EvilAP_Defender: Protect your Wireless Network from Evil Access Points
EvilAP_Defender is an application that helps a wireless network administrator to discover and prevent Evil Access Points (AP) from attacking wireless users.
The application can be run at regular intervals to protect your wireless network from Evil Twin-like attacks. By configuring the tool you can get notifications sent to your email whenever an evil access point is discovered. Additionally, you can configure the tool to perform DoS on the legitimate wireless users to prevent them from connecting to the discovered evil AP in order to give the administrator more time to react. However, notice that the DoS will only be performed for evil APs which have the same SSID but different BSSID (AP’s MAC address) or running on a different channel. This is to avoid DoS your legitimate network.
The tool is able to discover Evil APs using one of the following characteristics:
- Evil AP with a different BSSID address
- Evil AP with the same BSSID as the legitimate AP but a different attribute (including channel, cipher, privacy protocol, and authentication)
- Evil AP with the same BSSID and attributes as the legitimate AP but different tagged parameter – mainly different OUI (tagged parameters are additional values sent along with the beacon frame. Currently no software based AP gives the ability to change these values. Generally, software-based APs are so poor in this area).
Whenever an Evil AP is discovered the tool will alert the admin through email (SMS will be supported soon). Additionally, the tool will enter into a preventive mode in which the tool will DoS the users of the legitimate wireless network from connecting to the discovered Evil AP. The tool can be configured easily by starting in what we call “Learning Mode”. In this mode, you can whitelist your legitimate network. This can be done by following the wizards during the Learning Mode. You can also configure the preventive mode and admin notification from there as well. Finally, you need to change into Normal Mode or re-run the tool in this mode in order to start discovering Evil APs.
Installation
Requirement
- Aircrack-ng suite
- Your wireless card must be supported by Aircrack-ng. Check the following URL: http://www.aircrack-ng.org/doku.php?id=compatibility_drivers#which_is_the_best_card_to_buy
- MySQL
- Python
- Python libraries: MySQLdb, Scapy, and Netaddr
Download
git clone https://github.com/moha99sa/EvilAP_Defender.git
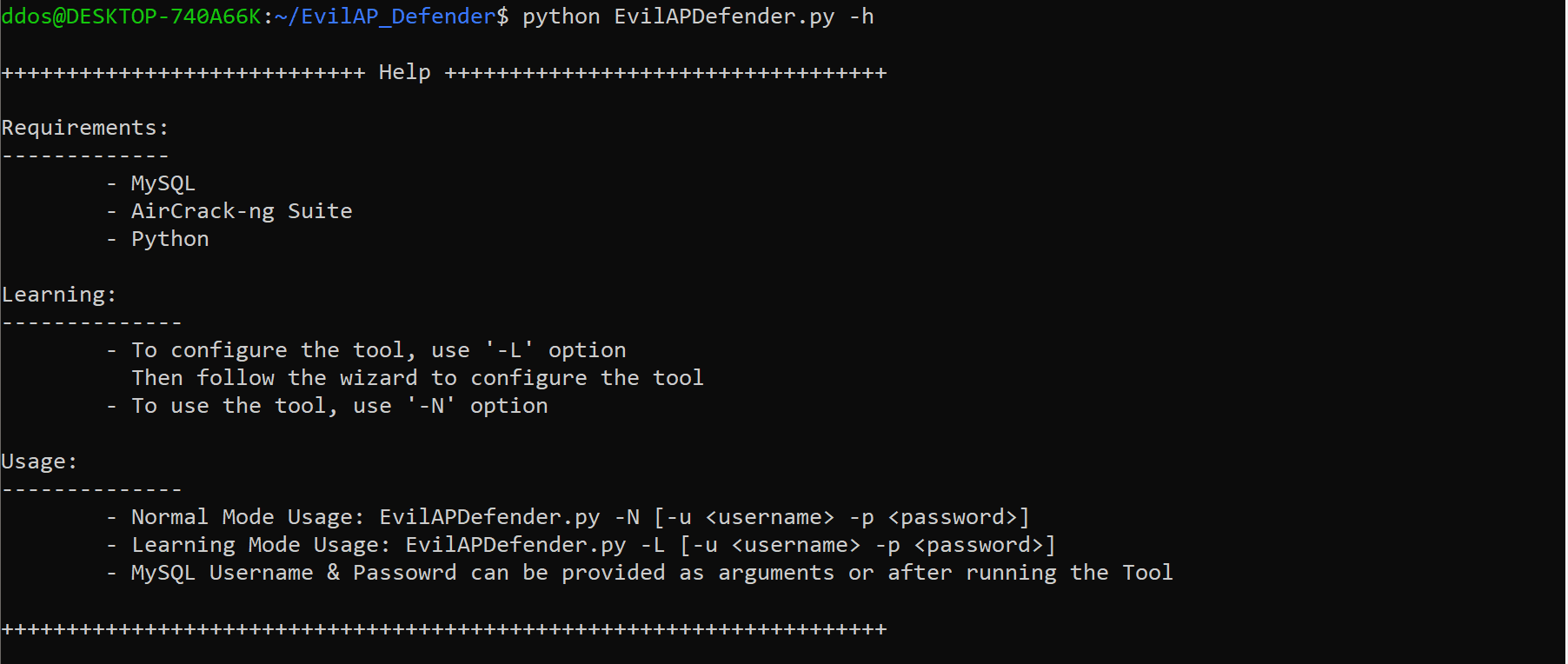
Usage

EvilAP_Defender Copyright (C) 2017 moha99sa
Source: https://github.com/moha99sa





