HrServ Web Shell Defies Detection with Stealthy Techniques
During a recent investigation, Kaspersky Lab researchers discovered a DLL file identified as “hrserv.dll,” representing a previously unknown web shell with advanced capabilities, including specialized encoding methods for communication with the client and executing operations in memory.
Analysis of this sample led to the identification of related variants compiled as early as 2021, suggesting a potential link between these separate instances of malicious activity.
HrServ initiates its operation by creating a task in the Windows scheduler, masquerading as a routine system update. It employs a specialized script that downloads and activates the malicious file on the infected computer. Subsequently, HrServ configures itself to launch and be controlled through a remote server.

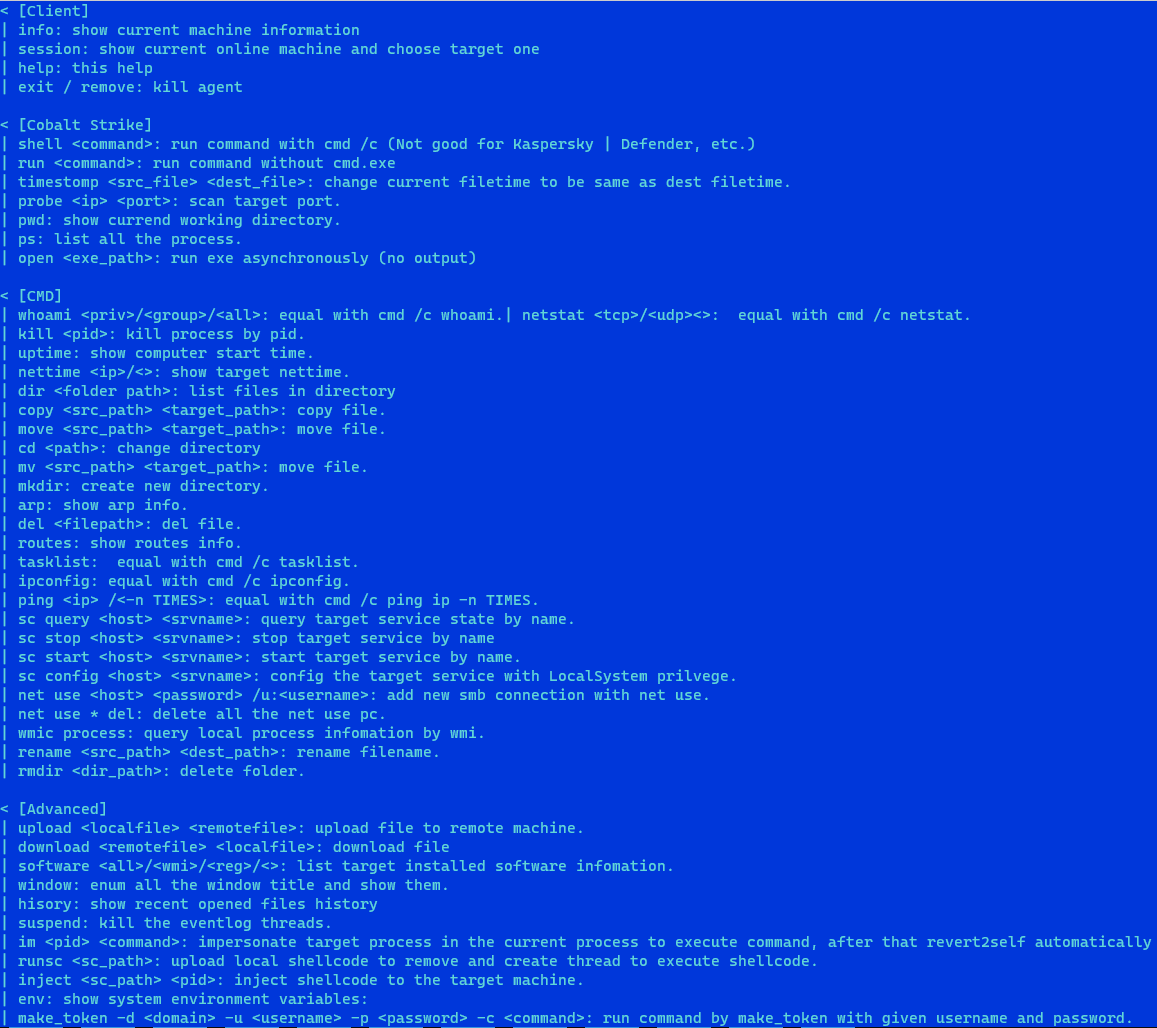
Available commands of the memory implant | Image: Kaspersky
This web shell skillfully conceals its activity, mimicking regular internet traffic. It utilizes complex methods, including Base64 encoding and FNV1A64 hashing algorithms.
Reportedly, the HrServ web shell can alter information in internet requests in such a way that they appear as standard queries to Google.
Once activated, the malware is capable of performing various actions on the infected device, including reading and writing files, as well as executing arbitrary commands. This allows attackers to steal data, monitor user activity, and even gain complete control over the computer.
Currently, it is known that this malware was used only for an attack on a government institution in Afghanistan. However, given its complexity and ability to disguise, HrServ could pose a threat to a wide range of organizations and individuals in any country worldwide.
Kaspersky Lab’s investigation underscores the necessity of vigilance and the use of advanced protective measures to safeguard against such threats. The team of experts will continue to research this web shell and monitor related activities to help prevent future attacks.




