Government IDs and Facial Recognition: A New Phishing Threat
A recent report by Harsh Patel and Brandon Cook from the Cofense Phishing Defense Center highlights a dangerous new tactic aimed at exploiting online users by combining phishing for government IDs with facial recognition video capture. This sophisticated attack not only jeopardizes personal security but also undermines public trust in the digital infrastructure we rely on daily.
The phishing scheme begins with an email claiming to require urgent identity verification for account continuity. According to Patel and Cook, “Loss of features or access to services is a popular way to lure users into submitting information.” This creates a sense of urgency, leading victims to click on malicious links without scrutinizing their authenticity.

Email Body | Image: Cofense
Once the victim clicks the link, they are greeted by a seemingly legitimate CAPTCHA page designed to lower suspicion. As Patel and Cook describe, “This CAPTCHA-style page is less common, making it an interesting and deceptive tactic.” The added assurance text, such as “No need to fear—this is safe and secure,” further manipulates victims into trusting the process.
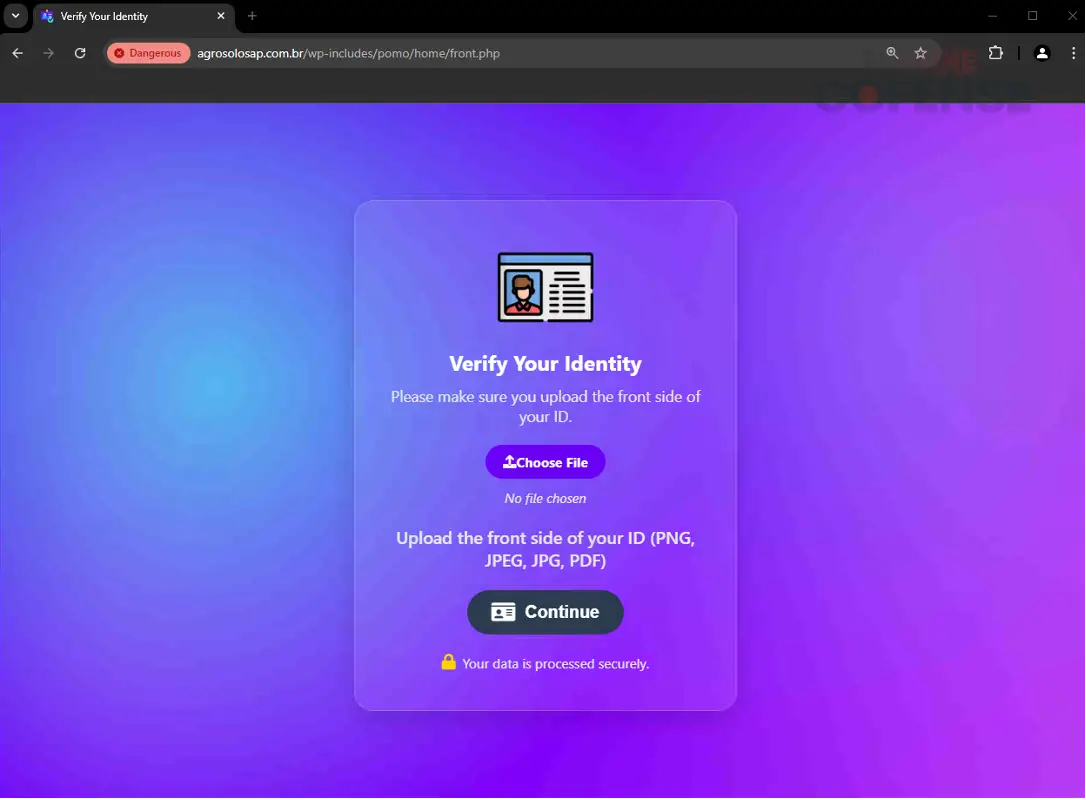
Following the CAPTCHA, the user is directed to a fake identity verification page where they are asked to upload government-issued identification documents. This page’s design, while simplistic, is accompanied by telltale signs of fraud, including unrelated domain names and vague messaging.

Country and Document Type | Image: Cofense
The final step in this attack involves biometric data theft. Users are instructed to engage in a “Selfie check,” mimicking legitimate facial recognition systems. The inclusion of a “Start Recording” button marks a shift towards more sophisticated phishing techniques. Patel and Cook warn, “The potential for copying or spoofing biometric data through malicious websites raises even greater concerns.”
This method represents a dangerous evolution in phishing attacks. By combining traditional identity theft techniques with biometric data capture, cybercriminals gain access to highly sensitive information that is difficult to change or revoke. The report emphasizes the risks posed by advancements in AI technology, which criminals can use to manipulate and exploit stolen biometric data further.
The report stresses the importance of recognizing phishing red flags. These include generic greetings, suspicious links, and grammatical errors in emails. It also underscores the necessity of critical thinking when faced with unusual requests for personal information. As Patel and Cook note, “Recognizing red flags in emails… can help prevent identity theft and safeguard personal information in an increasingly digital world.”





