GHOSTPULSE Evolves: Malware Now Hides in Image Pixels, Evading Detection

Elastic Security Labs has recently uncovered a significant evolution in the tactics of the GHOSTPULSE malware family, also known as HIJACKLOADER or IDATLOADER. In their latest report, Elastic Security Labs reveals how this malware has shifted from using the IDAT chunk of PNG files to hiding its payload within the pixel structure itself. This pixel-based algorithm represents a new level of deception, making detection and extraction even more challenging for cybersecurity professionals.
Since its discovery in 2023, GHOSTPULSE has continuously evolved to evade detection. In its earlier versions, the malware hid its encrypted configuration within the IDAT chunk of PNG files, which it would parse to retrieve the malicious payload. However, the latest version of the malware has introduced a pixel-level deception technique. As Elastic Security Labs explains, “The malware constructs a byte array by extracting each pixel’s RED, GREEN, and BLUE (RGB) values sequentially using standard Windows APIs from the GdiPlus(GDI+) library.”
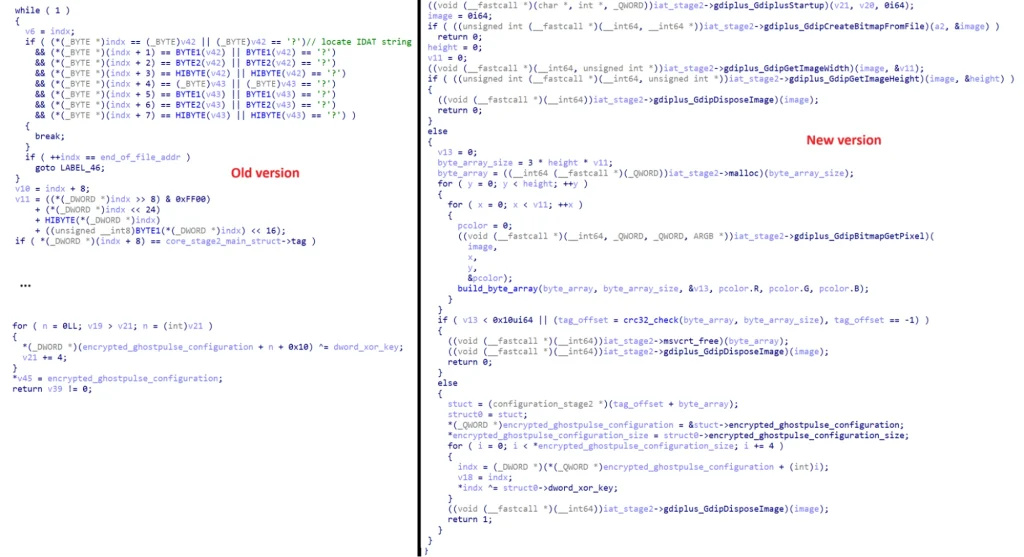
Pseudocode code comparison between old and new algorithm | Image: Elastic Security Labs
By embedding malicious data directly within the pixel values, GHOSTPULSE avoids detection mechanisms that rely on analyzing file structure or headers. The malware then decrypts the configuration using a CRC32 hash and an XOR key embedded within the pixel data. This approach allows GHOSTPULSE to hide its payload in a seemingly innocuous image, making it much harder to detect.
The new version of GHOSTPULSE not only features advanced hiding techniques but also a more streamlined delivery method. Unlike earlier versions, which relied on multi-file packages, the latest iteration of the malware now uses a single compromised executable that contains a large PNG file within its resource section. This PNG file holds the encrypted configuration and payload, removing the need for separate files.
GHOSTPULSE campaigns often employ creative social engineering tactics to trick users into executing the malware. In some cases, victims are lured into completing a fake CAPTCHA, which, instead of validating their identity, instructs them to run specific Windows keyboard shortcuts. These shortcuts trigger a malicious PowerShell script that initiates the GHOSTPULSE infection.
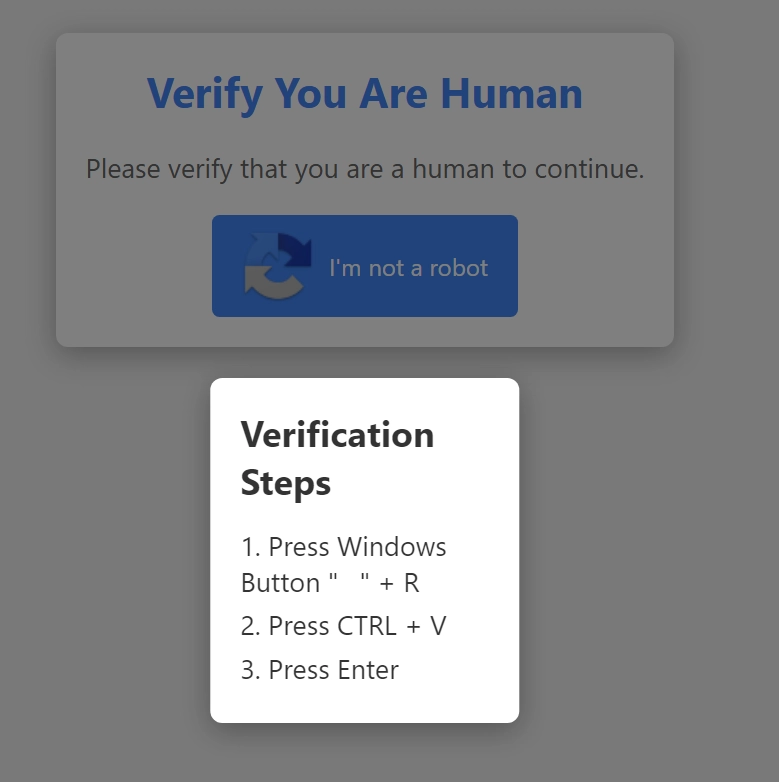
Social engineer lure website | Image: Elastic Security Labs
To address this evolving threat, Elastic Security Labs has updated its detection mechanisms. The original GHOSTPULSE YARA rules, built into Elastic Defend, still effectively prevent the final stage of infection. However, new rules have been developed to detect this pixel-based hiding technique. “The updated sample can be detected using the following YARA rules and will be included with Elastic Defend in a future release,” Elastic Security Labs noted, providing hope that defenders can stay one step ahead of this evolving malware.





