Hacker sells Telus source code, and staff info for $50,000
Telus is one of the three major telecommunications giants in Canada, headquartered in Vancouver, British Columbia. Telus is Canada’s fastest-growing telecommunications company, with approximately 60,000 employees serving millions of customers. According to theregister, Telus is currently investigating a data breach incident involving employee information and source code.
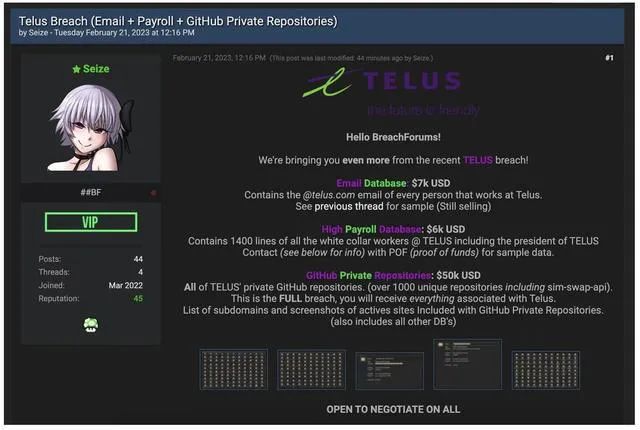
The incident began when a hacker (known as Seize) claimed on the BreachForums forum that they had obtained sensitive data from Telus and were publicly selling it. In one post, the hacker provided 76,000 employee emails and internal information related to Telus employees, with the price currently undecided and negotiable, and will only be sold to one person.

In another post, the hacker is selling a database containing Telus employee emails for $7,000 and a payroll database containing 770 employee records (including information on the Telus president) for $6,000. The most significant item for sale is Telus’s private source code and GitHub repository, priced at $50,000.
In response, Telus spokesperson Richard Gilhooley stated that they are investigating the claim that a small amount of data related to Telus internal source code and some Telus employee information has appeared on the dark web. They can confirm that no data involving any company or retail customers have been discovered in the investigation launched immediately after becoming aware of the incident.
For Telus customers, the biggest concern is the potential losses that could result from the leaked repository, such as SIM card swapping attacks. Typically, this type of attack requires social engineering to deceive telecommunications company employees. After the GitHub repositories including the SIM swap API are leaked, it could be used by criminals to transfer victims’ phone numbers to devices controlled by the attacker, intercept SMS verification codes, and hijack the victims’ other online accounts.





