iLeakage: Exposing Safari’s Persistent Spectre Attack
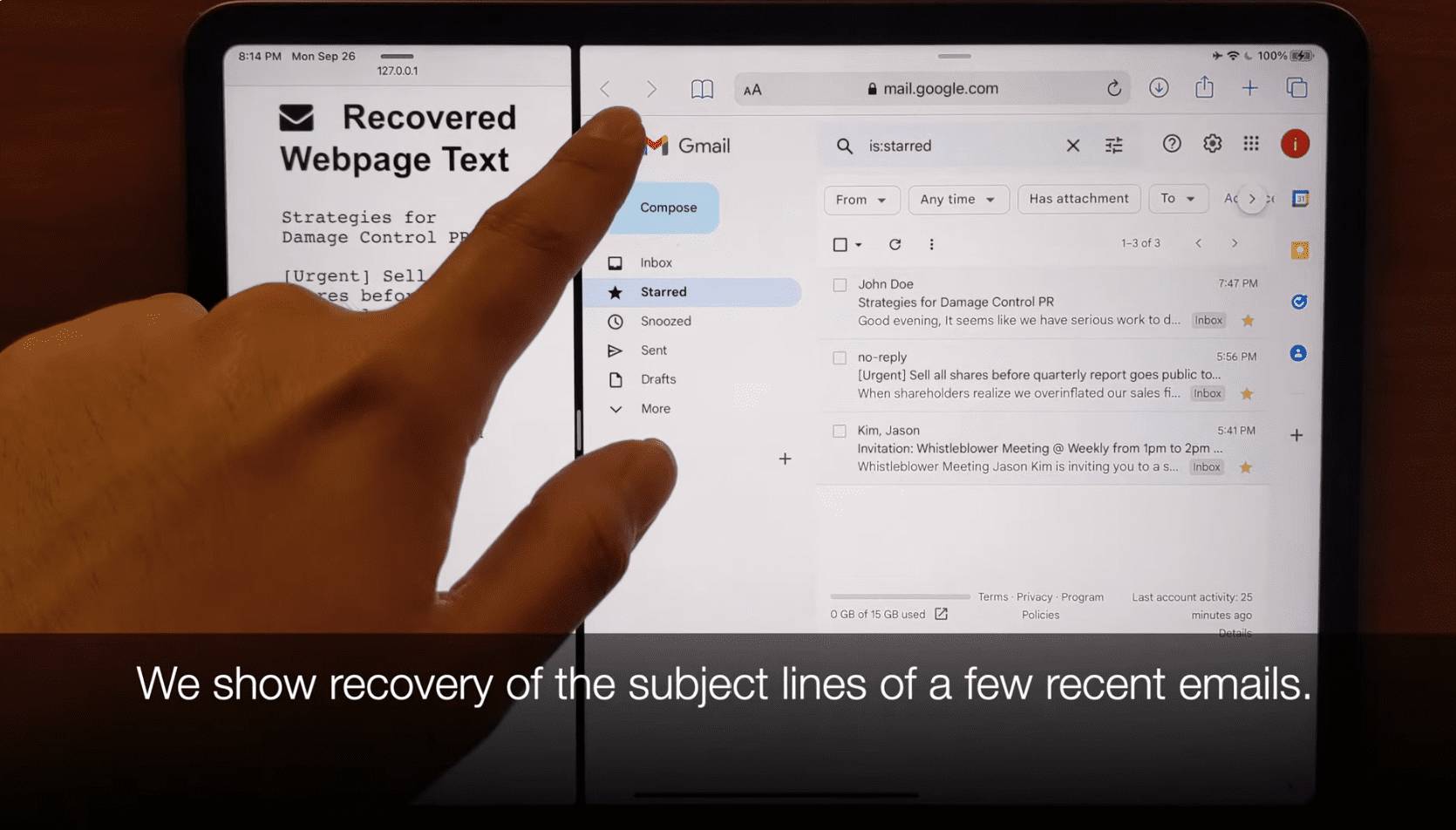
Researchers have crafted an attack compelling Safari to divulge passwords, Gmail message contents, and other confidential data, by exploiting a vulnerability in the A and M series processors, integral to contemporary iOS and macOS devices.
Termed ‘iLeakage‘, this side-channel attack is not only practical but requires minimal resources for execution. However, it does necessitate an intricate understanding of Apple’s hardware and expertise in exploiting vulnerabilities within the practical implementations of cryptographic systems. The underlying vulnerability mechanism revolves around speculative execution – a feature designed to boost the performance of modern processors.

iLeakage has been presented as a website, accompanied by videos demonstrating various attack vectors. When a user of a vulnerable macOS or iOS device visits this website, iLeakage, through JavaScript, covertly opens another maliciously chosen site, restoring its contents displayed in a pop-up. The researchers adeptly wielded iLeakage to access YouTube viewing history, Gmail mailbox contents, and auto-filled passwords.
https://www.youtube.com/watch?v=2uH9slLKTjw
While iLeakage operates on Mac solely via Safari, iPhones, and iPads are susceptible through any browser, given they all hinge on Apple’s WebKit engine. An Apple spokesperson acknowledged awareness of this vulnerability, affirming plans to rectify it in an imminent software update.
WebKit’s nuances and the architecture of the A and M series processors enabled the circumvention of existing protective measures aimed at thwarting speculative execution attacks. Weak points in protection implementation allowed iLeakage to surmount it.
For the attack to transpire, the vulnerable device must first visit the iLeakage website. Concurrently logged into a compromised website and the attacker’s site, approximately 5 minutes are requisite to analyze the visiting device. Subsequently, iLeakage can coerce the browser to open any site and commence data transmission at a rate ranging from 24 to 34 bits per second.
Despite its technical intricacy and the profound knowledge required for its execution, the likelihood of this vulnerability being harnessed for imminent real-world attacks is exceedingly slim. It is anticipated that Apple will release a corrective measure before iLeakage emerges as a tangible threat.





