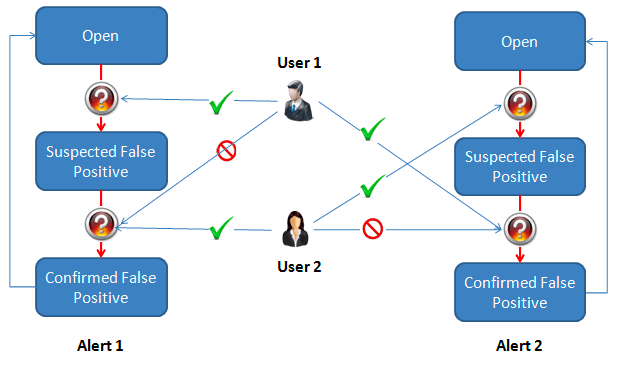
Source

I watched a movie some time ago titled Fiery Priest. In that movie, there were four business colleagues who had kept their money in a safe. The safe had four locks, and the lock can only be opened with all four of their fingerprints.
So, if 3 of them wanted to stab the 4th in the back, they wouldn’t be able to do so because the fingerprint of the 4th person is equally needed. They wouldn’t be able to do so without some difficulty. This provides high security for their money and prevents anyone from betraying others.
An Example
Let us look at a scenario that people have faced while operating a business or setting up security protocols and how they addressed them.
Security is of crucial importance in the blockchain. Some decentralized organizations are member-owned. For them, ensuring that all members work towards a common goal can be difficult. Often different members may feel they know what is best and act on that impulse, against the better judgment of the others.
Using Signatures for Security
To prevent this, organizations have set it up so that a smart contract cannot be executed without the digital signature of each of the members involved in decision-making. Without the signature of each individual, the deployment or execution of the contract fails. This ensures that each stakeholder has veto power and no decision is taken without everyone’s approval.
Adding Qualified Persons to the List of Approvers
Another way you can set up your security protocol is by creating a qualified person panel that has to approve things. For example, companies can set it up so that the CEO, COO, and accountant need to agree before money can leave the company.
So, say the marketing head wants to try a marketing strategy. The CEO, COO, and accountant will need to agree to the plan before they can go ahead.
See a common theme till now?
These are all examples of a type of security principle called the ‘four eyes principle’.
The Four Eyes Principle

The Four Eyes Principle means an activity or an action must be approved by at least two people. This is also called the two-man rule. This is to prevent actions that are not consented to and any fraudulent activity from an external person.
The main objective of this principle is to prevent mistakes while taking action, avoid fraudulent activity, and also ensure high security.
Now that we have a thorough understanding of the four eyes principle, let us see how we can enable it using the Tatum key management system (KMS).
Tatum Key Management System
The Tatum KMS is used to store private keys and mnemonics of the blockchain wallets securely. It runs locally on the server and provides security for wallets, addresses, private keys, and signing transactions.
This data is encrypted and stored on your server. It can only be decrypted by you using a password. A password is the most sensitive information in the system.
Installation
The Tatum KMS runs on different operating systems like Mac OS (natively or via docker), Unix (natively or via docker), and MS Windows(via docker only).
It can be installed via npm. Run the following code in your terminal:
| npm i -g @tatumio/tatum-kms |
As a docker image:
| docker pull tatumio/tatum-kms |
Usage
It is important to know how the KMS installed can be used so that you can tweak it as per your need.
To see all the commands available to run, you can use the help command:
| tatum-kms –help |
Tatum KMS periodically checks for any new pending transactions to sign and by doing this, it runs as a daemon by default.
The Tatum KMS checks for the pending transaction every five seconds. For every 500 signature IDs, 1 credit is consumed per API call.
Interestingly, the frequency of checking for transactions can be changed from 5 secs to any time you want using the –period command.
| tatum-kms daemon –period=20 |
Tatum KMS uses the daemon memory to store data that are encrypted and the password to the wallet store. So after a successful set-up, the daemon requires the password to the wallet store.
| bash:$ tatum-kms daemon Enter password to decrypt wallet store: |
The wallet store by default saves in the user’s home folder under .tatumrc the folder. To change the path to the wallet file, use the –path parameter.
Alternatively, the password can be provided via the environment variable.
| tatum-kms daemon –path=/path/to/wallet/store/directory/wallet.dat
OR TATUM_KMS_PASSWORD=password |
By doing the above you have access to your data in the wallet store. For security, there is a need for the four eyes principle, which I have explained earlier.
The Tatum KMS checks for transactions on different supported blockchains BTC, BCH, BNB, LTC, ETH, ETH ERC20s, XLM, XRP, VET, DOGE, TRON, BSC, CELO, FLOW, XDC, EGLD. You can check for transactions with a different type of blockchain of your choice using the -–chain parameter.
| tatum-kms daemon –chain=BTC,LTC,ETH |
So, where does the four-eyes principle come in?
The four eyes principle can be enabled to verify that the transaction to sign with the KMS is yours.
To do so, the external-url parameter needs to be added and set up in your application server. The server should hold a list of valid transactions to sign. The external-url is very important on mainnet for security in the production environment.
Every time a transaction from Tatum is fetched to be signed, there is a validation against the external server using a simple HTTP GET operation.
| tatum-kms daemon –external-url=http://192.168.57.63 |
Conclusion
Tatum KMS can help build and scale custodial apps, and also provide high security for users. More security can be attained using the four eyes principle, which is supported by Tatum KMS. There are different use cases for the Tatum KMS. Some of them are deploying smart contracts, minting NFTs, etc. You can get to know more use cases through their docs.
The Tatum KMS is a highly recommended platform for this because it allows you to use blockchain technology without having to deal with complex issues like private keys.