iOS Trustjacking vulnerability: Hackers can take over your iPhone with iTunes Wi-Fi Sync
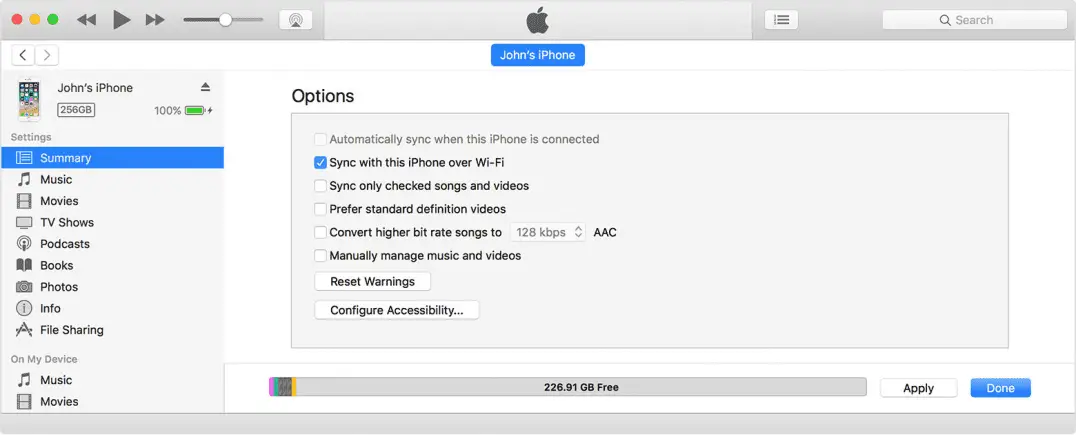
The security researcher at Symantec security recently discovered a vulnerability on Apple iPhone. When the device is paired with a Mac or laptop successfully, the hacker can use the default trust of the device to gain the iPhone’s permission. This is called Trustjacking. Technically speaking, this vulnerability stems from the “Sync with this iPhone over Wi-Fi” feature in the iTunes synchronization software installed on the computer. If this option is checked on the computer when an iPhone device is connected to the computer, it only needs to be in the same In a wireless network, data synchronization can be performed directly without data lines.
The first feature is to facilitate the user to synchronize the data between the computer and the mobile phone at any time. However, because the iTunes software on the default computer can obtain the highest authority of the mobile device, even if the mobile phone does not access the computer through the data cable, it is only in the same wireless. In the network, computer users can control the mobile phone.

At the recent RSA 2018 security conference, Symantec’s Roy Iarchy stated that hackers can use this to control the phone without the user’s knowledge. Hackers can entice users to pair their mobile phone with a computer, and then use the iTunes software on the computer to screen the user’s mobile interface at regular intervals. Then, the hackers can also install or delete applications on the mobile phone. The entire process can happen when the mobile phone user is unaware of the situation, or even can perform remote mobile phone backup, and then extract the relevant data from the backup file.
The use of this software vulnerability requires the use of social engineering, but it is not required. In general, users need to click the pairing confirmation pop-up window on the mobile phone to connect when the mobile phone and the computer are paired. However, when the mobile phone user needs to use a computer to charge, he/she will not hesitate to click to confirm the paired popup window button.
In addition, there is also a situation where malicious software is used to infect a Mac computer and the “Sync with this iPhone over Wi-Fi” function is automatically turned on, and then the iPhone will be attacked as long as it is a paired iPhone. If you use a VPN to connect a Mac computer and a mobile phone to the same Internet, then this kind of attack will rise to Internet attacks.
Symantec said that the current Trustjacking patch has not yet been completed. They reported the vulnerability to Apple. However, Apple’s solution is that when the user is pairing with a computer, the user is prompted to enter a password on the phone. Doing so can reduce the chance that the phone will be randomly paired, but for paired mobile devices, it still cannot prevent hackers from obtaining data from these phones. And currently on the iPhone cannot list all credit devices that have been successfully paired, it is recommended that users for security reasons, or in the iPhone’s settings – General – Reset – reset location information and privacy, remove all trusted devices, so that when there is When the device needs to connect to the phone, it needs to re-grant.





