Iranian APT hacker organisation falsifies Israeli security companies official website to implement phishing activities
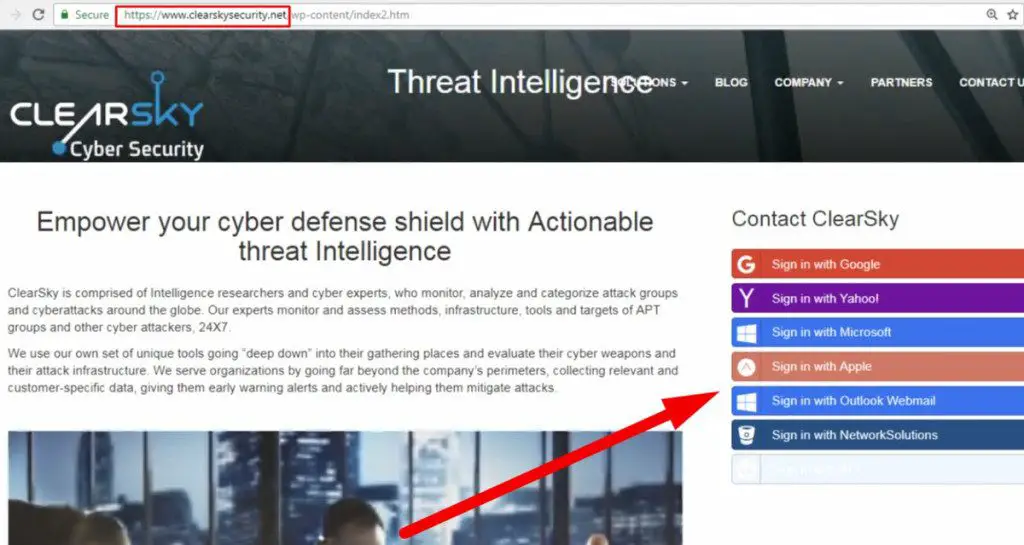
Israeli security company ClearSky Security recently released a report saying that the Iranian APT hacker group Charming Kitten was discovered by the company’s official website for phishing activities, thus revealing its traces.
Charming Kitten is also commonly referred to as Newscaster or Newsbeef, and the associated malicious activities can be traced back to 2014. The organisation was also one of the first Iranian national hacking organisations detected in actual attacks and has been active in recent years. It has launched hacking activities such as Saffron Rose, Newscaster and StoneDrill.
#CharmingKitten built a phishing website impersonating our company. The fake website is clearskysecurity.net (the real website is https://t.co/kdF5RfVA83). They copied pages from our public website and changed one of them to include a "sign in" option with multiple services. pic.twitter.com/3fETo2GTuJ
— ClearSky Cyber Security (@ClearskySec) July 1, 2018
In the early days, the organisation used spear phishing as its attack method and sent attacks against targets located in Iran and the United States. The organisation showed a significant technology upgrade last year. They created a hard disk eraser called “StoneDrill” and used it for attack activities, which means that their attack methods may change significantly in the future.
The last time Charming Kitten appeared in our field of vision was last year when an Iranian named Behzad Mesri sued in the United States for allegedly invading the US cable network media company HBO and stealing the hit TV series “Power The drama resources do not officially broadcast the game. It is worth noting that Behzad Mesri is considered to be a member of Charming Kitten.
Back in this incident, ClearSky pointed out that the organisation cloned its official website and hosted it on clearskysecurity[.]net, while the real ClearSky official website is located on ClearSky[.]com. The organization copied the page from the actual ClearSky official webpage and changed one of the pages to a page with multiple service login options (there is no such option on the real website), and these login options are undoubtedly all connected to the phishing website, which can send the victim’s credentials to the attacker.

Researchers at ClearSky said that when they found the site, it was still under construction, and clicking on specific pages might even bring up an error message. Therefore, the researchers believe that the fishing of Charming Kitten has not been successful. Also, the site did not survive for a long time, it was marked as suspicious by Google’s Safe Browsing API, and was forced to go offline after a few hours.





