The workflow chart of this rootkit malware | Source: FGIR
The FortiGuard Incident Response (FGIR) team has conducted a comprehensive analysis of a sophisticated Linux rootkit, shedding light on how it leverages kernel modules and user-space binaries to hijack network traffic and execute malicious commands on compromised systems. Dubbed sysinitd, this rootkit exemplifies the advanced tactics employed by attackers to maintain persistence and evade detection.
The rootkit was discovered during an investigation into a zero-day exploit where attackers exploited multiple vulnerabilities in an appliance. According to FGIR, “The remote attacker had deployed a rootkit (a loadable kernel module, sysinitd.ko) and a user-space binary file (sysinitd) on the affected system by executing a shell script (Install.sh).” Entries were also added to the /etc/rc.local files to ensure persistence upon system startup.
The sysinitd.ko module serves as the core of this rootkit’s operations. It initializes upon being loaded into the kernel via the insmod command and performs critical setup tasks, including registering a Netfilter hook function to intercept network packets. This hook operates at the NF_INET_PRE_ROUTING stage, “a hook point in the Linux kernel’s Netfilter framework where incoming packets are intercepted before any routing decision is made.”
One of the rootkit’s standout features is its ability to process and hijack TCP traffic. It identifies attacker-originated packets, known as attack-init packets, which contain specific flags and verification data. Once verified, the kernel module records the source and destination IP addresses and ports, allowing subsequent communications to bypass standard security checks. Encryption can also be enabled for these interactions, making them harder to detect.
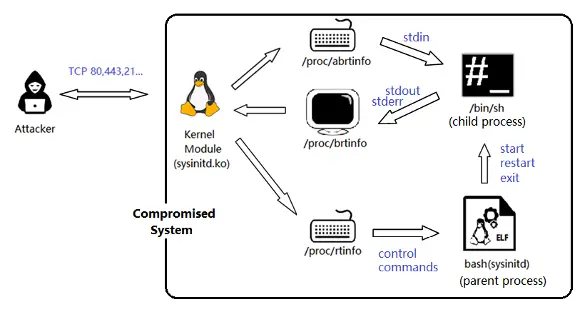
The sysinitd binary, installed in /usr/share/empty/, is activated by the kernel module. It masquerades as the legitimate bash shell process, a tactic to evade casual inspection by system administrators. The FGIR team noted, “The sysinitd process is started by the kernel module. It disguises itself as a bash program by replacing its process name with ‘bash.’” The binary interacts with procfs entries created by the kernel module to process commands and execute attacker-controlled tasks.
The rootkit establishes a dual-process architecture: a parent process that manages system control commands and a child process that processes attacker-sent Linux commands. Control commands are sent via procfs entries, allowing attackers to restart, kill, or send signals to these processes. This mechanism ensures robust and stealthy control over the compromised system.
To defend against such threats, FGIR emphasizes the importance of rigorous monitoring and auditing. Their analysis concluded with a warning: “The attacker can now remotely execute any command with root privilege on the compromised system through the malicious kernel module (sysinitd.ko) and the child process (sysinitd -> /bin/sh).” Regular patching, robust network monitoring, and kernel integrity checks are critical to mitigating such attacks.
Related Posts:
- New Undetected Diamorphine Rootkit Targets Linux Systems
- Driver Signature Enforcement Cracked: OS Downgrade Attacks Possible on Windows
- Kernel Modules and Malicious Commands: Anatomy of the sysinitd Rootkit