IcePeony – A New China-Nexus APT Group Targeting Asian Nations
A previously unknown China-nexus advanced persistent threat (APT) group, identified as “IcePeony,” according to a recent report from the nao_sec Cyber Security Research Team. This group, active since at least 2023, has launched cyberattacks against government agencies, academic institutions, and political organizations in nations such as India, Mauritius, and Vietnam. IcePeony has become a significant threat, and the team’s analysis provides a rare look into the group’s sophisticated attack methodologies and geopolitical motives.
In an unusual turn of events, operational errors by IcePeony exposed their attack resources, offering researchers an invaluable opportunity to scrutinize their tactics. The group’s attack vectors typically begin with SQL injection techniques, targeting vulnerable public-facing web servers. When successful, they exploit the breach with webshells and custom backdoors—particularly a unique malware named “IceCache,” developed specifically for use in their campaigns.
“They have targeted government agencies, academic institutions, and political organizations in countries such as India, Mauritius, and Vietnam. […] In the log files we analyzed, there were over 200 attempts to attack various government websites in India,” the report states. Their primary objective appears to be credential theft, although the full scope of their intentions likely aligns with China’s national interests, particularly in maritime strategy.
The nao_sec report meticulously details the group’s timeline across a two-week period. Each day offers a fascinating glimpse into the attackers’ methods. From executing SQL injections to deploying IceCache, the attackers demonstrated a clear strategy for deepening their foothold across government networks. On day-1, for example, SQL injections paved the way for webshells, and by day-4, proxy rules had been established via IceCache. Notably, the attackers do not appear to work on Sundays, leading researchers to suspect that IcePeony operates under the 996 working hour system, common in China’s IT industry—working from 9 a.m. to 9 p.m., six days a week.
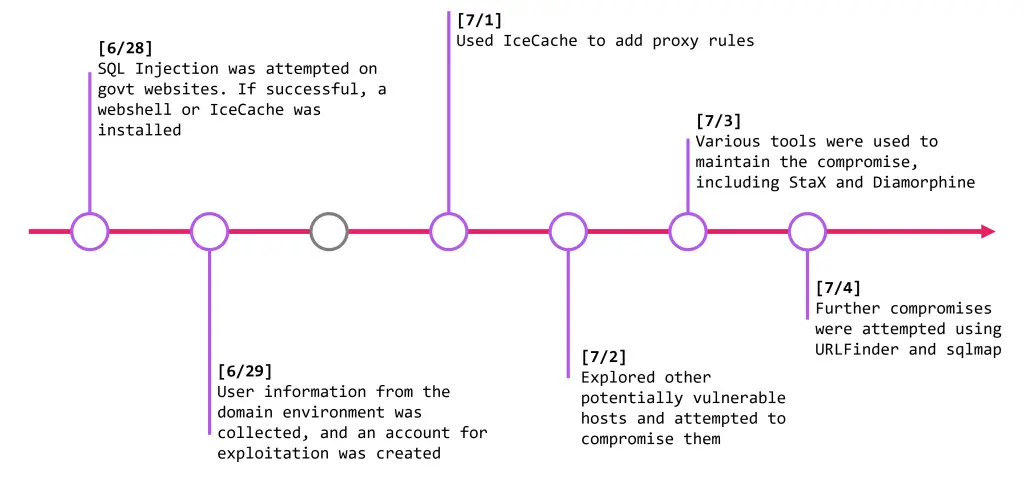
Image: nao-sec
An intriguing find in the attackers’ zsh_history file revealed their use of customized helper commands, such as “hPass,” which provides tutorials for Mimikatz, improving their attack efficiency.
