Information-Stealing ViperSoftX Malware Targets Cryptocurrencies and Password Managers Across the Globe
ViperSoftX, an information-stealing malware notorious for targeting cryptocurrencies, has recently evolved with new execution techniques and encryption methods. Initially discovered in 2022, the malware has gained attention for hiding malicious code within log files. Researchers at TrendMicro have observed the malware’s arrival and execution via DLL sideloading, a more sophisticated encryption method involving byte remapping, and a monthly change in command-and-control (C&C) servers. These enhancements make analysis and decryption more time-consuming for cybersecurity experts.
Global Impact: Consumer and Enterprise Sectors

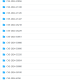
Top 10 countries affected by ViperSoftX in both the consumer and enterprise sectors
Source: Trend Micro™ Smart Protection Network™ (SPN)
ViperSoftX has affected a significant number of victims in both consumer and enterprise sectors. Australia, Japan, and the United States are the top three countries impacted in the consumer category, while Southeast Asian countries constitute the majority of affected organizations in the enterprise sector.
Arrival Routine: Malicious Actors Exploit Illegal Software Solutions
Typically, ViperSoftX arrives as a software crack, activator, patcher, or key generator (keygen). Cybercriminals behind the malware exploit the fact that users seeking bootleg software versions often believe such programs are flagged as “false positives.” The actors behind ViperSoftX go a step further by using actual non-malicious software as carriers for the malware, encrypting it within the overlay.
Commonly abused software includes multimedia editors, video format converters, cryptocurrency coinminer apps, phone-related desktop apps, and system cleaner apps. Binary carriers observed by the researchers include gup.exe from Notepad++, firefox.exe from Tor, and ErrorReportClient.exe from Magix, a multimedia-editing software.
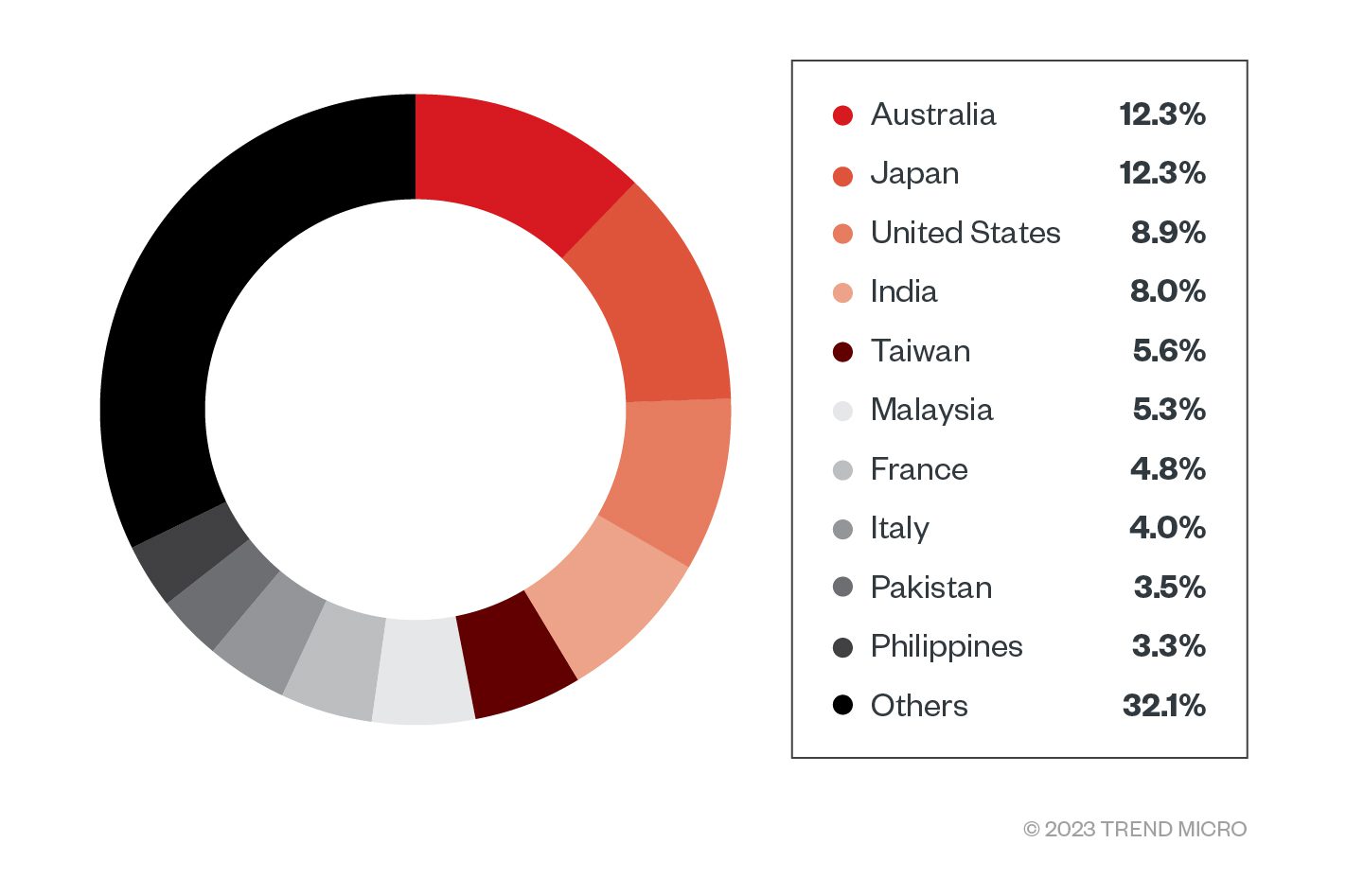
Infection Routine: Checking for Virtualization, Monitoring Tools, and Antivirus Products
Execution flow of ViperSoftX | Source: Trend Micro
Before executing its main routine, ViperSoftX checks for virtualization strings and monitoring tools to ensure the system isn’t running a virtual machine (VM). It also verifies that Process Monitor isn’t running on the machine and those specific antivirus products, such as Windows Defender and ESET, are not installed and active. If all checks pass, the malware proceeds to decrypt the PowerShell code and download the main ViperSoftX routine.
Unique Encryption: Byte Remapping
The updated ViperSoftX uses byte remapping, a simple yet effective encryption method that makes decryption difficult without the correct byte map. The malware benefits from this technique as it reduces the presence and actions made by a large graph of objects, making forced decryption more challenging.
Password Theft: Targeting Cryptocurrency Wallets and Password Managers
ViperSoftX is known for targeting cryptocurrencies, but recent investigations have revealed that it can also check for specific password managers. In addition to scanning local directories for cryptocurrency wallets, the malware checks for wallets via browser extensions and searches for password managers like KeePass 2 and 1Password.
A Growing Threat: Consumer and Enterprise Victims
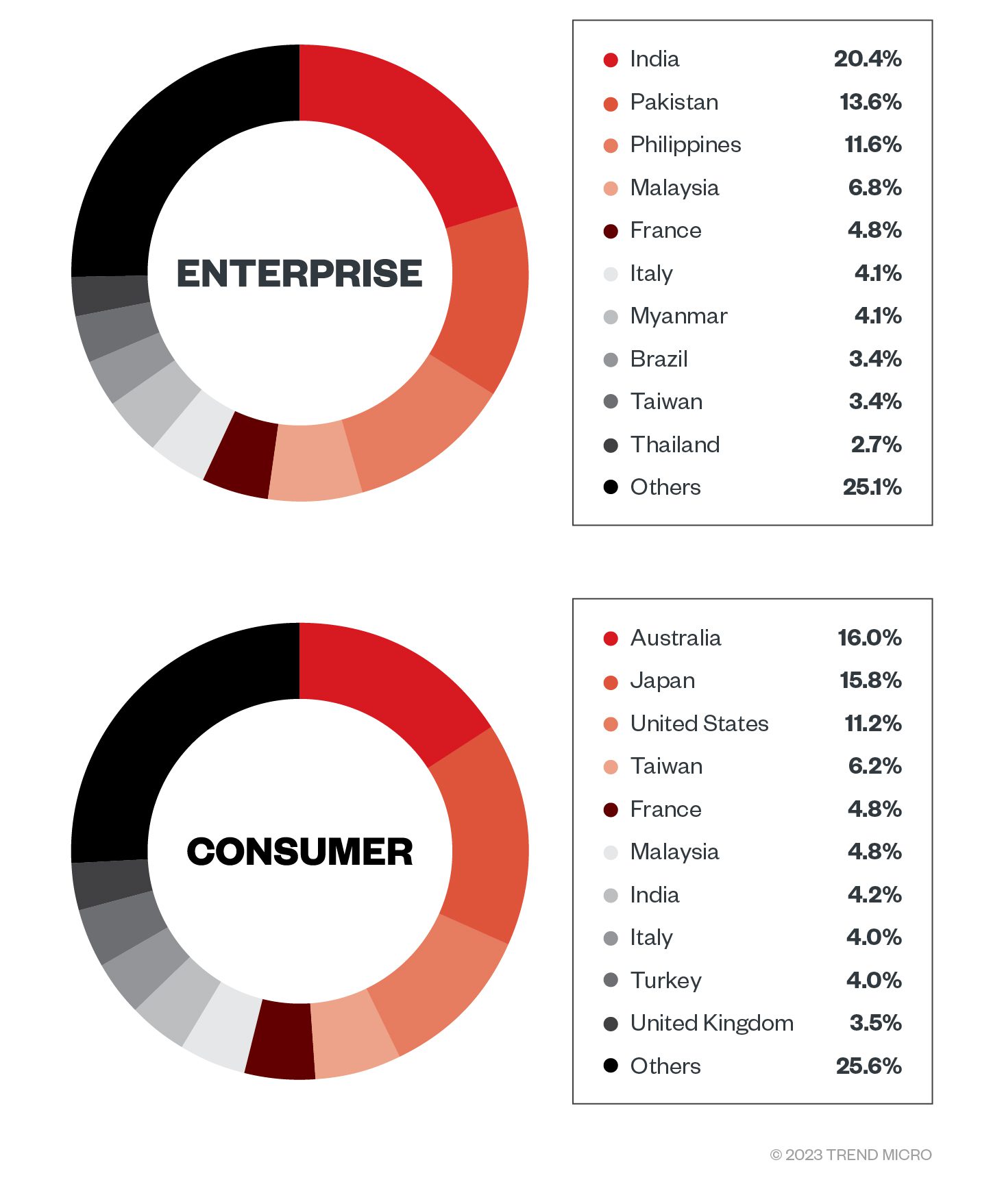
Top 10 countries affected by ViperSoftX malware in the enterprise (top) and consumer (bottom) sectors
Source: Trend Micro Smart Protection Network (SPN)
Initially, researchers believed that the malware would primarily target regular users. However, over 40% of the total victims were found to be from the enterprise sector. Australia, Japan, and the United States are the most affected countries, with a significant number of victims in Asia’s enterprise sector.