feroxbuster v2.10 releases: fast, simple, recursive content discovery tool written in Rust
What the heck is a ferox anyway?
Ferox is short for Ferric Oxide. Ferric Oxide, simply put, is rust. The name rustbuster was taken, so I decided on a variation.
What’s it do tho?
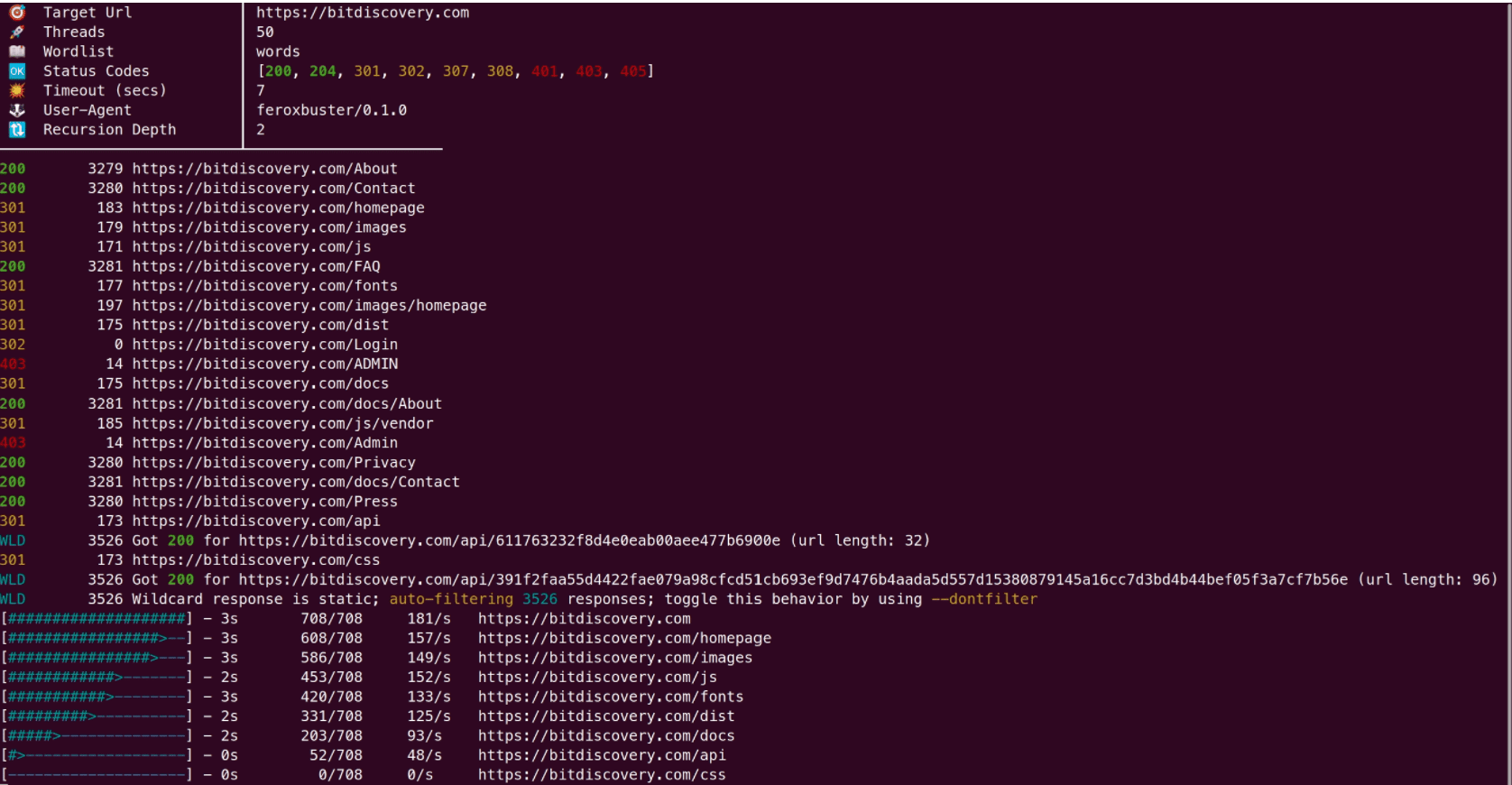
feroxbuster is a tool designed to perform Forced Browsing.
