hakoriginfinder: discovering the origin host behind a reverse proxy
hakoriginfinder
Tool for discovering the origin host behind a reverse proxy. Useful for bypassing WAFs and other reverse proxies.
How does it work?
This tool will first make an HTTP request to the hostname that you provide and store the response, then it will make a request to every IP address that you provide via HTTP (80) and HTTPS (443), with the Host header set to the original host. Each HTTP response is then compared to the original using the Levenshtein algorithm to determine similarity. If the response is similar, it will be deemed a match.
Install
go install github.com/hakluke/hakoriginfinder@latest
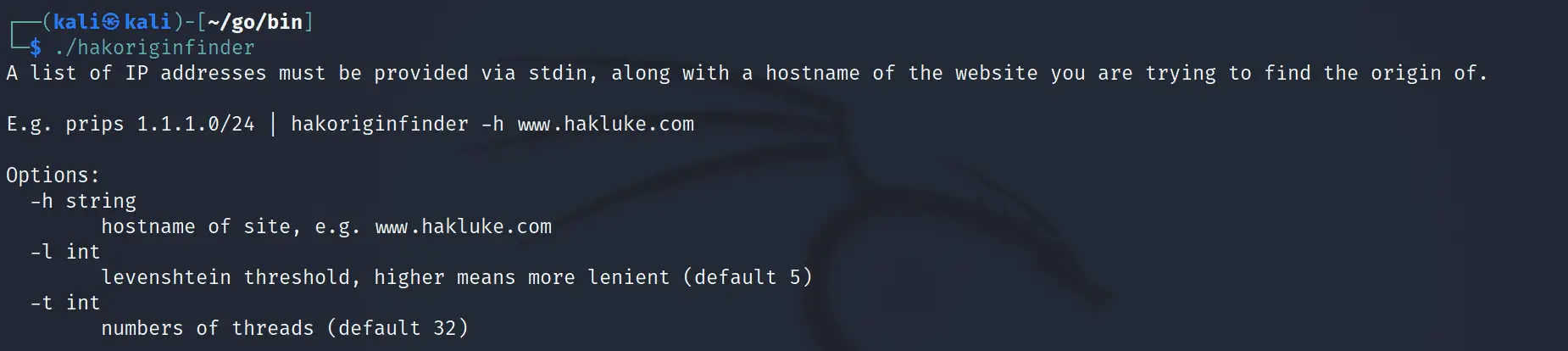
Usage

Provide the list of IP addresses via stdin, and the original hostname via the -h option. For example:
prips 93.184.216.0/24 | hakoriginfinder -h example.com
You may set the Levenshtein distance threshold with -l. The lower the number, the more similar the matches need to be for it to be considered a match, the default is 5.
The number of threads may be set with -t, default is 32.
The hostname is set with -h, there is no default.
Output
The output is 3 columns, separated by spaces. The first column is either “MATCH” or “NOMATCH” depending on whether the Levenshtein threshold was reached or not. The second column is the URL being tested, and the third column is the Levenshtein score.
Output example
Source: https://github.com/hakluke/





