Google Impersonation Scams: Cybersecurity Expert Reveals Alarming Tactics

Cybersecurity expert Brian Krebs has uncovered alarming new details about the dangers posed by sophisticated phishing campaigns. In his blog, Krebs reveals the stories of two victims, Adam Griffin and Tony, who together lost millions of dollars in cryptocurrency to social engineering attacks that combined technical precision and emotional manipulation.
Adam Griffin, a firefighter and battalion chief from Seattle, became the victim of a convincing phishing scam in May 2024. A scammer, posing as a representative from Google, used a real Google phone number and sent security alerts from the legitimate google.com domain. As Krebs explains, Griffin received a call warning of suspicious activity on his Gmail account. Moments later, a Google prompt appeared on his phone asking, “Is it you trying to recover your account?” Believing the caller to be genuine, Griffin clicked “yes.”
“As soon as I clicked yes, I gave them access to my Gmail, which was synched to Google Photos,” Griffin recalled. Unbeknownst to him, the thieves were targeting an image stored in his Google Photos containing the seed phrase for his cryptocurrency wallet. Within minutes, they drained $450,000 worth of funds from his Exodus wallet.
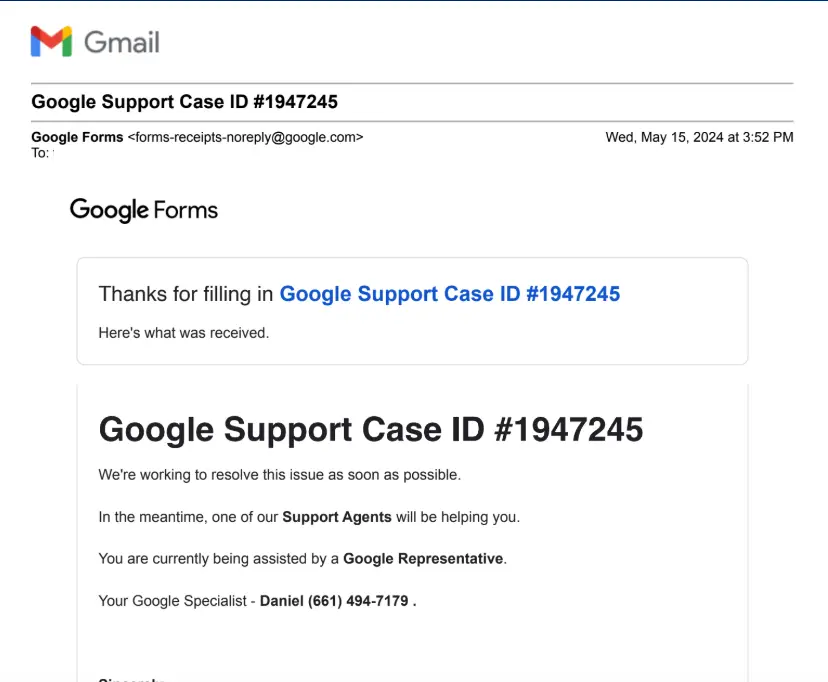
Adam Griffin and Tony said they received the same Google Support Case ID number in advance of their thefts | Source: Brian Krebs
Tony, another victim featured in Krebs’ report, lost 45 bitcoins—equivalent to $4.7 million at the time—to a similarly orchestrated scam. Distracted while caring for his young children, Tony fell prey to a call from a fake Google representative who convinced him to confirm account recovery via a phishing prompt. In a devastating turn of events, the attackers then used his credentials to access a phishing site mimicking Trezor, a hardware wallet provider, where Tony inadvertently entered his cryptocurrency seed phrase.
The attackers exploited legitimate tools, such as Google Forms and Google Assistant, to craft highly convincing phishing messages. As Krebs notes, “The attackers are taking advantage of the fact that the emails are being sent out directly by Google Forms (from the google.com domain).” This tactic bypasses traditional email filtering solutions, increasing the likelihood of success.
Once the victims were hooked, the scammers escalated the emotional pressure. Griffin and Tony both received calls from other impersonators, including fake representatives from Coinbase and Trezor, who used fear and urgency to manipulate their decisions.
“Even security-conscious people tend to underestimate the complex and shifting threat from phone-based phishing scams, but they do so at their peril,” Krebs warns.
Both Griffin and Tony have since become outspoken advocates for stronger security practices. Griffin admitted, “I know I definitely made mistakes, but I also know Google could do a lot better job protecting people.”
Krebs advises users to adopt robust security measures to guard against similar attacks. Recommendations include:
- Disable Google Authenticator cloud sync: By default, one-time codes are accessible through Gmail accounts, making them vulnerable if the account is compromised.
- Use physical security keys: These phishing-resistant tools provide an additional layer of defense.
- Verify suspicious calls: “Hang up, look up, and call back,” Krebs emphasizes. Always contact companies through their verified phone numbers.
- Strengthen passwords: Use unique, long passphrases for email accounts and avoid reusing old passwords.
For those managing significant cryptocurrency holdings, Krebs suggests enrolling in Google’s Advanced Protection Program, which offers heightened security features.
The tales of Griffin and Tony serve as stark reminders of the high stakes in the digital age. As attackers refine their methods, individuals must remain vigilant, adopting proactive security measures to safeguard their digital identities and assets. In the words of Brian Krebs, “Understand that your email credentials are more than likely the key to unlocking your entire digital identity.”





