EvilTwinFramework: A framework for pentesters that facilitates evil twin attacks
EvilTwinFramework
A framework for pentesters that facilitates evil twin attacks as well as exploiting other wifi vulnerabilities
It uses hostapd-wpe to create the access point, so it is highly configurable.
It uses dnsmasq to run the dhcp and dns services.
It uses Apache with help of dnsmasq to launch spoofed web pages as well as captive portals!
Packet sending and receiving are all done via Scapy!

Motivation
The Evil Twin Framework is meant to replace all existing Wi-Fi hacking tools by integrating all features necessary for Wi-Fi penetration testing in one framework. The 3 core features needed are:
Packet Sniffing
Packet Injection
Access Point Creation
All Wi-Fi attacks can be implemented with one or a combination of these core features. By having this platform it will always be possible to contribute with new Wi-Fi attacks that depend on these features.
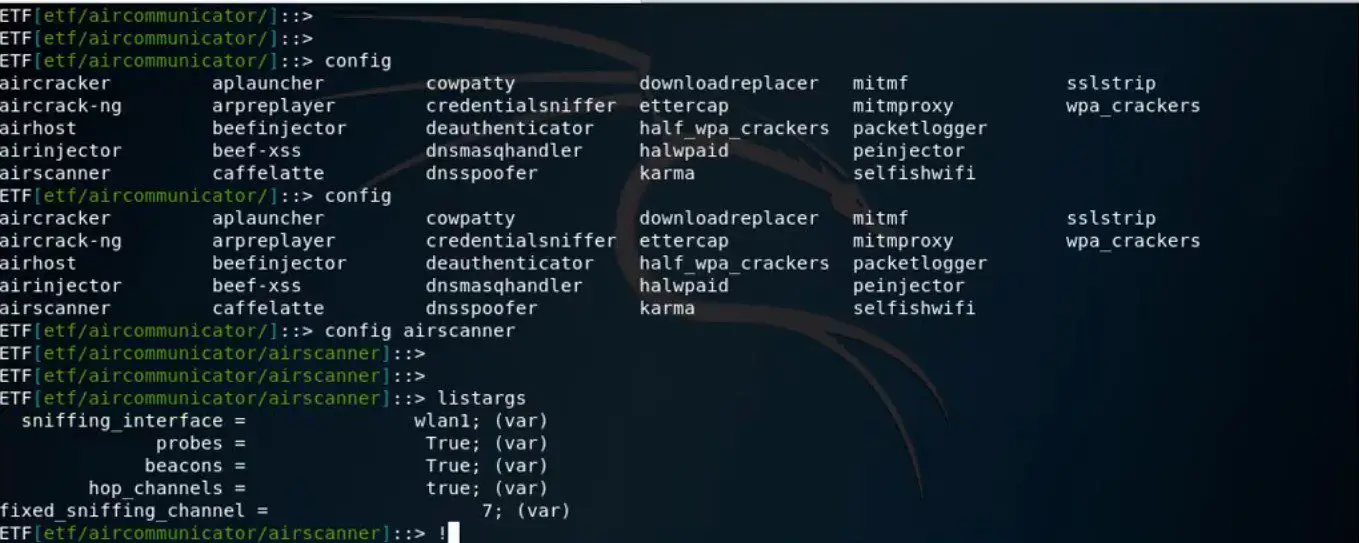
Features
All Forms of Evil Twin AP
The Evil Twin Framework, with the help of hostapd, can mimic any type of Wi-Fi Network. And by using the hostapd-wpe patch it is easy to get WPA-EAP credentials.
One can configure it as a catch-all honeypot to find out the encryption type of a network that was probed for.
One can even create a karma attack and mimic many networks with different ssids on the same Wi-Fi card (as long as it supports ap-mesh mode). This can be done manually if you want different encryption types for different networks, or automatically. The automation works by sniffing for popular probe requests and then creating the most popular one according to how much virtual access points you Wi-Fi card supports.
Handshake and Credential Logging
As said before, with the help of hostapd-wpe WPA-EAP credential sniffing is easy!
You can also spoof DNS with dnsmasq and even create captive-portals to force browsers to your webpage!
You can sniff for WPA-Handshakes and even Half-WPA-Handshakes for ap-less password cracking!
Integrated Man-In-The-Middle
An Evil-Twin is nothing without a proper MITM arsenal!
The framework uses the mitmproxy library to create a local proxy capable of custom Level3 packet manipulation! Some fun ones have already been implemented such as beef hook injection into someone’s webpage, download content replacement with other files (idea stolen from the Wi-Fi Pumpkin Project). And my favourite: .exe file infection with PEInjector. PEInjector does a great job by seamlessly injecting a payload into an exe file without changing its size while at the same time obfuscating the payload to pass AV software.
You can easily contribute and/or make your own custom MITM packet manipulation and add it to the framework. More information will be in the wiki.
Wi-Fi Reconossaince
The framework is able to sniff for access points, probe requests and responses and associating them to Wi-Fi clients. You can also log all of this information.
Packet Injection
Packet Sniffing and Injection is all done via Scapy. This makes it possible to contribute with any feature that involves packet sniffing and custom packet assembly and injection.
For now, the only packet injection feature is deauthentication packets since it is a nice thing to have when trying to catch WPA-Handshakes.
Spawners
Spawners are a great and easy way to use your custom tools in conjunction with the framework. Some tools have already been added since they make a lot of sense: Ettercap, Beef, MITMFramework and SSLStrip.
You can easily add your own, more information will be on the wiki.
Install & Use
Copyright (C) 2017 Esser420





