Gentoo publishes GitHub repository intrusion event report
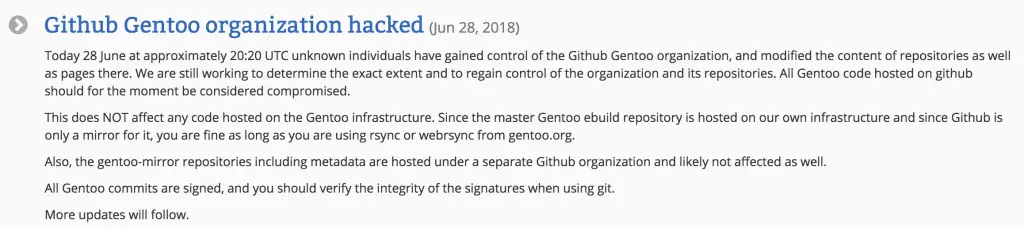
Previously we reported that GitHub repository for Gentoo Linux was compromised, intended to delete all files. Gentoo Linux’s Github repository was hacked on the evening of June 28 and successfully gained control of the organisation. The attacker tampered with the contents of the repository and the page and replaced the files in portage and musl-dev trees with malicious ebuild files, intent to delete all files on the repository. After the Gentoo developer found the problem, an alert email was sent, and the Gentoo GitHub organisation permissions were frozen.
After that, Gentoo posted some announcements on the official website explaining the progress of the incident. Until five days after July 3, Gentoo officially marked the incident as resolved, malicious submissions and contaminated files were processed, and the Gentoo GitHub organisation was re-unlocked. Gentoo also posted a detailed report on the entire incident on its website and said that the evidence gathered indicates that the root cause of the incident is that the password scheme they use is too simple, and disclosure on a site makes it easy for an attacker to guess. The passwords on other unrelated pages cause the attacker to obtain the password and access rights of the organisation administrator.
“Malicious content available
Initial clones of these repositories during these time intervals will have malicious content. Gentoo recommends recreating these from a new clone if you cloned during this period.
- gentoo/gentoo: (2018-06-28 20:38 – 2018-06-29 06:58)
- gentoo/musl: (2018-06-28 20:56 – 2018-06-29 06:59)
- gentoo/systemd: (2018-06-28 21:07 – 2018-06-29 06:57)
Root Cause
The attacker gained access to a password of an organization administrator. Evidence collected suggests a password scheme where disclosure on one site made it easy to guess passwords for unrelated webpages.”