Forced browsing is an attack where the aim is to enumerate and access resources that are not referenced by the web application but are still accessible by an attacker.
feroxbuster uses brute force combined with a wordlist to search for unlinked content in target directories. These resources may store sensitive information about web applications and operational systems, such as source code, credentials, internal network address, etc…
This attack is also known as Predictable Resource Location, File Enumeration, Directory Enumeration, and Resource Enumeration.
Comparison w/ Similar Tools
There are quite a few similar tools for forced browsing/content discovery. Burp Suite Pro, Dirb, Dirbuster, etc… However, in my opinion, there are two that set the standard: gobuster and ffuf. Both are mature, feature-rich, and all-around incredible tools to use.
So, why would you ever want to use feroxbuster over ffuf/gobuster? In most cases, you probably won’t. ffuf in particular can do the vast majority of things that feroxbuster can, while still offering boatloads more functionality. Here are a few of the use-cases in which feroxbuster may be a better fit:
- You want a simple tool usage experience
- You want to be able to run your content discovery as part of some crazy 12 command unix pipeline extravaganza
- You want to scan through a SOCKS proxy
- You want auto-filtering of Wildcard responses by default
- You want recursion along with some other thing mentioned above (ffuf also does recursion)
- You want a configuration file option for overriding built-in default values for your scans
| feroxbuster | gobuster | ffuf | |
|---|---|---|---|
| fast | ✔ | ✔ | ✔ |
| easy to use | ✔ | ✔ | |
| blacklist status codes (in addition to whitelist) | ✔ | ✔ | |
| allows recursion | ✔ | ✔ | |
| can specify query parameters | ✔ | ✔ | |
| SOCKS proxy support | ✔ | ||
| multiple target scan (via stdin or multiple -u) | ✔ | ✔ | |
| configuration file for default value override | ✔ | ✔ | |
| can accept urls via STDIN as part of a pipeline | ✔ | ✔ | |
| can accept wordlists via STDIN | ✔ | ✔ | |
| filter by the response size | ✔ | ✔ | |
| auto-filter wildcard responses | ✔ | ✔ | |
| performs other scans (vhost, dns, etc) | ✔ | ✔ | |
| time delay/rate limiting | ✔ | ✔ | |
| huge number of other options | ✔ |
Use

Example
Multiple Values
Options that take multiple values are very flexible. Consider the following ways of specifying extensions:
./feroxbuster -u http://127.1 -x pdf -x js,html -x php txt json,docx
The command above adds .pdf, .js, .html, .php, .txt, .json, and .docx to each url
All of the methods above (multiple flags, space-separated, comma-separated, etc…) are valid and interchangeable. The same goes for urls, headers, status codes, queries, and size filters.
Include Headers
./feroxbuster -u http://127.1 -H Accept:application/json "Authorization: Bearer {token}"
IPv6, non-recursive scan with INFO-level logging enabled
./feroxbuster -u http://[::1] --norecursion -vv
Read urls from STDIN; pipe only resulting urls out to another tool
cat targets | ./feroxbuster --stdin --quiet -s 200 301 302 --redirects -x js | fff -s 200 -o js-files
Proxy traffic through Burp
./feroxbuster -u http://127.1 --insecure --proxy http://127.0.0.1:8080
Proxy traffic through a SOCKS proxy
./feroxbuster -u http://127.1 --proxy socks5://127.0.0.1:9050
Pass auth token via a query parameter
./feroxbuster -u http://127.1 --query token=0123456789ABCDEF
Changelog v2.10
- Adds server and client certificate management; enables mTLS by @lavafroth in #892
--server-certs--client-cert--client-key
Download
Copyright (c) 2020 epi