Introducing Shadow Dumper: A Powerful Tool for LSASS Memory Extraction
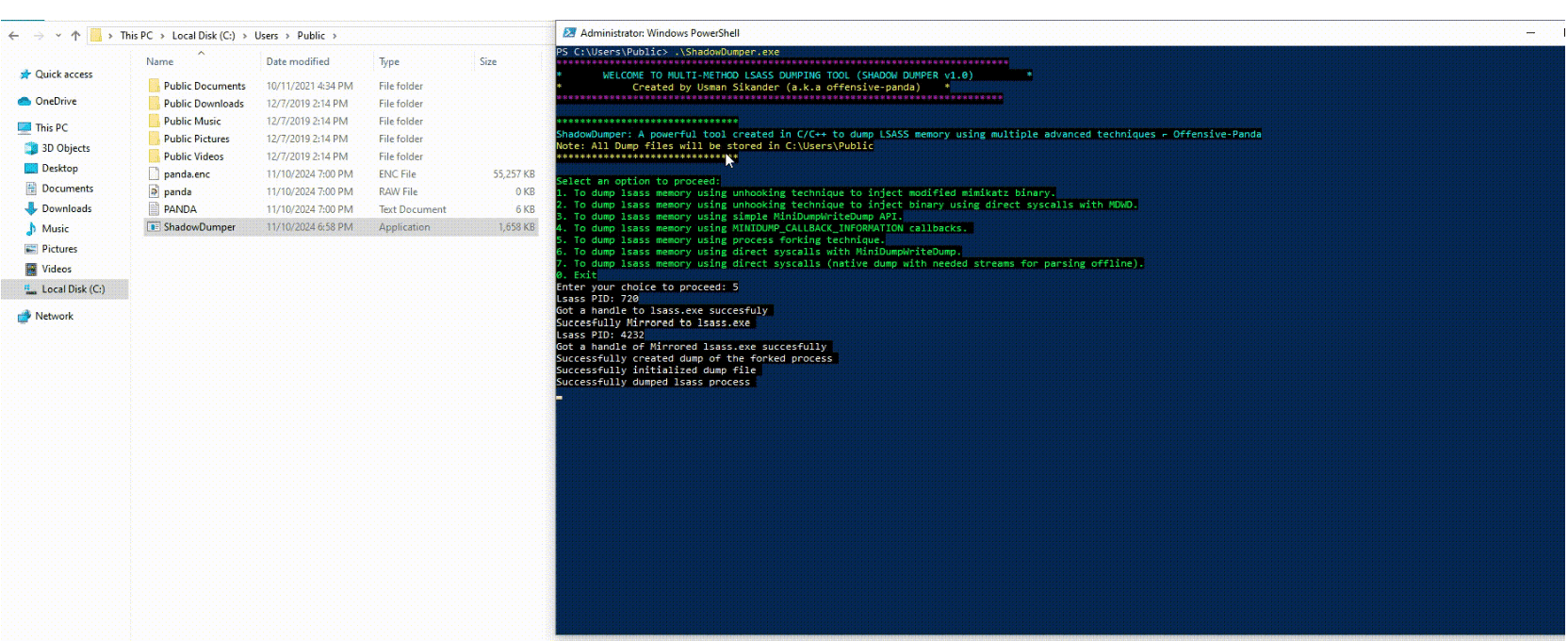
In the world of cybersecurity, penetration testers and red teams need sophisticated tools to assess and improve an organization’s security posture. One such tool gaining traction is Shadow Dumper, an open-source utility designed to extract data from the LSASS process.
LSASS (Local Security Authority Subsystem Service) is a critical Windows process responsible for managing user authentication and security tokens. This makes it a prime target for attackers seeking to steal credentials and gain unauthorized access. Shadow Dumper helps security professionals simulate such attacks, allowing them to identify vulnerabilities and strengthen defenses.
What Makes Shadow Dumper Special?
Shadow Dumper stands out due to its versatility and stealth. It employs a variety of techniques to dump LSASS memory, making it harder for security solutions to detect its activity. Some of its key features include:
- Unhooked Injection: This technique bypasses security software by injecting a modified Mimikatz binary (a popular credential extraction tool) directly into LSASS memory, avoiding common hooks used for detection.
- Direct Syscalls: Shadow Dumper can leverage direct system calls, reducing its reliance on the Windows API and minimizing its footprint. This makes it harder to detect and block.
- Process Forking: By creating a copy of the LSASS process, Shadow Dumper can extract data without directly interacting with the original process, further reducing the risk of detection.
- Offline Parsing: For extremely sensitive environments, Shadow Dumper can create a native memory dump with essential streams for offline analysis. This allows for a thorough investigation without raising alarms on the target system.
Why is LSASS Dumping Important?
Dumping LSASS memory can reveal sensitive information like:
- Usernames and passwords: Often stored in clear text or easily reversible formats within LSASS.
- Security tokens and hashes: Used for authentication and authorization, potentially allowing attackers to impersonate users.
- Kerberos tickets: Granting access to network resources, which can be exploited for lateral movement within a network.
By simulating these attacks, security professionals can identify weaknesses in authentication mechanisms, access controls, and security software configurations.
The Future of Shadow Dumper
The developers behind Shadow Dumper are actively working on exciting new features, including:
- Enhanced Defense Evasion: Making it even harder for endpoint detection and response (EDR) solutions to identify and block its activities.
- On-Disk Detection Evasion: Encrypting the dump file before saving it to disk, further minimizing the risk of detection.
- Exfiltration Capabilities: Enabling the secure transfer of the dump file to a command-and-control server for analysis.
- Expanded Techniques: Adding more methods for LSASS memory extraction to stay ahead of evolving security measures.
Shadow Dumper: A Valuable Tool for Security Professionals
With its powerful capabilities and commitment to innovation, Shadow Dumper is an essential tool for penetration testers and red teams. By simulating real-world attacks, it helps organizations proactively identify and mitigate security risks, ensuring the confidentiality, integrity, and availability of their critical assets.
For those interested in exploring or contributing, the project can be found on GitHub—a great place to learn, experiment, and stay ahead of the curve in the field of offensive security.
Important Note: It is crucial to use Shadow Dumper ethically and legally, only on systems where you have explicit permission. Unauthorized use can have serious legal consequences.