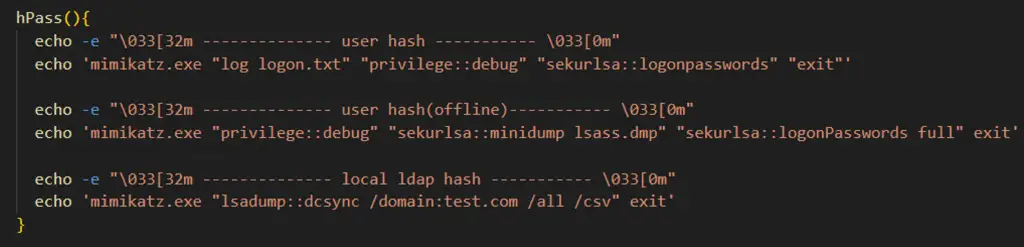
Image: nao-sec
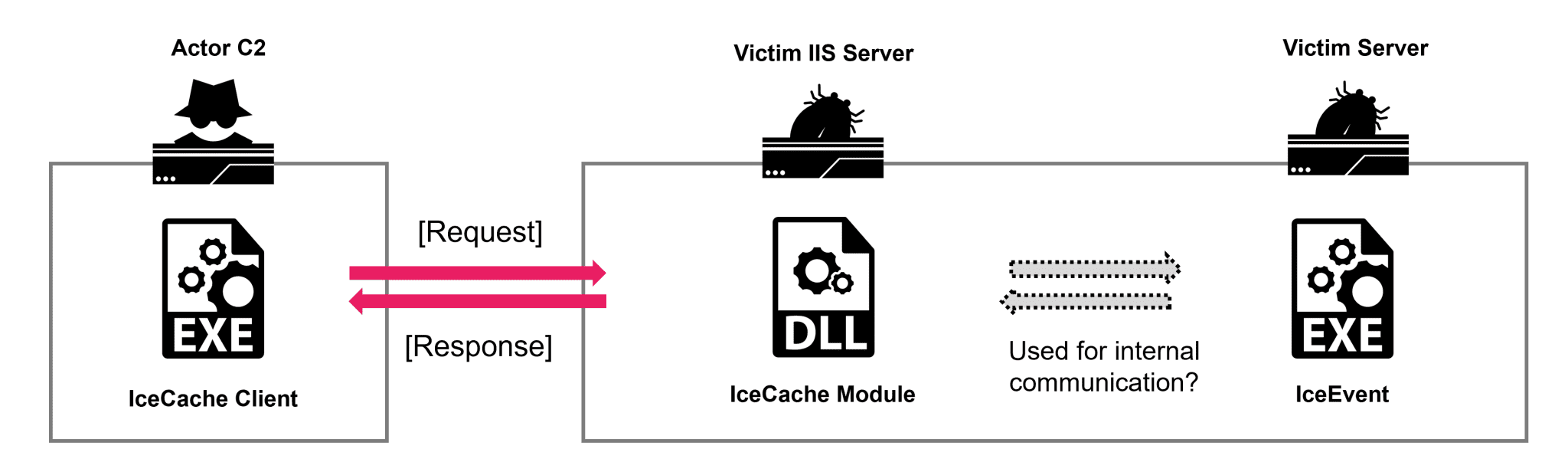
At the main of IcePeony’s operations is a suite of custom tools. Their malware of choice, IceCache, is an ELF64 binary developed in Go, adapted from open-source software called reGeorge. IceCache’s command set is extensive, allowing it to function as a proxy and facilitate file uploads and downloads. Alongside IceCache, the group employs StaX, an enhanced version of the open-source tool Stowaway, which features encryption and high-performance proxy functionalities.
The nao_sec team also discovered another piece of malware associated with the group, dubbed IceEvent, a passive-mode backdoor that shares similarities with IceCache in terms of its encoding and command execution. While IceEvent appears to be a simpler tool, the researchers suspect it was used in cases where the group required minimal functionality to maintain persistence on compromised systems.
IcePeony’s ties to China are reinforced through a variety of clues found during the investigation. Simplified Chinese comments were found in the wrapper scripts for IceCache, and the group’s activity times align with UTC+8, consistent with Chinese working hours. Furthermore, the report suggests that IcePeony’s operations align with China’s strategic interests, particularly in Indian Ocean regional geopolitics, which is highlighted by the group’s focus on targets in India and Mauritius, both countries increasingly wary of China’s maritime influence.
Related Posts:
- China-Linked Phishing Campaign Exploits Geopolitical Tensions, Ravages Asian Finance Sector
- Misinformation Campaigns Surge in the Philippines Amidst Geopolitical Tensions
- India Post Customers Targeted in Massive Phishing Scam
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions





