“INC” Ransomware Surge: New GOLD IONIC Group Hits Global Targets
Cybersecurity researchers at Secureworks Counter Threat Unit (CTU) are tracking a significant escalation in activity from the GOLD IONIC ransomware group. This aggressive threat group has rapidly amassed a list of victims since emerging in August 2023. Their attacks target organizations worldwide, deploying custom “INC” ransomware that encrypts vital data and holds it hostage. To increase pressure, they threaten to publicly release stolen information if ransom demands are not met.
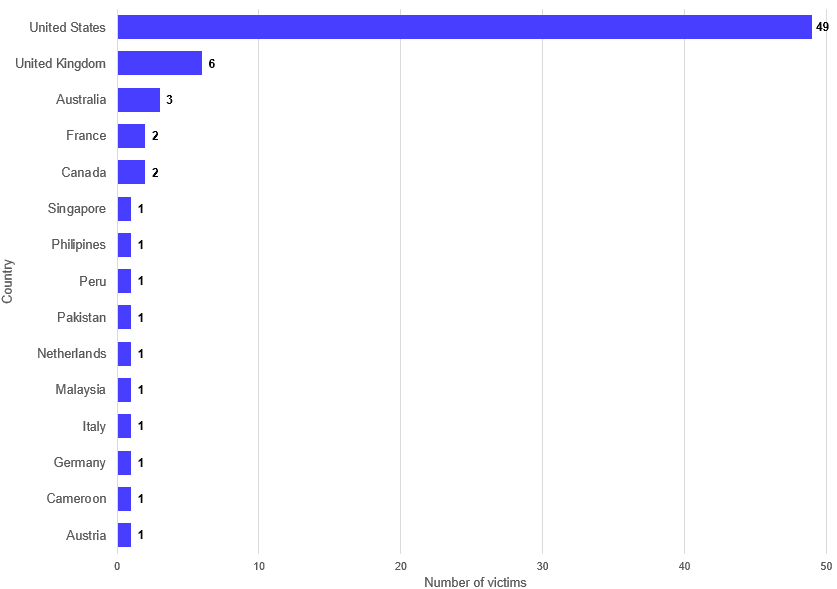
Who’s at Risk: U.S. Businesses Top the List

Geographic locations of victims posted to GOLD IONIC’s leak site. (Source: Secureworks)
GOLD IONIC’s attacks demonstrate their indiscriminate nature, affecting businesses and organizations across various sectors. However, their focus appears to be on United States targets, with industrial, healthcare, and education institutions suffering a disproportionate number of attacks. The healthcare sector, already battling numerous challenges, faces a severe risk from ransomware, as lives and patient data hang in the balance. Educational institutions, custodians of sensitive student records and research, also find themselves increasingly in the crosshairs.
Tactics Revealed: From Citrix Exploits to Double Extortion
Secureworks investigations indicate a pattern in GOLD IONIC’s attack methods. Initial access is often gained by exploiting known vulnerabilities like the “Citrix Bleed” flaw (CVE-2023-4966). Once established within a network, attackers use powerful tools like AdFind and Meterpreter to map out the victim’s environment. This reconnaissance allows them to identify and stealthily exfiltrate the most valuable data, maximizing leverage in ransom negotiations. Finally, the devastating “INC” ransomware payload is deployed, disrupting operations, and leaving the victim grappling with encrypted files and a chilling ransom note.
Ransomware Landscape: Shifting Alliances and Blurred Lines
The Secureworks report reveals a complex web of ransomware players. While GOLD IONIC appears to operate independently, its tactics and the structure of its leak site bear strong similarities to the notorious LockBit operation. Additionally, there are hints that some victims originally targeted by other ransomware groups have had their data posted to the GOLD IONIC leak site, indicating potential fluidity in the allegiances of ransomware affiliates.
Call to Action: Defending Against GOLD IONIC
“GOLD IONIC is yet another emerging ransomware group quickly amassing victims, and its tactics, techniques, and procedures (TTPs) are similar to many other groups. CTU researchers advise organizations to follow guidance provided by the U.S. Cybersecurity & Infrastructure Security Agency (CISA) and the UK National Cyber Security Centre (NCSC) to mitigate the risk of ransomware attacks,” says Secureworks Counter Threat Unit researcher.





