FROZEN#SHADOW Campaign: The Stealthy Advance of SSLoad Malware and Cobalt Strike
In a sophisticated and deeply troubling cyber campaign, dubbed FROZEN#SHADOW, threat actors have leveraged the relatively unknown SSLoad malware along with Cobalt Strike and ScreenConnect remote monitoring and management (RMM) software to orchestrate a comprehensive takeover of network domains. A new analysis by Securonix Threat Research (STR) reveals their insidious strategy.
The Inception of the Attack
SSLoad, serving as the primary attack vector, infiltrated systems via phishing email campaigns, distributing links that directed unsuspecting users to download a JavaScript file. This seemingly innocuous file was a mere facade for what was essentially a gateway into the victim’s system, leading to the deployment of multiple payloads and backdoors to maintain persistence and evade detection.
Deceptive Simplicity: The Entry Point
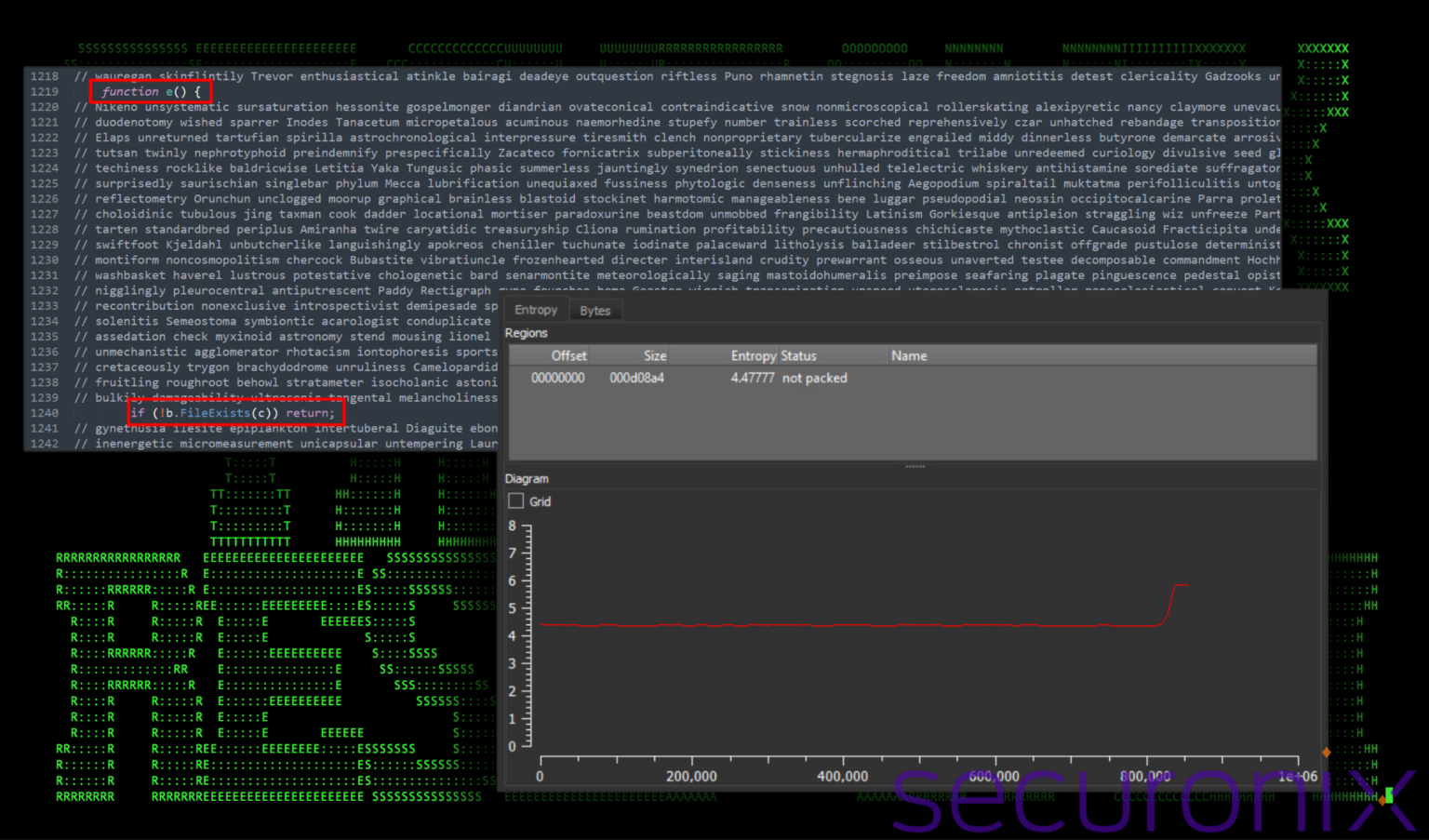
JavaScript obfuscation and entropy (out_czlrh.js) | Image: STR
The initial stage of the malware’s entry was marked by an ingeniously simple JavaScript, “out_czlrh.js”. Hidden beneath layers of obfuscation—massive comment blocks filled with nonsensical words—this script performed critical yet basic functions, setting the stage for further exploitation. The file utilized ActiveXObject instances and Windows Management Instrumentation (WMI) for executing operations on network drives and the local file system.
RMM Software and Cobalt Strike: A Dual Threat
As the campaign progressed, the attackers installed RMM software to achieve a deeper integration into the systems. Cobalt Strike, a tool often used for its robust capabilities in creating secure tunnels to control compromised machines, played a pivotal role. It facilitated the execution of a malicious MSI file that mimicked the behavior of the BazarBackdoor, a malware often used to deploy ransomware and perpetrate data theft.
Network and Domain Takeover
The ultimate objective of FROZEN#SHADOW was the complete domain takeover. By deploying Cobalt Strike beacons and using RMM software, the attackers could navigate laterally across the network, gathering critical information and escalating their privileges silently. They manipulated the domain environment skillfully, creating new admin accounts and executing commands that gave them unfettered access to sensitive areas of the network.
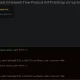
The Lethal Payload: SSLoad Malware

SSLoad DDL file details | Image: STR
The SSLoad malware, downloaded via Cobalt Strike, was particularly insidious. It embedded itself deeply within the system, masquerading as benign software while performing malevolent activities like data harvesting and credential theft. This malware’s effectiveness was significantly enhanced by its ability to remain under the radar, evading traditional detection methods thanks to its sophisticated obfuscation techniques.
Conclusion
The FROZEN#SHADOW campaign serves as a stark reminder of the dangers posed by cyber threats that exploit both the weaknesses in human psychology (through phishing) and the vulnerabilities in system architectures. The integration of legitimate tools in malware attacks complicates the detection and mitigation processes, making it imperative for cybersecurity defenses to be as dynamic and adaptive as the threats they aim to thwart.
For organizations worldwide, this campaign underscores the critical need for advanced security measures, continuous monitoring, and robust defensive strategies to protect against increasingly sophisticated cyber threats.