Global Malware Campaign Exploits Lua in Gaming and Education Sectors
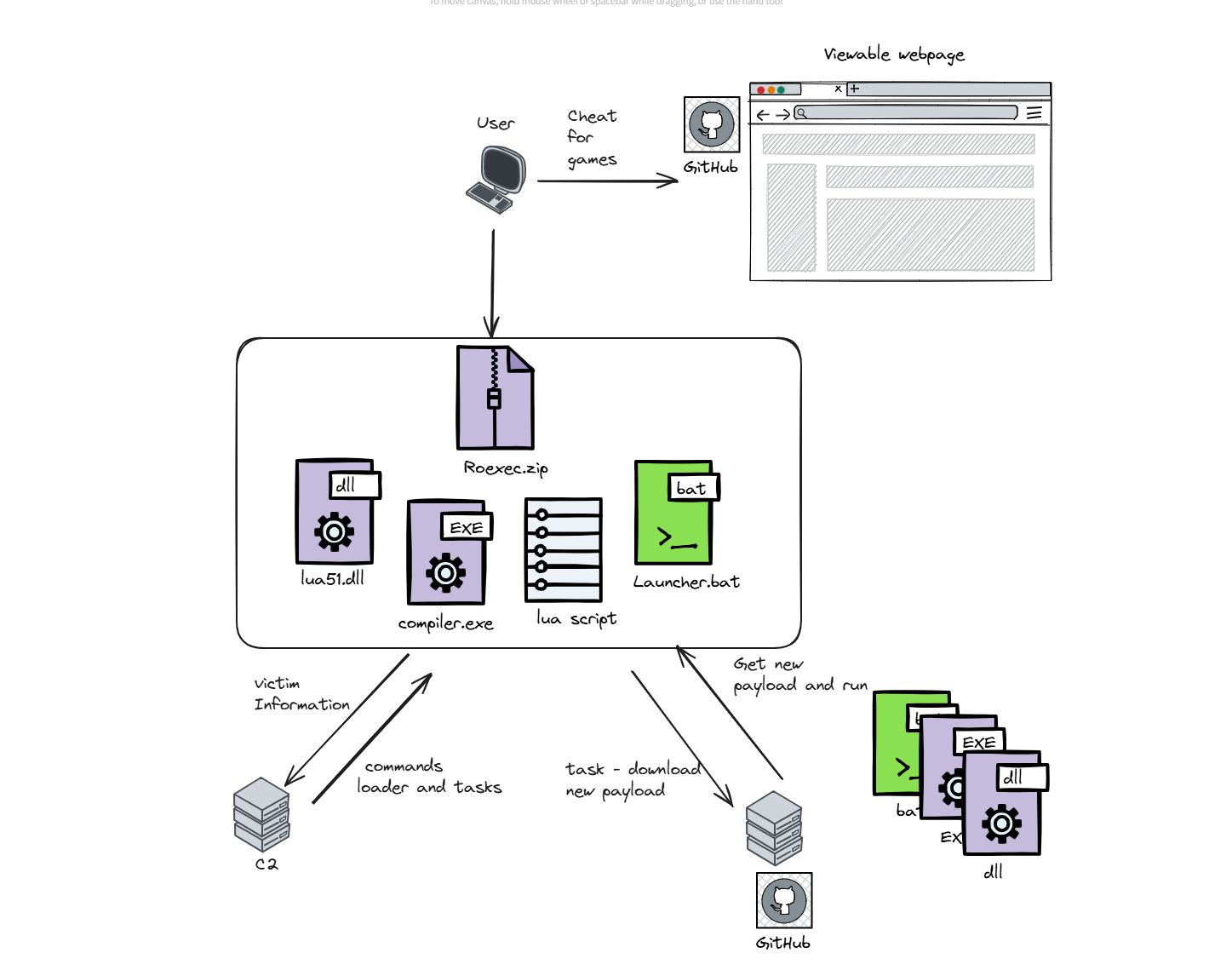
A new wave of malware attacks has been uncovered by Morphisec Threat Labs, targeting the educational sector and gaming communities. According to security researcher Shmuel Uzan, these sophisticated malware variants leverage Lua, a scripting language widely used in game development, to infiltrate systems via platforms like GitHub. The campaign has had a global reach, with infections reported across North America, South America, Europe, Asia, and Australia.
The rise of this malware can be attributed to its exploitation of Lua’s popularity, especially among student gamers using gaming engines like Roblox. According to the report, “Users searching for game cheats often end up downloading files from platforms like GitHub or similar sources.” The attackers take advantage of these cheat-seeking users by embedding malicious Lua scripts within seemingly harmless downloads.
The malware is typically delivered through a ZIP archive, which contains multiple components, including a Lua compiler, Lua DLL file, an obfuscated Lua script, and a batch file. These components work together to execute malicious actions once installed on the victim’s machine. Upon execution, the Lua script establishes communication with a command-and-control (C2) server, sending detailed information about the infected system.
Once the malware is active, the C2 server provides instructions to the infected machine, categorized into two types of tasks: Lua loader tasks and task payloads. The Lua loader tasks maintain persistence and hide processes, while the task payloads focus on downloading additional malware payloads or applying new configurations. The report explains, “Lua loader tasks involve actions such as maintaining persistence or hiding processes,” while the payloads are designed to extend the malware’s capabilities.
To evade detection, the Lua script is obfuscated using the Prometheus Obfuscator, a tool designed to protect the underlying code from reverse engineering. This level of obfuscation makes it difficult for security researchers to analyze and understand the malware’s full functionality. “The script is obfuscated using the Prometheus Obfuscator… making it significantly more difficult for researchers to analyze and understand the code,” Uzan noted in the report.
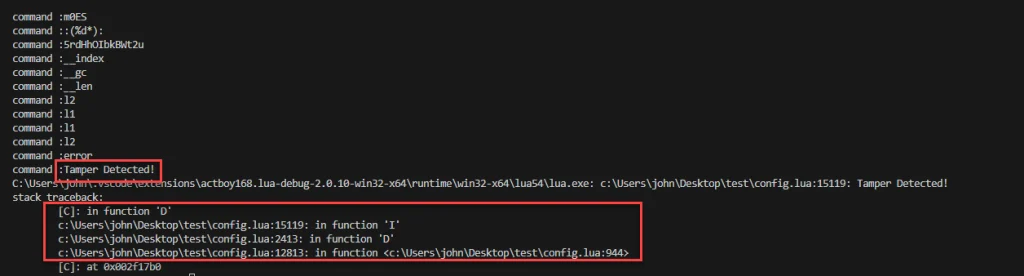
In an effort to thwart researchers from reversing or reformatting the code, the malware incorporates a unique anti-reversing technique that triggers error messages when attempts are made to beautify the obfuscated code. The obfuscator’s functionality includes detecting whether the code has been tampered with by checking the line numbers of error messages generated during execution. If the code has been altered, the malware terminates, displaying a message: “Tamper Detected!”
Beyond obfuscation, the malware also makes use of Lua’s ffi (foreign function interface) library to directly execute C code. This technique allows the attackers to call C functions and use C data structures without needing to write C wrapper code. This integration between Lua and C enhances the malware’s ability to manipulate system-level processes and execute more advanced attacks.
Once the malware has infiltrated the victim’s system, it establishes persistence by creating scheduled tasks and generating random task names. The malware also gathers extensive information about the victim’s machine, including details such as the user’s GUID, computer name, operating system, and network details. It even captures screenshots of the compromised system and sends this data to the attacker’s C2 server.
The report highlights that “the script retrieves the MachineGuid… and sends the adversary C2 the collected data from the computer along with screenshots.” This level of data gathering gives attackers a comprehensive view of the compromised machine, allowing them to tailor subsequent attacks more effectively.
Once the malware has successfully gathered the required data, the C2 server responds with either a blocked message or a JSON response, which provides further instructions for executing tasks or downloading additional payloads. If the server response is blocked, the malware attempts to retrieve a new address from a backup location, such as pastebin.com, ensuring continued communication with the attackers.
Payloads delivered by this malware include Redline Infostealers, a type of malware used to harvest credentials and sensitive information from victims. The report indicates that Redline has gained prominence in the cybercriminal landscape due to its ability to steal valuable data, which is later sold on the dark web. “The harvested credentials from these attacks are sold to more sophisticated groups to be used in later stages of the attack,” Uzan warns.





