HawkScan v2.6 releases: Security Tool for Reconnaissance and Information Gathering on a website
HawkScan
Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x)
This script uses “WafW00f” to detect the WAF in the first step.
This script uses “Sublist3r” to scan subdomains.
This script uses “waybacktool” to check in the waybackmachine.
Features
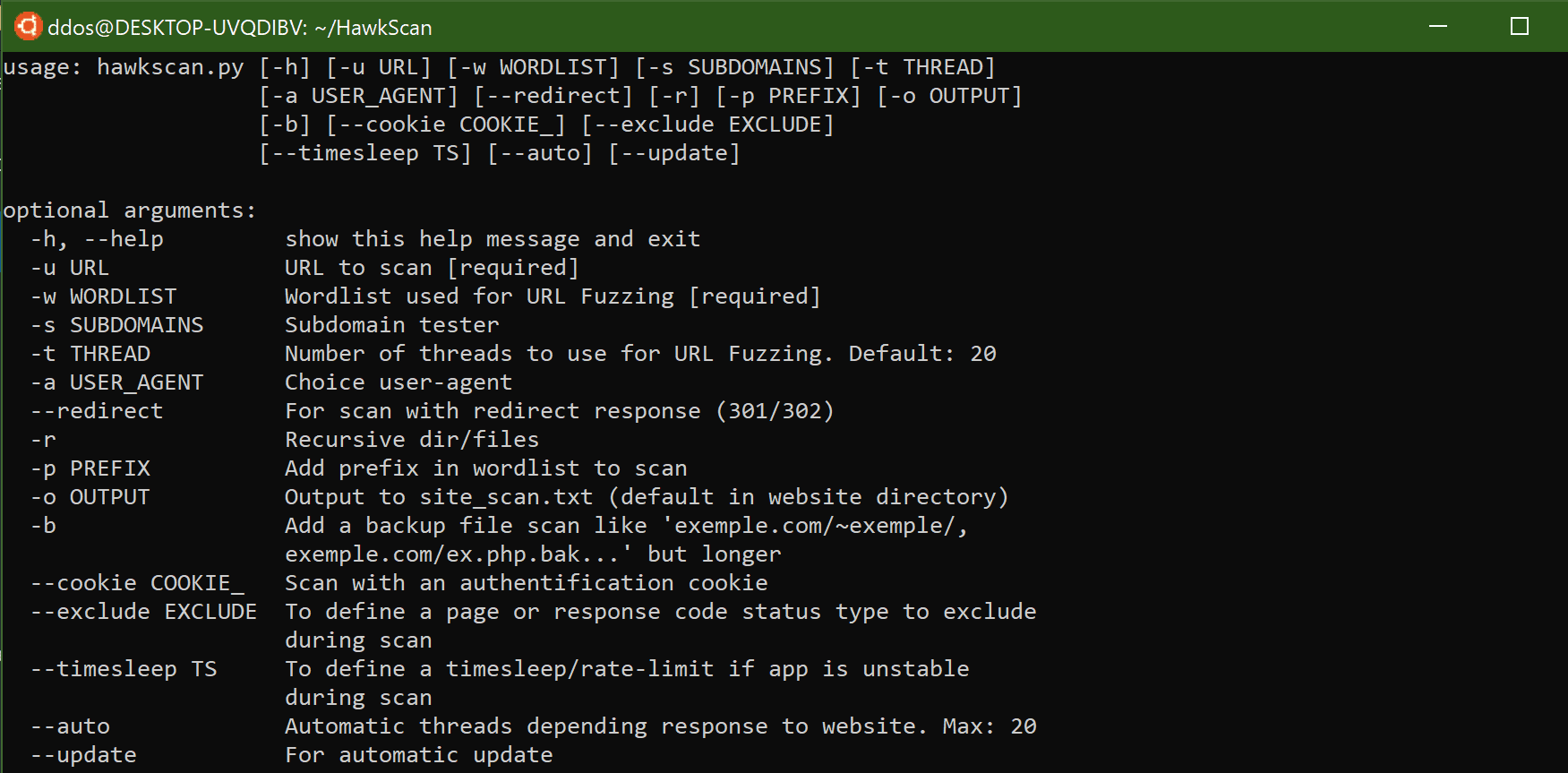
- URL fuzzing and dir/file detection
- Test backup/old file on all the files found (index.php.bak, index.php~ …)
- Check header information
- Check DNS information
- Check whois information
- User-agent random or personal
- Extract files
- Keep a trace of the scan
- Check @mail in the website and check if @mails leaked
- CMS detection + version and vulns
- Subdomain Checker
- Backup system (if the script stopped, it take again in the same place)
- WAF detection
- Add personal prefix
- Auto-update script
- Auto or personal output of scan (scan.txt)
- Check Github
- Recursive dir/file
- Scan with an authentication cookie
- Option –profil to pass profil page during the scan
- HTML report
- Work it with py2 and py3
- Add option rate-limit if the app is unstable (–timesleep)
- Check-in waybackmachine
- Response error to WAF
- Check if DataBase firebaseio exists and is accessible
- Automatic threads depending on the response to a website (and reconfig if WAF is detected too many times). Max: 30
- Search S3 buckets in the source code page
- Testing bypass of waf if detected
- Testing if it’s possible scanning with “localhost” host
Changelog v2.6
- Updated: dichawk endpoints
- New: lightmode option
Install
git clone https://github.com/c0dejump/HawkScan.git
cd HawkScan
pip3 install -r requirements.txt
Use
Source: https://github.com/c0dejump/





