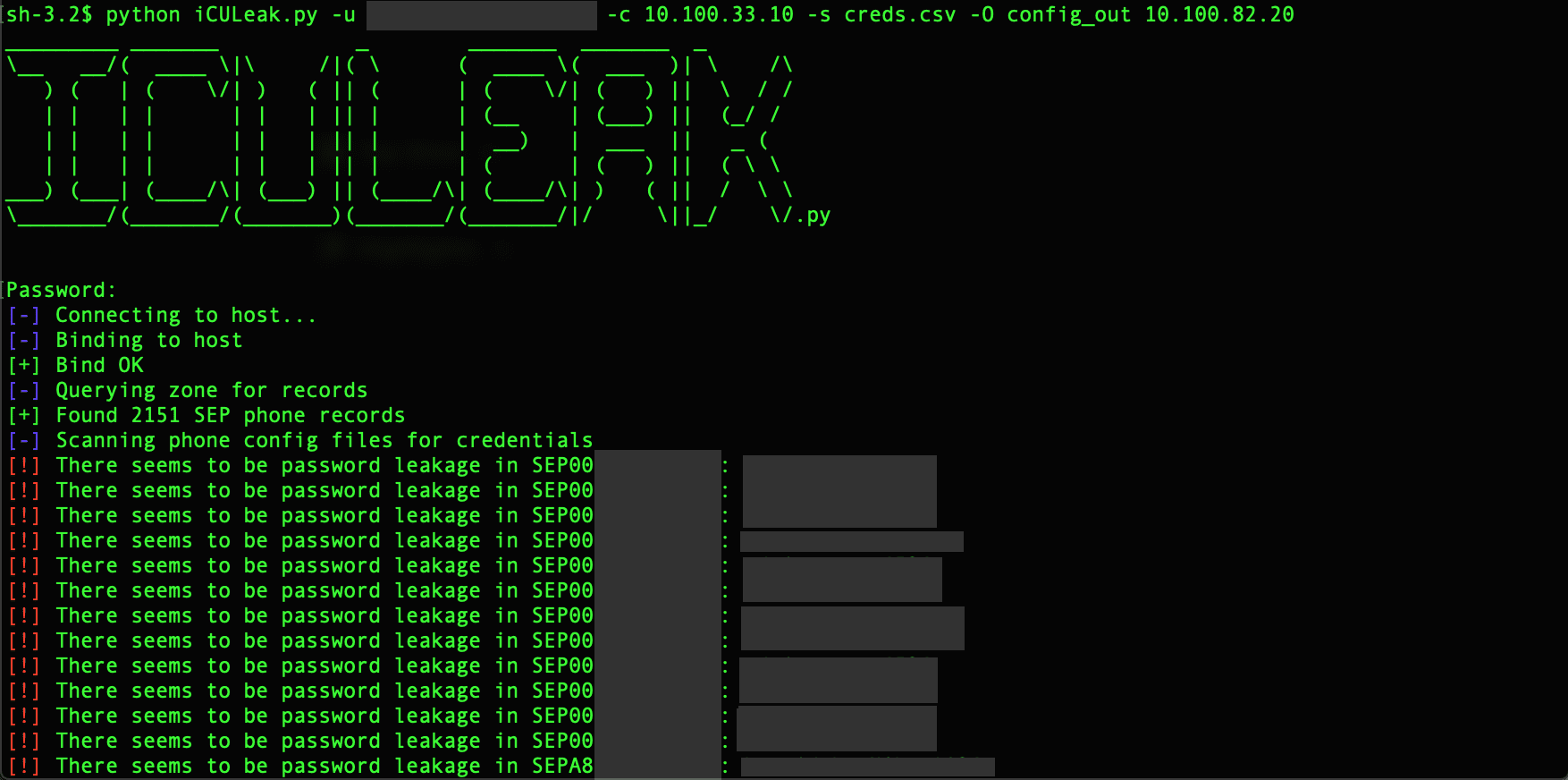
iCULeak: find and extract credentials from phone configuration files hosted on CUCM
iCULeak.py
A tool to find and extract credentials from phone configuration files in environments managed by Cisco’s CUCM (Call Manager).

When using Cisco’s CUCM (Call Manager), phone configuration files are stored on a TFTP server. These phone configuration files quite frequently contain sensitive data, including phone SSH/admin credentials.
There is also an issue with how some browsers autofill fields such as the SSH Username & Password fields with their CUCM credentials (commonly their AD credentials) if the administrator has saved the credentials in their browser. This issue has also been faced by administrators using password managers that automatically plug in credentials, where they found that their credentials were being automatically inputted into the SSH Username & Password fields, and then being saved (and stored in plaintext in the configuration files).
