GTPDOOR: The Shape-Shifting Threat Lurking in Telco Networks
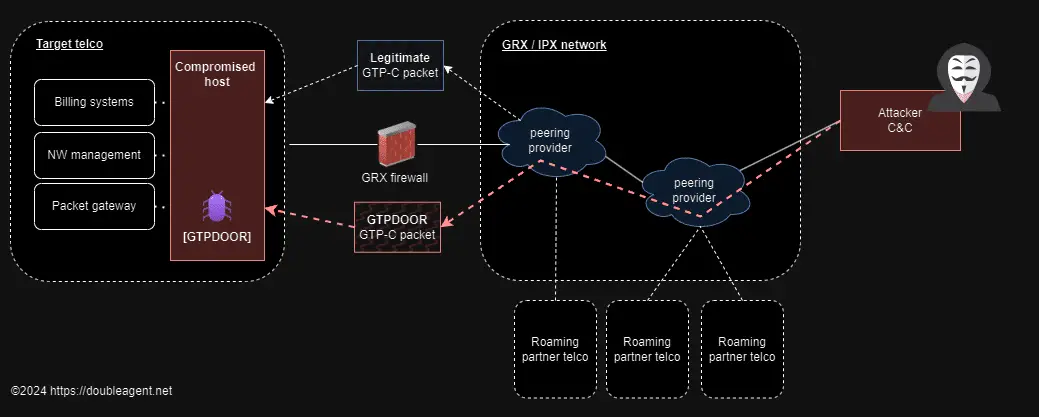
A new Linux-based malware, christened GTPDOOR, has emerged with a cunning strategy to infiltrate the heart of telecommunication networks – the GRX (GPRS Roaming Exchange). By harnessing the GPRS Tunneling Protocol (GTP-C), usually confined to legitimate network signaling, GTPDOOR aims to evade detection and gain a foothold within these sensitive environments.

Image: haxrob
A Novel Approach to Network Infiltration
GTPDOOR’s deployment strategy is as cunning as it is effective. It targets systems within the telco network, leveraging the GTP-C protocol to blend its malicious traffic with the normal ebb and flow of data. This camouflage enables it to exploit open and exposed ports that are already permitted within the GRX network, ensuring its activities remain undetected.
The malware’s modus operandi involves establishing persistence within the roaming exchange network, then accessing compromised hosts by dispatching GTP-C Echo Request messages laden with a malicious payload. This approach not only facilitates remote code execution but also allows GTPDOOR to signal its presence through the transmission of arbitrary TCP packets, with its beacon response ingeniously concealed within a TCP header flag.
Named by the security researcher Haxrob, GTPDOOR employs a “port knocking / magic packet” technique reminiscent of its predecessor, BPFDOOR. However, it distinguishes itself by explicitly utilizing GTP-C echo request/response messages without relying on BPF/pcap filters. This specificity enables it to intercept packets directly through raw sockets, filtering on UDP and GTP header values with meticulous precision.
Attributed to the likes of UNC1945 (Mandiant) and LightBasin (CrowdStrike), GTPDOOR is a testament to the evolving tactics of threat actors. Unlike traditional methods that exploit the GTP protocol for encapsulating traffic, GTPDOOR harnesses specific GTP-C signalling messages, adding an extra layer of complexity to its operations.
Among its arsenal of capabilities, GTPDOOR excels in listening for “magic” wakeup packets, executing commands from these packets to facilitate a reverse shell functionality, and covertly probing external networks to elicit responses. Its use of a simple XOR cipher for authenticating and encrypting message contents further enhances its stealth capabilities. Moreover, the ability to change its process name and blend into the environment as a benign syslog process exemplifies its chameleon-like adaptability.
Connections and Insights
GTPDOOR’s potential for deployment is vast, given the interconnected nature of telecommunication networks. It could be strategically placed within systems requiring direct connectivity to the GRX network, such as SGSN, GGSN, or P-GW, to name a few. These entry points provide a direct conduit into a telco’s core network, presenting a golden opportunity for this malware to exert its influence.
In essence, GTPDOOR does not merely infiltrate systems; it weaves itself into the fabric of the network, operating undetected and unchallenged. Its existence underscores the need for heightened vigilance and advanced security measures within the telecommunications sector.





