FBI Warns of PRC-Linked Botnet Targeting Critical Systems, 260,000+ Devices Compromised

A new cybersecurity threat has emerged as U.S. authorities, including the Federal Bureau of Investigation (FBI), Cyber National Mission Force (CNMF), and National Security Agency (NSA), raise alarms about a botnet created and controlled by cyber actors linked to the People’s Republic of China (PRC). These malicious actors have compromised thousands of routers, firewalls, and Internet of Things (IoT) devices across the globe, posing significant risks to both private and public sector networks.
The compromised devices, which include small office/home office (SOHO) routers and network-attached storage (NAS), are now part of a sprawling botnet that the PRC-linked Integrity Technology Group has maintained since mid-2021. The botnet, consisting of over 260,000 devices as of June 2024, has a global footprint, affecting systems in North America, Europe, Asia, and beyond. Many of the compromised devices are still supported by their vendors, underscoring the widespread vulnerability across modern networks.
The botnet, managed through China Unicom Beijing Province Network IP addresses, leverages a sophisticated variant of the Mirai malware, originally designed to hijack IoT devices such as routers, webcams, and digital video recorders (DVRs). Mirai has long been a threat since its source code was leaked in 2016, but the PRC-linked group has customized the malware for more extensive operations, including distributed denial of service (DDoS) attacks and other nefarious activities.
Once compromised, these devices are turned into “bots” controlled by a command-and-control (C2) server, enabling attackers to use them to disrupt network traffic, deliver malware payloads, or act as proxies to conceal their malicious activities. Infected devices send detailed system information to the C2 server for further exploitation, including data on the device’s operating system, memory, and bandwidth capabilities.
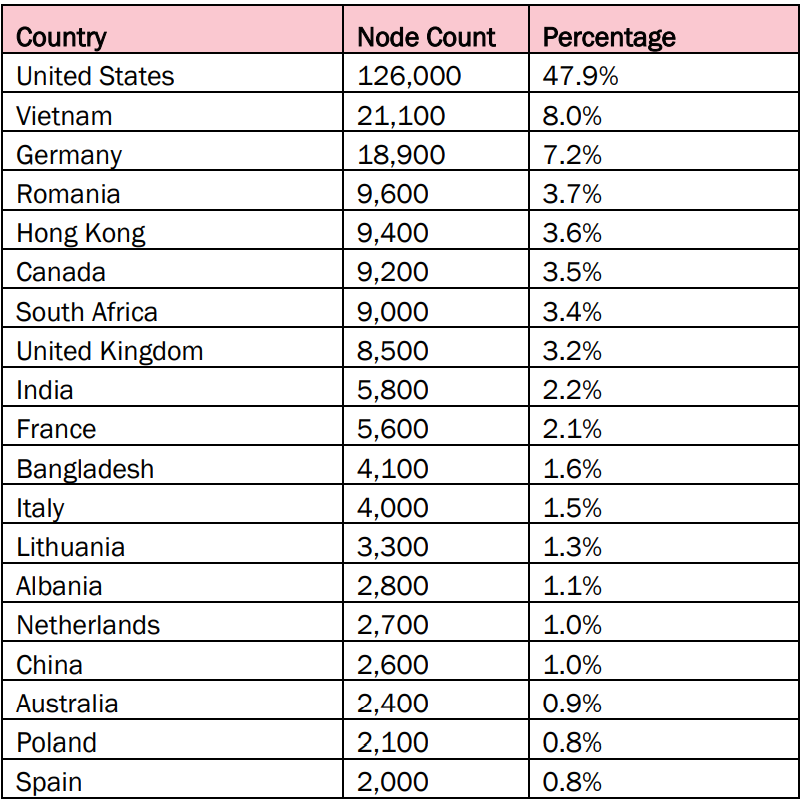
Botnet devices per continent | Image: FBI
The scale of this operation is vast, with compromised devices observed across multiple continents. The United States, with over 126,000 compromised devices, accounts for nearly half of the botnet’s network. Other heavily affected regions include Vietnam, Germany, Canada, and South Africa. Notably, the infected devices are running various Linux-based operating systems, ranging from legacy versions no longer supported by vendors to modern systems still receiving security patches.
The botnet is linked to Integrity Technology Group, a PRC-based company with documented ties to the Chinese government. The group has also been associated with cyber threat actors known as Flax Typhoon, RedJuliett, and Ethereal Panda. U.S. authorities have traced multiple cyber intrusion campaigns targeting American organizations to this botnet infrastructure, heightening concerns about state-sponsored cyberattacks aimed at critical U.S. systems.
Investigators identified over 80 subdomains connected to the botnet’s C2 servers, providing a roadmap for organizations seeking to defend their networks. As part of the advisory, cybersecurity experts recommend disabling unused services, such as remote access protocols and file-sharing services, which could be leveraged for initial compromise. In addition, monitoring network traffic for abnormalities, applying regular patches, and replacing outdated equipment are critical steps to protect against this botnet’s impact.
Organizations are also advised to enforce strict password policies and reboot compromised devices to remove certain types of malware that reside in the host’s memory. For devices that no longer respond to commands, physical reboots may be necessary.
The scale and persistence of this PRC-linked botnet highlight the increasing threat posed by nation-state actors leveraging IoT vulnerabilities. The FBI and its partners are urging exposed vendors, device operators, and network defenders to take swift action to secure their devices, as these compromised systems are poised to be used in further malicious activities, potentially targeting U.S. critical infrastructure.
With millions of records stored in the botnet’s management servers and evidence of ongoing cyberattacks, the PRC’s cyber operations represent a growing concern for global cybersecurity. As the botnet expands, and its operators develop more sophisticated techniques, the international cybersecurity community must remain vigilant and proactive in safeguarding their networks against this evolving threat.
For more technical details, organizations are encouraged to refer to the advisory from the FBI and its partners, and to consult with cybersecurity professionals to bolster their defenses against this pervasive cyber threat.





