Kaspersky reveals Free Download Manager backdoored, three-year supply chain attack on Linux devices
According to Kaspersky Lab, the Linux application, “Free Download Manager”, has clandestinely been embedded with a backdoor. The software’s download site, freedownloadmanager.org, redirects users to a malicious Debian package repository. This supply chain attack, which persisted for over three years, was unearthed by Kaspersky while probing suspicious domains.
In an official security bulletin regarding the matter, the Free Download Manager team disclosed that since 2020, specific pages on their website appear to have been compromised by a Ukrainian hacker group and were exploited to disseminate malevolent software.

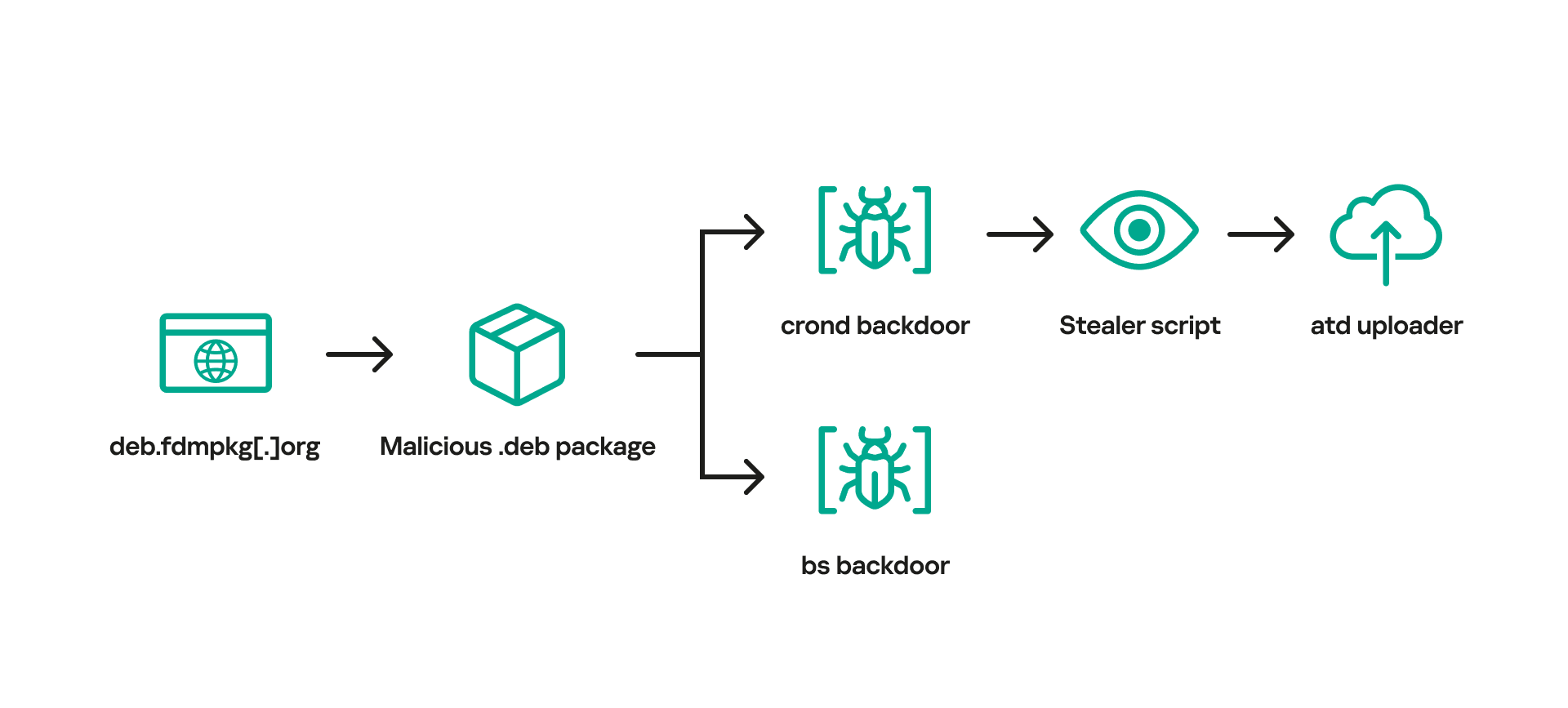
Once installed, this malicious software establishes persistence by invoking the /var/tmp/crond file every ten minutes. The embedded backdoor initiates a reverse shell connection to a C2 server and installs a Bash stealer, designed to harvest system information, browsing history, stored passwords, cryptocurrency wallet files, and credentials from cloud services, such as AWS, Google Cloud, Oracle Cloud Infrastructure, and Azure.
Kaspersky pointed out that the official download page, “freedownloadmanager.org”, sporadically redirects users attempting to download the software to a malicious domain, “deb.fdmpkg.org”, hosting the pernicious Debian package. Such redirections are contingent upon certain, yet undisclosed, criteria, targeting only some users. Over the past three years, there have been discussions regarding suspicious files associated with the software, yet users remained oblivious to the malware infection.
The aforementioned crond backdoor is a variant of the “Bew” backdoor that has been in circulation since 2013, while the Bash stealer was first identified and analyzed in 2019. Moreover, victims of this malevolent operation span across the globe, encompassing countries such as Brazil, China, Saudi Arabia, and Russia. Given this widespread impact, one ponders over its long-standing concealment.
Kaspersky surmises several factors contributed to its obscurity:
- Compared to Windows, malicious Linux software is seldom detected.
- The likelihood of contracting the infected Debian package remains ambiguous; only a minority downloaded the tainted package, while others received the legitimate version.
- Users discussing issues with the Free Download Manager never suspected these anomalies to be malware-induced.
As a precaution, the Free Download Manager’s official stance suggests that if users downloaded and installed the Linux version of the software between 2020 and 2022, they should promptly execute a malware scan on their system and amend their passwords.





