HookChain: The Technique That Bypass Exposes EDR in 94% of Security Solutions
In an ever-evolving cybersecurity landscape, where threats are becoming more sophisticated by the day, the focus on Endpoint Detection and Response (EDR) systems has never been more critical. However, in a new study, cybersecurity researcher Hélvio Júnior, also known as M4v3r1ck, has introduced a novel technique that challenges the very foundations of these security measures. Dubbed “HookChain,” this innovative approach offers a new perspective on bypassing EDR solutions, shedding light on the vulnerabilities that still linger in today’s advanced security frameworks.
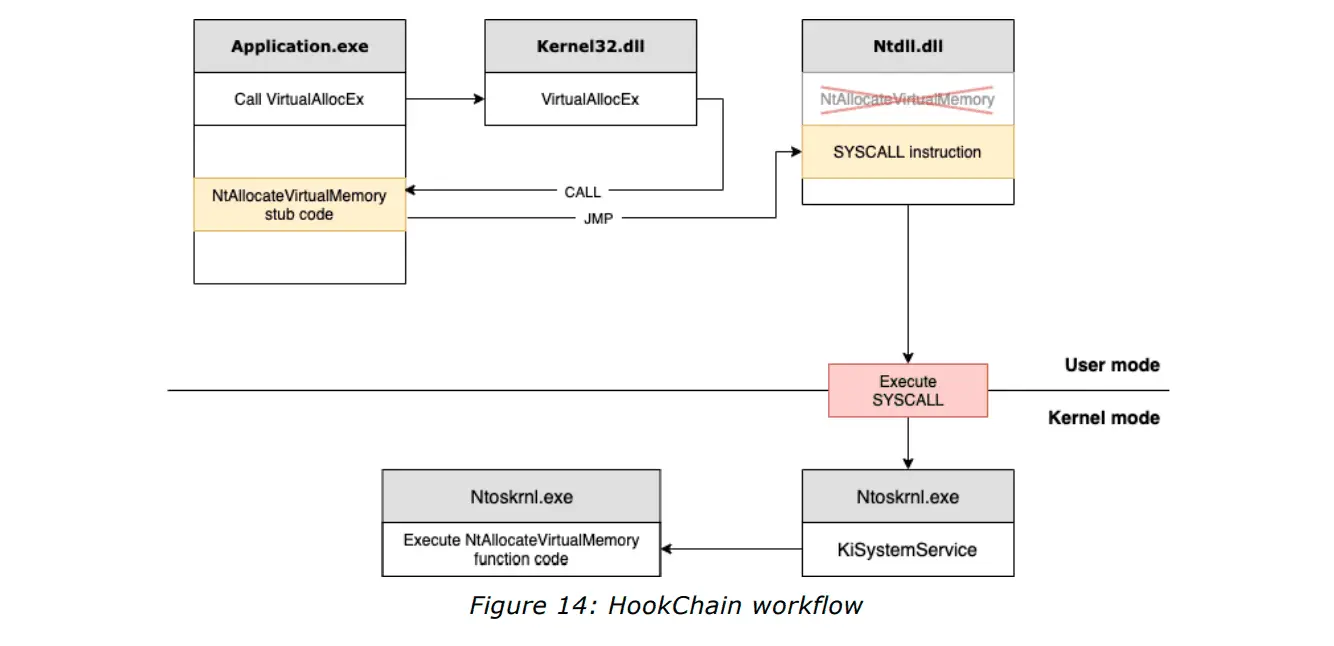
HookChain takes the art of evasion to a new level by combining several well-known techniques into a cohesive strategy that operates entirely within user mode. By leveraging a combination of Import Address Table (IAT) Hooking, dynamic System Service Number (SSN) resolution, and indirect system calls, HookChain effectively sidesteps the monitoring mechanisms employed by EDR systems that focus on the Ntdll.dll library. This library is a critical point for telemetry collection and serves as the last barrier before accessing the operating system’s kernel. HookChain’s brilliance lies in its ability to reroute the execution flow of Windows subsystems without altering the source code of the applications or malware involved, making its activities virtually undetectable by traditional EDR solutions.
