GitHub Search Sabotaged: Malware Hidden in Popular Repositories
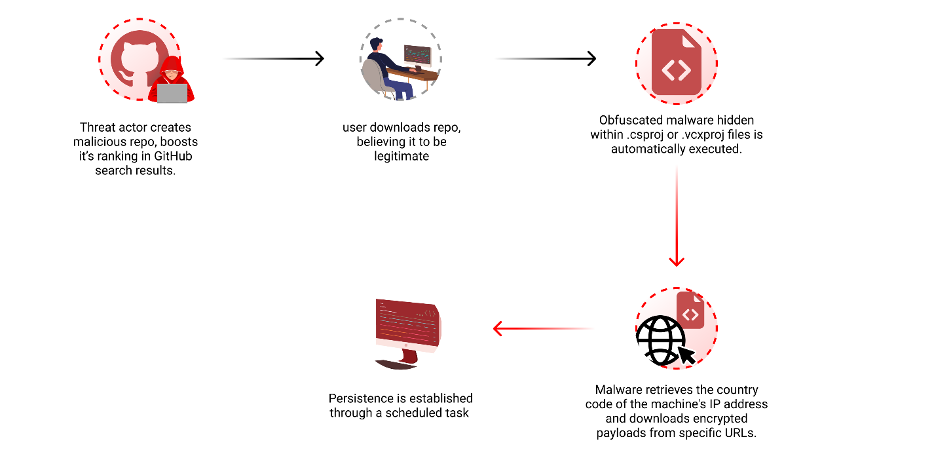
In the ever-evolving landscape of cybersecurity, a new threat has emerged, cleverly exploiting GitHub’s vast open-source ecosystem. Cybercriminals, demonstrating both ingenuity and malice, have initiated a campaign that manipulates GitHub’s search functionality to distribute malware through repositories masquerading as legitimate projects. This report, brought to light by the vigilant analysis of Checkmarx, underscores the sophisticated tactics these threat actors employ to ensnare unsuspecting developers.
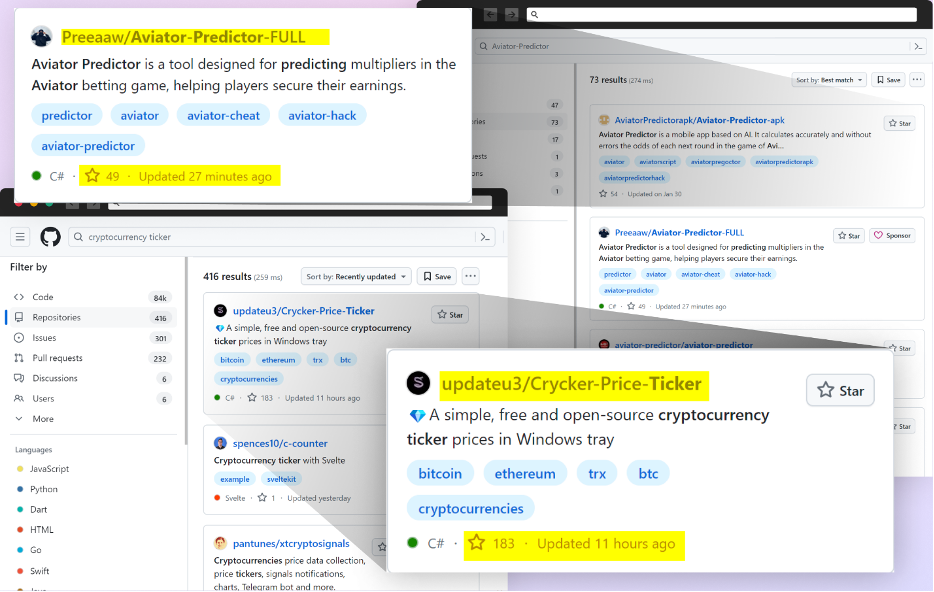
Image: Checkmarx
The essence of this scheme lies in the abuse of GitHub’s search features. Attackers create repositories with appealing names and topics, mimicking popular games, tools, or software, thereby attracting their victims. But the deceit doesn’t end there; through automated updates and the strategic addition of fake stars, these malicious repositories gain undue visibility, tricking users into believing in their authenticity and popularity.
Employing GitHub Actions, the attackers incessantly update these repositories, a facade of activity that significantly boosts their search rankings. These updates, often as trivial as altering a log file, prey on the platform’s algorithms, pushing the repositories to the forefront of search results.
To compound the illusion, attackers deploy fake accounts to star these repositories, fabricating a sense of community endorsement and trustworthiness. This manipulation, albeit more modest in its execution compared to past incidents, effectively amplifies the repositories’ visibility, ensnaring more victims under its guise.
Within these repositories lurks the true danger: malware cleverly concealed within Visual Studio project files (.csproj or .vcxproj). This obfuscation ensures the automatic execution of malicious code upon the building of the project.

Image: Checkmarx
The malware operates by embedding a script in a pre-build event, which then executes a concoction of batch and VBScript files, ultimately running a PowerShell script designed to perform various malicious activities, including downloading and executing further malware based on the victim’s geography. Remarkably, this campaign even tailors its payload to avoid targets in Russia, a nuance that adds another layer of complexity to the threat.
As of April 3rd, the campaign remains active, with the attackers updating their methods to distribute a new form of malware disguised within a bloated executable, designed to evade detection by exceeding the file size limits of many security solutions. This evolution of tactics signifies the attackers’ adaptability and persistence.
The success of this malicious campaign is, unfortunately, evident, with numerous users reporting issues after unknowingly engaging with these repositories. This scenario underscores the critical need for awareness and caution among developers and users alike.