While the issue was fixed in CUCM 12.0, credentials stored in the past may still be discoverable.
The issue can be somewhat mitigated by the following actions:
- Regularly purging existing configuration files from leaked credentials.
- Blocking autosave/autofill on CUCM.
- Enabling encryption of phone configuration files. Read more on that here. Note that this doesn’t completely mitigate the issue, as the encryption password could be obtained from the phones’ memory or through administrative access of CUCM.
This tool utilizes a lot of code from Dirk-Jan’s tool adidnsdump to extract a list of phone hostnames from ADIDNS over LDAP. To read more about the technique and tool, you can read the associated blog post. So credit goes to him for a lot of the code.
Installation
git clone https://github.com/llt4l/iCULeak.py
cd iCULeak.py
pip install -r requirements.txt
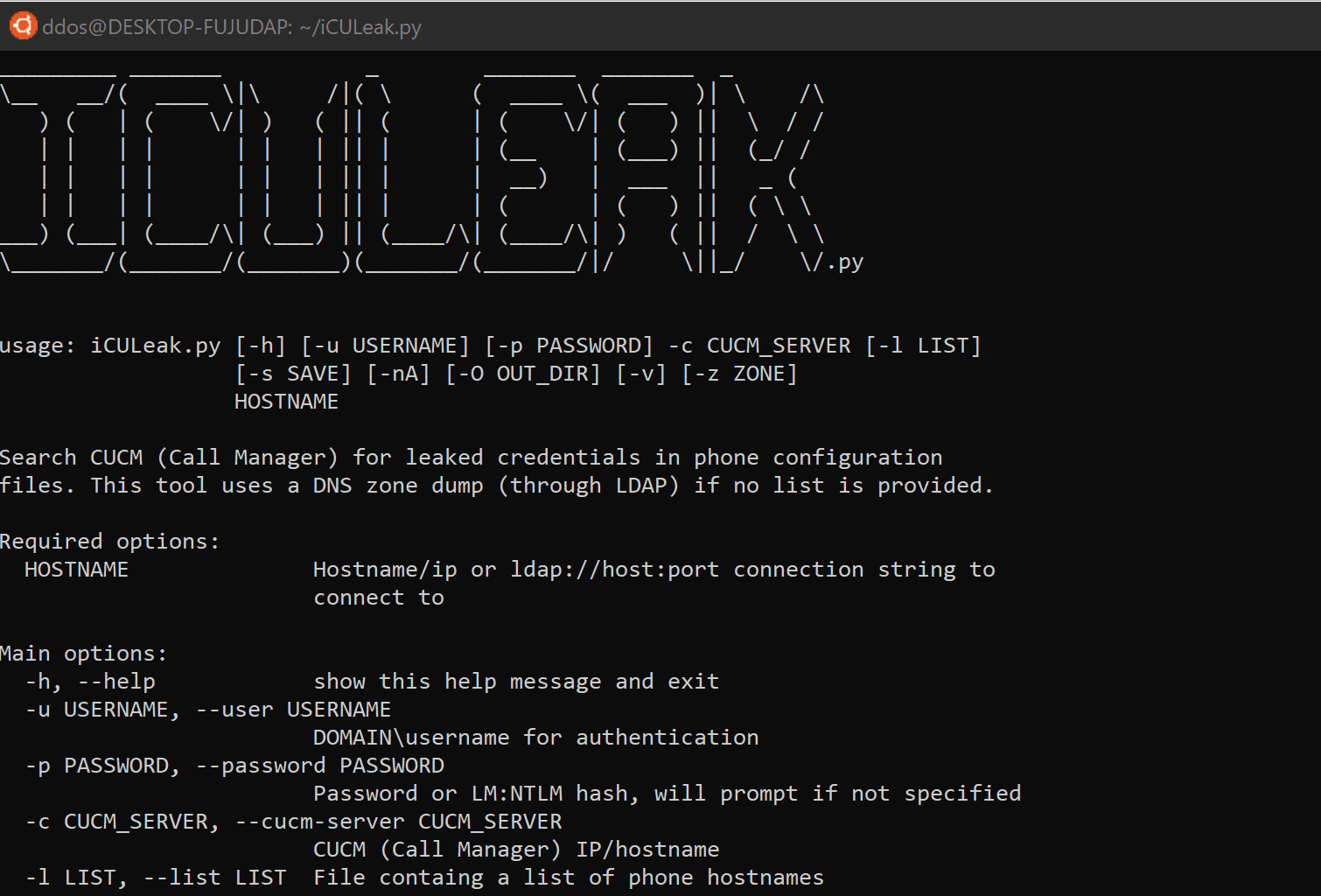
Usage
Copyright (c) 2019 t4
Source: https://github.com/llt4l/





