GodFather Malware Now Targets 500+ Banking and Crypto Apps
The GodFather malware has expanded its scope, now targeting over 500 banking and cryptocurrency applications across various regions worldwide, according to a report by Cyble Research and Intelligence Labs (CRIL). This latest variant uses sophisticated techniques, including native code implementation and minimal permissions, making it more elusive and dangerous than before.
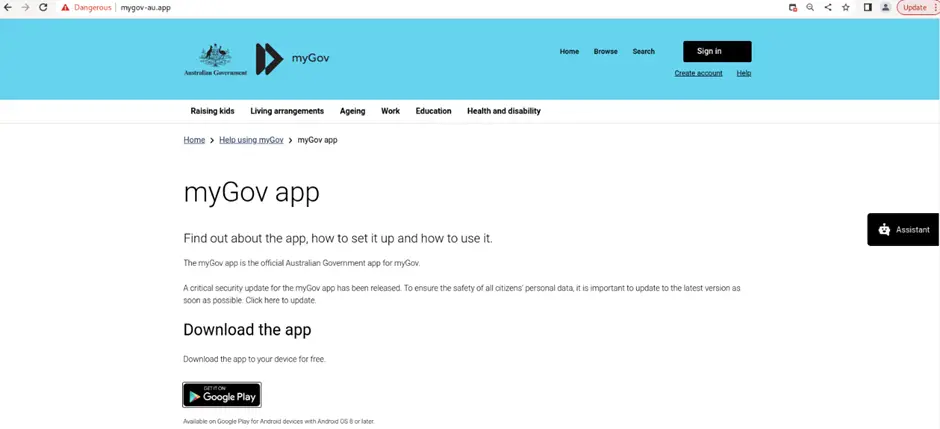
One of the malware’s most notable tactics involves phishing sites. A recent example includes a fake MyGov website—“mygov-au[.]app”—that distributes a malicious APK file disguised as the MyGov application, aimed at stealing banking credentials. “Upon further analysis, this site was found to be distributing a suspicious APK file linked to the GodFather Malware,” CRIL notes. Once installed, this fake app connects to an external URL to track installations, retrieve the device’s IP address, and store this data on the attacker’s server.
The malware also leverages the Accessibility service on Android devices, enabling it to perform tasks like executing gestures, loading injection URLs into WebView, and establishing connections with a command-and-control (C&C) server. In this version, GodFather has shifted from traditional Java to native code, which “implements various malicious capabilities, including loading an injection URL into the WebView, executing automated gestures, establishing connections with the Command and Control (C&C) server, and keylogging.” This transition to native code has made the malware significantly harder to detect and analyze.
Once the malware detects a target application—whether a banking or cryptocurrency app—it closes the legitimate app and loads a fake login page to steal credentials. CRIL’s analysis revealed that “when the user tries to interact with the target application, the malware closes the genuine application. Instead, it loads a fake banking or crypto login URL into the WebView or displays a blank screen,” effectively intercepting the login attempt.
Additionally, GodFather has expanded its geographical reach. Originally targeting users in the United Kingdom, United States, Turkey, Spain, and Italy, it now also targets users in Japan, Singapore, Azerbaijan, and Greece.
The GodFather malware illustrates the increasing sophistication of mobile threats, especially those aimed at financial and cryptocurrency sectors. As CRIL concludes, “With its new automated actions and broader targeting of apps in more countries, this malware poses a growing risk to users worldwide. Staying alert and using strong security practices on mobile devices is essential to avoid falling victim to threats like GodFather.”
Related Posts:
- New Phishing Scam Targets Android Users in India, Researchers Warn
- Turla APT Suspected in “Tiny BackDoor” Campaign Leveraging MSBuild to Evade Detection
- Cybercriminals Escalate Attacks Exploiting Microsoft SmartScreen Flaw (CVE-2024-21412)
- Hackers Fake ChatGPT App to Spread Windows, and Android Malware
- Transparent Tribe & SideCopy: A Dangerous Cyber Alliance Targeting India