The research highlights how HookChain can evade detection in 94% of the tested EDR solutions. Of the 16 EDR products analyzed, only one demonstrated a hook in the IAT beyond the Ntdll.dll layer, and 50% of the solutions showed no hooks in user mode at all. This startling discovery underscores the need for EDR developers to rethink their approach to security, as current solutions may not be as impenetrable as previously thought.
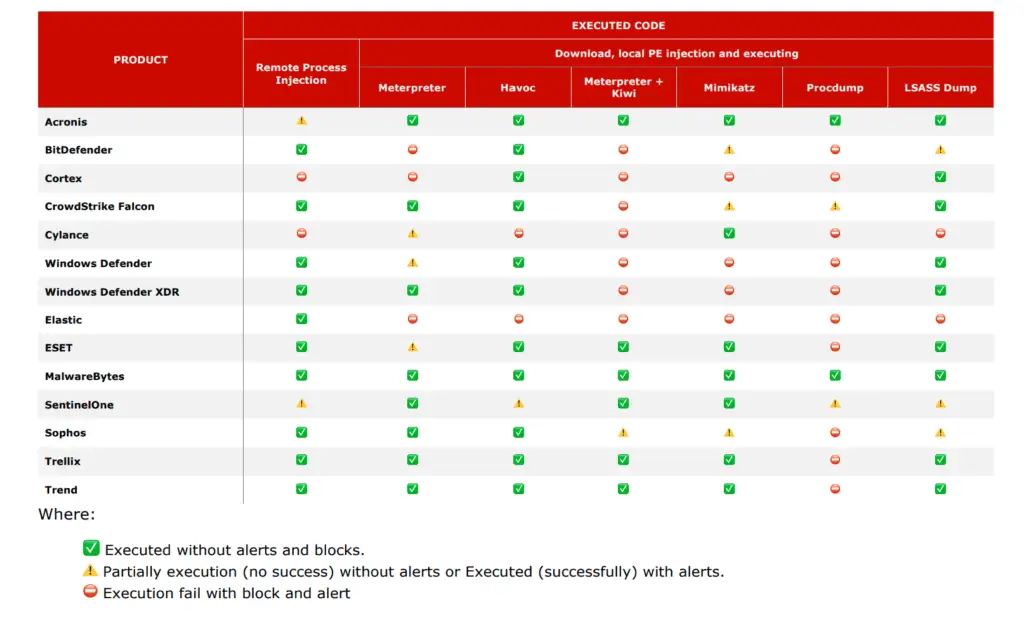
Image Credit: M4v3r1ck
At the core of HookChain is a meticulously crafted technique that starts with dynamic mapping of SSNs using methods like Halo’s Gate. It then progresses to preload critical DLLs and implement IAT hooks in key system libraries such as Kernel32, Kernelbase, and others. The result is an evasion method that not only bypasses EDR monitoring but does so with minimal impact on system performance, leaving the call stack telemetry unchanged. This allows HookChain to operate under the radar, effectively rendering the EDR’s detection mechanisms useless.
Hélvio Júnior’s HookChain research serves as a wake-up call to the cybersecurity industry. It demonstrates that even the most advanced EDR solutions are not infallible and that attackers continue to innovate in ways that can outpace current defenses. This study is not just a testament to the ingenuity of cyber adversaries but also a call to action for the cybersecurity community to develop more robust and adaptive security measures that can counteract such sophisticated techniques.
As this research gains attention, it is expected that cybersecurity firms will need to rapidly adapt to counteract the potential threats posed by HookChain. Meanwhile, the publication of the exploit code on GitHub has made this technique accessible to a wider audience, underscoring the urgency for a response from the cybersecurity community.





