Jenkins-Pillage: automatically gathering sensitive information from exposed Jenkins servers
Jenkins-Pillage
This tool will attempt to pull console output, environment variables, and workspaces associated with Jenkins builds. It works both against unauthenticated and authenticated (with creds) servers.
Typically lots of sensitive information may be retrievable from these locations and this tool aims to automate the pillaging of that info. Credentials, API endpoints, private keys, and much more have been gathered using Jenkins-Pillage.
Download
git clone https://github.com/DolosGroup/Jenkins-Pillage.git
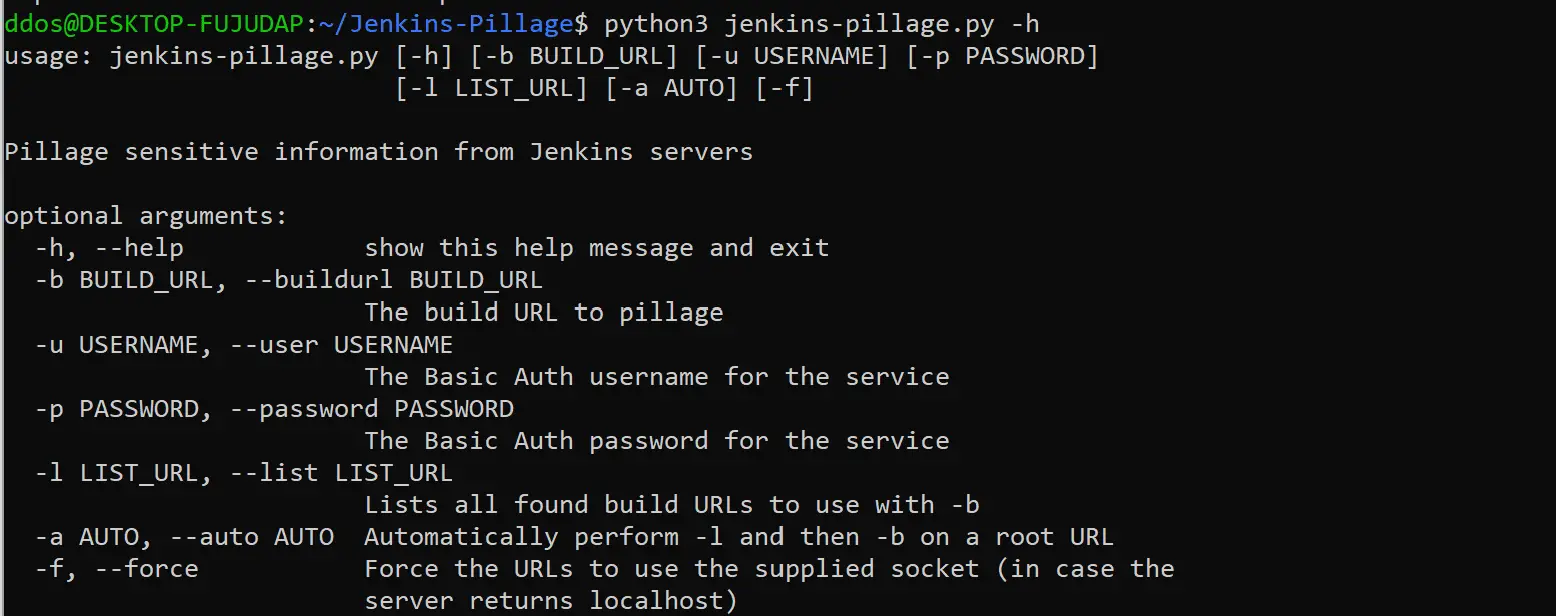
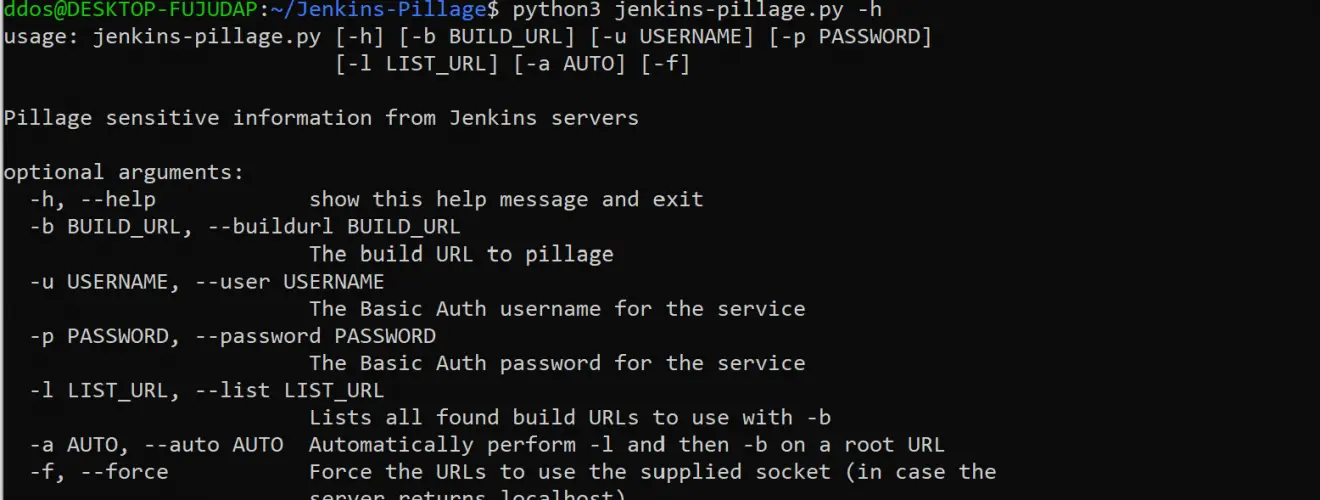
Use
Example
Easy mode:
List all build URLs recursed from a top-level URL:
Pull the console output, workspace zip url, and environment variables of a build recursed from above:
Same but behind an SSH proxy and needs creds to work:
The files are pulled down to the current directory. The URL for the zip download is placed in a file as opposed to downloading the zip because many of the zips I’ve seen can easily fill up your hard drive. Once the files are downloaded, grep to your hearts’ delight:
Copyright (C) 2019 Dolos Group
Source: https://github.com/DolosGroup/