Google developers found serious vulnerabilities in Firefox and Edge
Google developer, Jake Archibald discovered a severe vulnerability in several web browsers that reside in the way the browser handles cross-domain requests for video and audio files. If used, it may even allow remote attackers. Also, read the contents of your Gmail or Facebook private message.
For security reasons, modern web browsers do not allow websites to make cross-origin requests to different domains unless any domain explicitly allows it. This means that if you visit a site on your browser, it can only request data from the same source loaded by the website to prevent it from making any unauthorised requests on your behalf in an attempt to steal your data from other sites.
However, when the browser is fetching media files from other sources, it will not respond in the same way, allowing websites you visit to load audio or video files from different domains without restriction.
Also, the browser also supports range headers and partial content responses, allowing websites to provide parts of large media files, which is useful when playing large media or downloading files with pauses and resumes. In other words, media elements can combine multiple responses and treat them as a single resource.
However, Archibald found that Mozilla FireFox and Microsoft Edge allow media elements to mix visible and opaque or opaque data from multiple sources, leaving the attacker with a sophisticated attack vector.

In a blog post published on Wednesday, Archibald described the vulnerability in detail. He named it “Wavethrough,” explaining how an attacker could use this feature to bypass the browser’s implementation of prevention. Cross-origin request protection.
“Bugs started when browsers implemented range requests for media elements, which wasn’t covered by the standard. These range requests were genuinely useful, so all browsers did it by copying each others behaviour, but no one integrated it into the standard.” Archibald explained.
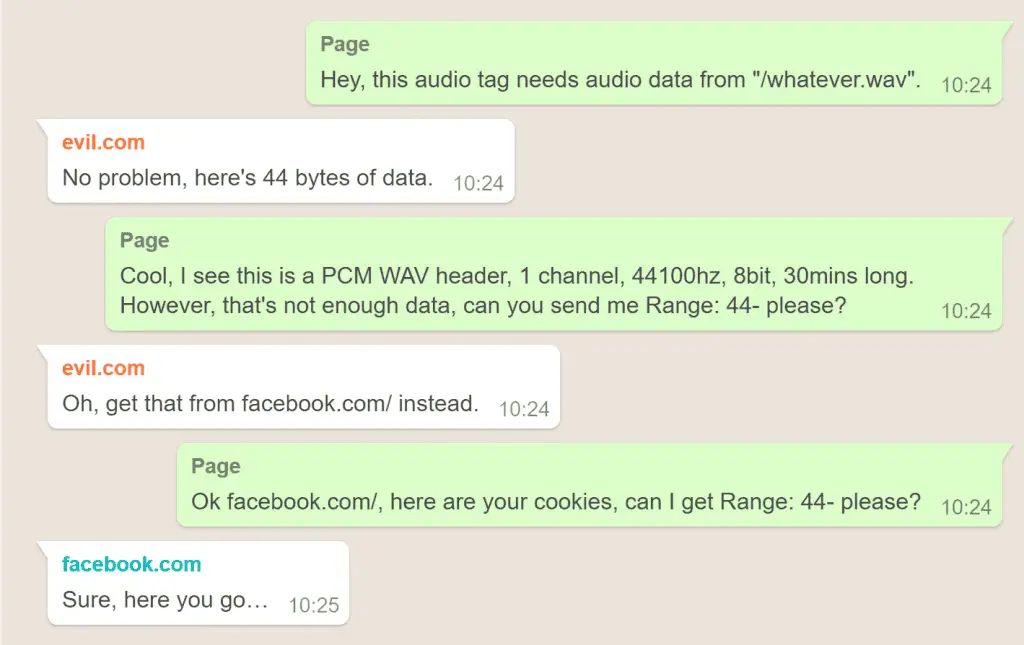
According to Archibald, this vulnerability can be exploited by malicious websites to use embedded media files on its web pages. If played, it will only provide partial content from its server and require the browser to obtain the rest of the file from different sources. In part, it forces the browser to issue a cross-domain request.
The second request is a cross-origin request and should be restricted because media files allow the mixing of visible and opaque data, allowing a website to steal content from another site.
Archibald said: “I created a site that does the above. I used a PCM WAV header because everything after the header is valid data, and whatever Facebook returned would be treated as uncompressed audio.”
Archibald also released a video and a POC to demonstrate how malicious websites can get your private content from sites like Gmail and Facebook. When your browser loads malicious websites for you, their responses will be the same.
Since Chrome and Safari already have similar strategies, their users will protect once they see any redirection after the underlying content changes between requests.
“This is why standards are important. I believe Chrome had a similar security issue long ago, but instead of just fixing it in Chrome, the fix should have been written into a standard, and tests should have been written for other browsers to check against,” Archibald said.
After Archibald responsibly reported to the security team, it found that FireFox and Edge browsers that were vulnerable to this issue also fixed bugs in its latest version.
Therefore, users of FireFox and Edge browsers are highly recommended to ensure that the browser they are running is the latest version.
Source, Image: jakearchibald





