EV: IDS Evasion via TCP/IP Packet Manipulation
EV: IDS Evasion via TCP/IP Packet Manipulation
EV is a tool that allows you to craft TCP packets and leverage some well-known TCP/IP packet manipulation techniques to evade IDS devices.
It supports HTTP protocol but unfortunately not HTTPS protocol. The handshake process of TLS is quite complicated and I haven’t figured out how to craft TLS packets elegantly.
This tool is written in Python and QT5, using Scapy to make packets. So though this software is tested on the Windows platform only, it theoretically works on other platforms like Linux or MacOS.
Install
git clone https://github.com/TomAPU/ev.git
cd ev
pip3 install -r requirements.txt
Use
python3 ev.py
or you can click run.bat in the root directory of the software to start it.

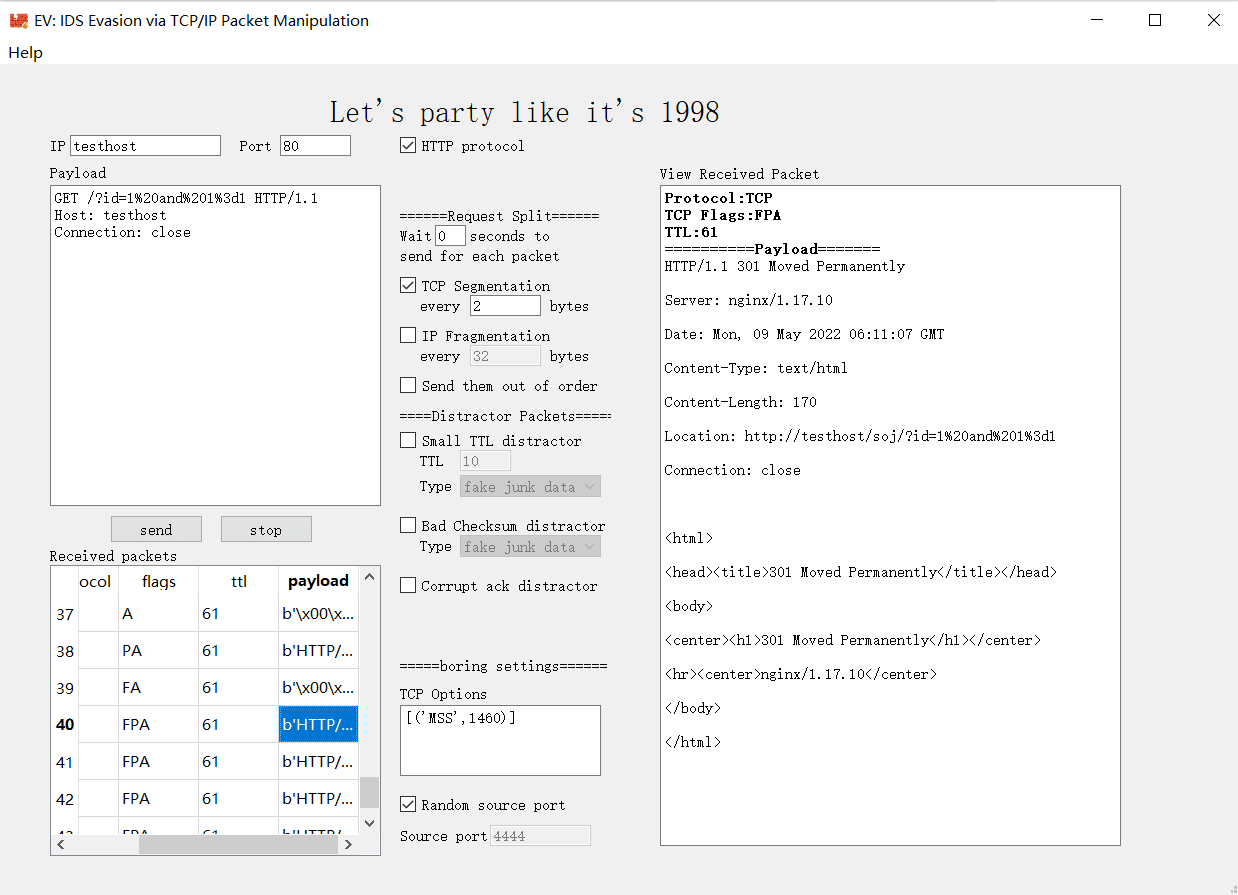
Fill IP, Port, and Payload fields and click the “Send” button to send the TCP packet to the target. You can also set TCP options and source port. Remember that TCP options are tcp options supported by scapy.
You can view response packets in the “Received packets” window and click the packet to view it in the “View Received Packet” window. This is implemented by scapy’s sniff() function, it finds packets that match the target IP or is ICMP protocol(so that you can find TTL exceeded packets). However, sniff() sometimes records packets duplicately. So I strongly recommend users use WireShark if you’ve installed one to see received packets.
Request Split
You can use TCP Segmentation and IP Fragmentation to break the TCP packet into pieces and send them to the target. This may defeat IDS devices that don’t support TCP/IP reassembly.
Increasing wait time or sending packets out of order may also circumvent IDS devices who has a very limited capability in TCP/IP reassembly.
Sending Distractor Packets
Distractor packets are packets that might be ignored by the target and be recognized by IDS devices.
Small TTL distractor packets are packets’ TTL are subtracted to 0 between the IDS device and the target. The target will not receive this packet because the packet has been dropped before reaching the target. But IDS might think that the packet arrives at the target. Therefore, sending small TTL distractor packets containing junk data or RST flags may distract the process of reassembling TCP packets, leading to an evasion.
Bad Checksum packets are packets with the wrong TCP checksum. Packets with the wrong checksum are ignored by the target, but IDS devices may not calculate the checksum and reassemble all packets directly, which leads to an evasion.
Corrupt ack distractor packets are packets’ ACK field is corrupted. The target ignores such packets because of the wrong ACK field, but IDS might reassemble all packets directly, which leads to an evasion.
Source: https://github.com/TomAPU/