrieved about 750 MB of data from these servers from 1,485 IPs, including 8,781 passwords, 650 AWS access keys, 23 keys, and 8 private keys.
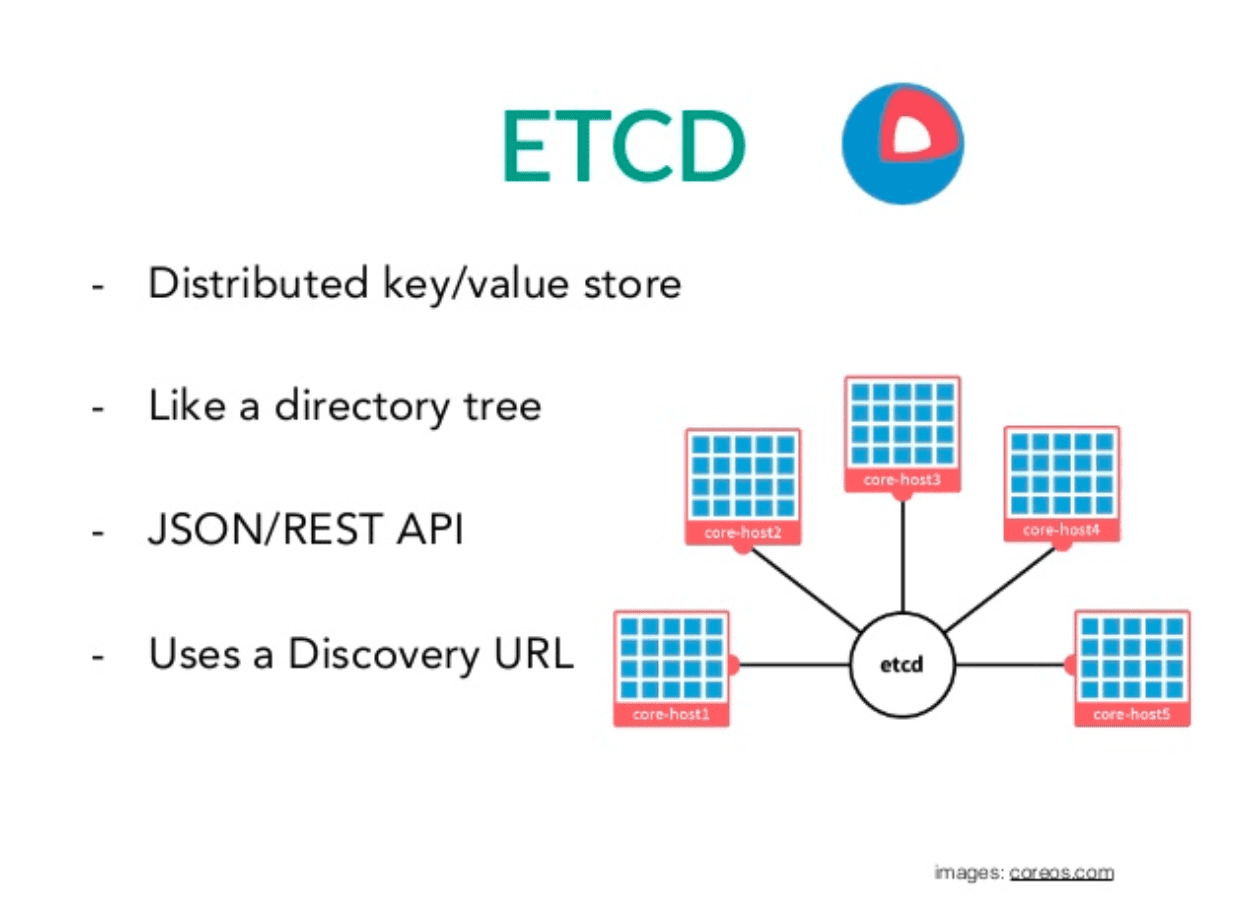
Etcd is a distributed key-value store and a database that provides a reliable way to store data across clusters of machines. It is typically used to store and distribute passwords and configuration settings between various servers and applications. Etcd implements a programming interface that can be queried and, by default, does not require authentication to return administrative login credentials.
Although Collazo did not test these credentials, some of them were presumed to be valid and could be used by attackers to break into the system. In addition, according to Collazo, anyone needs only a few minutes to get a list of hundreds of database certificates that can be used to steal data or perform ransomware attacks.
To ensure the security of the etcd installation, Collazo recommends enabling authentication and taking it offline when it is not needed, or setting up a firewall to prevent unauthorized persons from querying etcd servers.
Read Etcd REST API Unauthorized access vulnerability
Source: securityaffairs





