Golddigger and Gigabud Android Banking Trojans: Same Cybercriminal, New Tricks
A recent investigation by Cyble Intelligence and Research Labs (CRIL) has unveiled a significant connection between two prominent Android banking trojans: Golddigger and Gigabud. Evidence suggests they are orchestrated by the same threat actor, who is continually evolving their tactics and expanding their reach.
Golddigger first surfaced in June 2023, targeting users in Vietnam by masquerading as a Vietnamese government entity. Meanwhile, Gigabud, discovered earlier in January 2023, initially focused on users in Thailand, the Philippines, and Peru by impersonating local government entities. What seemed like two separate campaigns now appear to be intertwined, with both malware strains employing overlapping source code and techniques.
CRIL’s recent analysis has confirmed that the same TA behind Golddigger is also responsible for the ongoing Gigabud campaign. This revelation is backed by evidence of shared libraries and modules within the malware, including the strategic use of a native file named “libstrategy.so,” which is crucial for identifying and interacting with user interface elements in targeted banking applications.
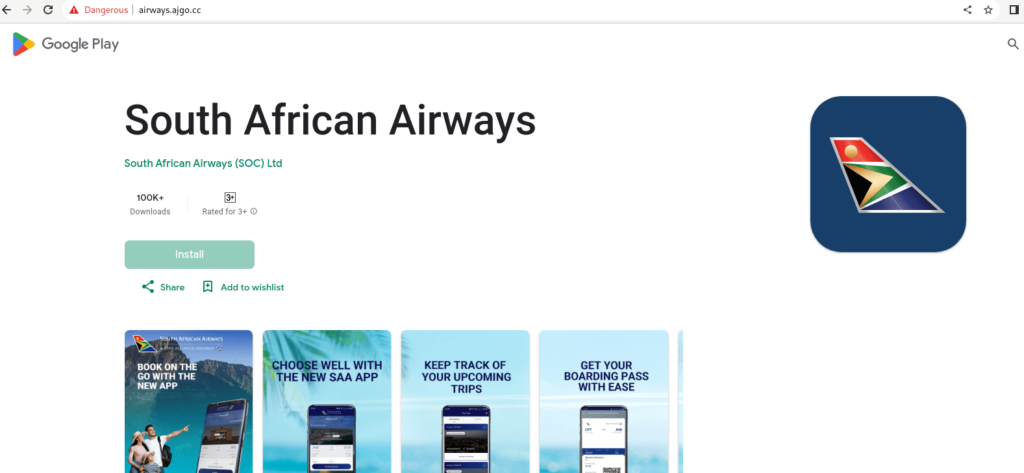
Phishing site distributing fake South African Airways app | Image: CRIL
Initially confined to specific regions, the Gigabud malware has since broadened its reach, now targeting users in Bangladesh, Indonesia, Mexico, South Africa, and Ethiopia. This strategic expansion highlights the TA’s increased sophistication and ambition, as they aim to compromise a wider range of victims across the globe.
One of the key tactics employed by the Gigabud campaign involves the use of phishing sites that replicate legitimate Google Play pages to distribute malicious applications. CRIL identified multiple phishing sites impersonating South African Airways and Ethiopian Airlines, designed to deceive users into downloading the malware. Similar schemes have been observed in Mexico and Indonesia, where Gigabud masquerades as a Mexican bank and an Indonesian tax government entity, respectively.
Further analysis of the Gigabud malware reveals that it utilizes the Virbox packer, a technique also employed by Golddigger, to obfuscate its true nature and evade detection by security solutions. This packer conceals the malware’s malicious intent, making it more challenging for traditional defenses to identify and neutralize the threat.
CRIL’s investigation also uncovered a notable increase in the number of API endpoints used by the latest Gigabud samples. The malware now features 32 API endpoints, a substantial upgrade from the 11 endpoints found in earlier versions. This expansion reflects the TA’s ongoing efforts to enhance their malware’s capabilities and adapt to new environments.
One of the most striking similarities between Gigabud and Golddigger is the use of the “libstrategy.so” library and its Java counterpart, “com.strategy.utils.” This library is critical for the malware’s operation, allowing it to parse UI elements of targeted banking applications and lock pattern windows on various mobile devices. The malware then uses this information to execute malicious actions, such as exfiltrating financial data or locking the infected device.
Related Posts:
- Google Chrome 127 Arrives with Security Patches: What Users Need to Know
- Western Digital suffers network security incident
- New Phishing Scam Targets Android Users in India, Researchers Warn
- Turla APT Suspected in “Tiny BackDoor” Campaign Leveraging MSBuild to Evade Detection
- Cybercriminals Escalate Attacks Exploiting Microsoft SmartScreen Flaw





