Froxlor Web Hosting Control Panel Vulnerable to Remote Compromise (CVE-2024-34070)
A critical vulnerability (CVE-2024-34070) has been discovered in Froxlor, a popular open-source web hosting control panel. This flaw, rated 9.7 on the CVSS severity scale, could allow an unauthenticated attacker to completely take over a Froxlor instance, potentially leading to data theft, service disruption, or further attacks on hosted websites.
What is the Vulnerability?
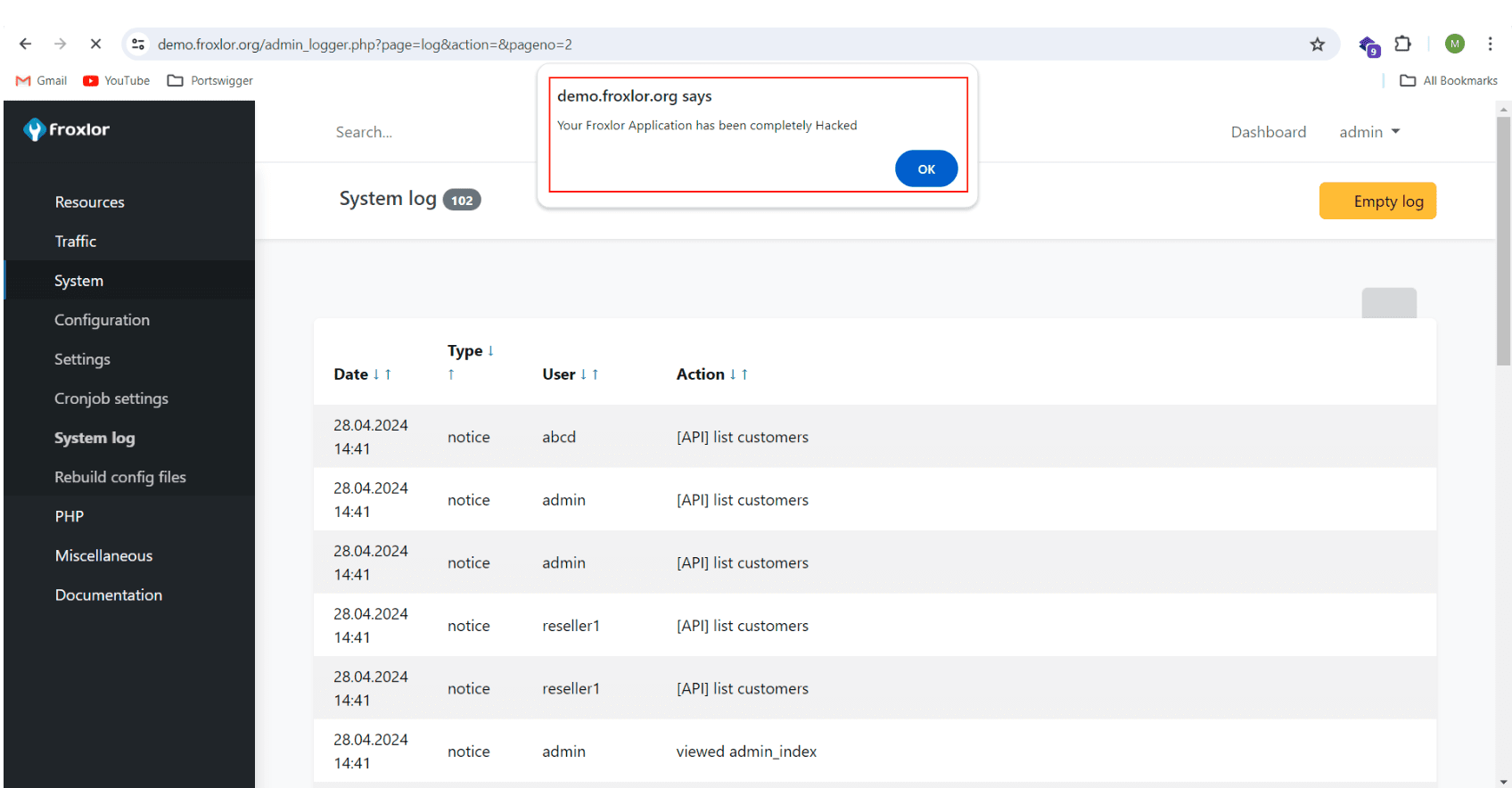
CVE-2024-34070 exposes a Stored Blind Cross-Site Scripting (XSS) flaw in Froxlor’s Failed Login Attempts Logging Feature. This type of vulnerability occurs when user inputs, which are not properly sanitized, are stored on the server. These inputs can then execute malicious scripts when accessed by other users. In this specific case, an unauthenticated user can inject harmful scripts through the loginname parameter during a login attempt. These scripts are later executed when an administrator views them in the System Logs.

XSS payload Executed
The vulnerability exploits the application’s reliance on an XSS sanitization library, which was circumvented using data binding and interpolation features of Vue.js. The attackers crafted a payload that, when executed, covertly adds a new administrator account under the attacker’s control, thus compromising the entire application.
Who is Affected?
All Froxlor versions prior to 2.1.9 are vulnerable. Server administrators using Froxlor are strongly urged to update immediately to the patched version (2.1.9) to mitigate this critical risk.
Impact and Potential Consequences:
- Complete System Compromise: An attacker gaining administrative access could perform any action within the Froxlor panel, including:
- Stealing sensitive user data
- Modifying website content
- Disrupting services
- Planting further malware
- Data Breach: Compromised servers may expose user credentials, session tokens, or other personally identifiable information (PII) to attackers.
- Website Defacement: Attackers could deface or modify websites hosted on the compromised server.
Discovery and Mitigation:
The vulnerability was discovered by security researcher Umer Adeem Cheema. Froxlor has promptly released version 2.1.9, which addresses the flaw. In addition to updating, administrators should also review system logs for any suspicious activity.
Recommendations:
- Update Immediately: Apply the Froxlor update to version 2.1.9 without delay.
- Review Logs: Check system logs for any unauthorized logins or unusual activity.
- Implement Additional Security Measures: Consider enabling two-factor authentication (2FA) for Froxlor administrators and implementing web application firewalls (WAFs) to provide an additional layer of protection.