Exposed Docker APIs Under Attack: New Malware Campaign Deploys “perfctl”
A newly discovered cyberattack campaign has been targeting exposed Docker Remote API servers to deploy the perfctl malware, a malicious software designed to infiltrate and compromise systems by exploiting the Docker environment. The recent report from Trend Micro sheds light on how attackers are probing vulnerable Docker servers, deploying containers, and executing harmful payloads to gain control over the host system.
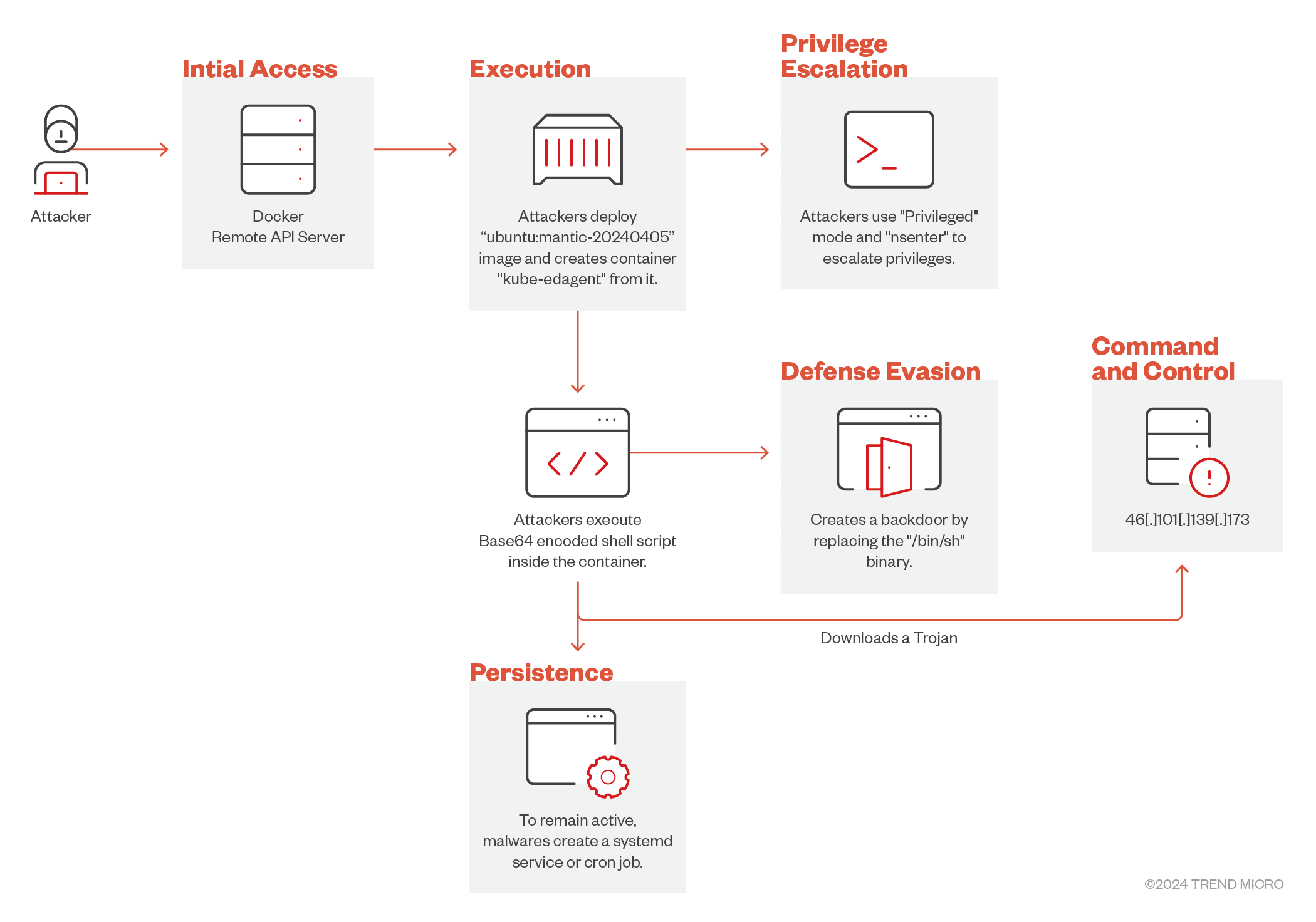
The attack begins with probing the Docker Remote API server, a vital entry point for the subsequent malicious actions. Attackers initiate this process by sending ping requests to the vulnerable server, confirming its presence before executing further commands.
Once the server is identified, the attackers create a Docker container, often using an image like ubuntu:mantic-20240405, and configure it to run in privileged mode. According to the report, “They also utilize “pid mode: host,” allowing the container to share the Process ID (PID) namespace of the host system,” which gives the container elevated privileges, allowing it to interact with host processes directly.
After the container is created, the attackers execute a Base64-encoded payload via the Docker Exec API. The payload contains two key parts:
- Escaping the container: The
nsentercommand is used to access the host system’s namespaces, granting the attacker root-level control. “The payload tries to escape the container by using the “nsenter” command to enter the target process with PID 1,” effectively enabling them to act as if they were directly on the host machine. - Bash script creation: A script named
kubeupdis generated in the/tmpdirectory, setting up environment variables, and downloading a malicious binary disguised as a PHP extension. This binary, once downloaded, is further used to carry out more malicious actions. The report notes that “The script will terminate if the architecture is not “x86_64“, and the binary is only downloaded if the system meets certain criteria
The attackers employ various evasion techniques, such as preventing duplicate processes by checking for already running malicious instances. They also set up persistence mechanisms to ensure the malware remains active, even if system administrators attempt to remove it. If the system is running systemd, a service is created to maintain persistence; otherwise, a cron job is used as a fallback, making it extremely difficult to eradicate.
The malware even employs techniques to disguise its presence, like downloading the malicious binary with legitimate-looking names like “httpd” to avoid file extension-based detection. Additionally, it leverages the Tor network to route traffic through a relay node, further obfuscating its activity.
The exploitation of exposed Docker Remote API servers has become a significant concern for organizations using containerized environments. As Trend Micro emphasizes, “Exploiting exposed Docker remote API servers has now reached a critical level where the attention of an organization and its security professionals is seriously required.” By securing Docker environments and adhering to container security best practices, organizations can significantly reduce the risk of such attacks.





