Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
According to a report released by Kaspersky Lab on March 26th, the number of cyber attacks encountered by the energy industry far exceeds that of other industries, and the numerous security vulnerabilities disclosed in 2017 also effectively affected The various products used in this industry.
The security giant Kaspersky analyzed a total of 322 security breaches disclosed by the ICS-CERT, security vendors, and their own researchers in the first half of 2017, including industrial control systems ( Referred to as ICS) and the general software and protocol-related security issues used by industrial companies.
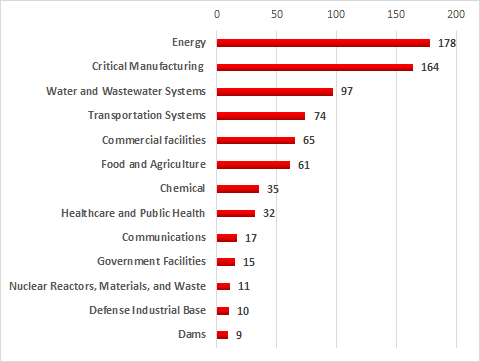
Among them, 178 flaws point to the control systems used by the energy industry. Key manufacturing companies such as raw material metals, machinery, electrical equipment, and transportation equipment manufacturers suffered a total of 164 security flaws.

Image: Kaspersky
Other industries that are significantly affected by security breaches include Water and Wastewater Systems(97), Transportation Systems (74), Commercial facilities (65), Food and Agriculture (61).
A significant portion of the security vulnerabilities disclosed in 2017 was mainly affected by:
- SCADA/HMI components (88),
- networking devices designed for industrial environments (66),
- PLCs (52),
- and engineering software (52).
However, security vulnerabilities affecting various types of general-purpose software and protocols also impact industrial enterprises, including WPA2 KRACK vulnerabilities and multiple bugs that affect Intel’s technical solutions.
By vulnerability type, about 25% of the vulnerabilities are related to the web, and 21% belong to the authentication class problem.
Most security flaws were designated as medium or high severity but according to the relevant CVSS score, only 60 of them were at high risk. Kaspersky noted that all vulnerabilities with a CVSS score of 10 are related to authentication mechanisms and can be easily exploited remotely.
Kaspersky said that there are 265 security holes that can be exploited remotely without authentication, and do not require the attacker to acquire any special knowledge or skills. The company also explained that the specific use of 17 of the security breaches has even been made public on the Internet.
Kaspersky also released data on malware infections and other security incidents. In the second half of 2017, Kaspersky Security Products installed on industrial automation systems detected nearly 18,000 malware variants from approximately 2,400 families. Nearly 38% of corporate industrial control system computers were exposed to malware attacks, a slight decrease from the second half of 2016.
The energy sector is still the victim of the largest vulnerability attack. Nearly 40% of the equipment in energy companies has been targeted.
Kaspersky said that in the vast majority of cases, attempts to infect industrial control system computers are incidental and not part of targeted attacks. Therefore, the functions implemented in such malware are not specific to industrial automation systems. However, even if they do not possess the special functions of industrial control systems, such malware infection problems will also bring serious consequences to the industrial automation system, and even lead to the urgent termination of the production process. For example, under certain circumstances, the WannaCry attack makes the production process short-term. Internal interruption.
Researchers also pointed out that botnets may also pose major threats, including stealing sensitive data, disrupting production processes, causing coding errors, and compatibility damage. In 2017, at least one of the systems monitored by Kaspersky had been attacked by botnets.





