Kromtech Reveals Two Data Breach involving Honda and Universal Music
The Kromtech Security Center disclosed two data breaches on Wednesday (May 30th). The main body of the incident included Honda Motors’ (HONDA) subsidiary in India, Honda India, and Universal Music Group,UMG.
Among them, Honda India leaked personal details of more than 50,000 customers due to insecure AWS S3 buckets, while

Universal Music was exposed by its contractors, exposing its internal FTP credentials, database root passwords, and AWS configuration details, including access keys and passwords.
Kromtech Security Center stated that Honda Motor India accidentally stored personal details of more than 50,000 Honda CONNECT mobile app users in two publicly accessible Amazon S3 buckets, this makes it possible for hackers to steal this data.
Honda CONNECT, a new generation of navigational interconnection systems jointly developed by the Gold German Group. It provides users with diversified services such as precision navigation, online entertainment, information transmission, and emergency rescue, allowing users to interact with their own cars through the Honda CONNECT mobile application, and contracting and interacting with services provided by Honda Motor Company.
Over time, the application has collected and stored a large amount of information about users and their cars so far. Bob Diachenko, a researcher at the Kromtech Security Center, found that publicly accessible information includes the names of users and their trusted contacts, phone numbers, password, gender and email address, as well as information about their car, including VIN, Connect ID, etc.

Image: kromtech
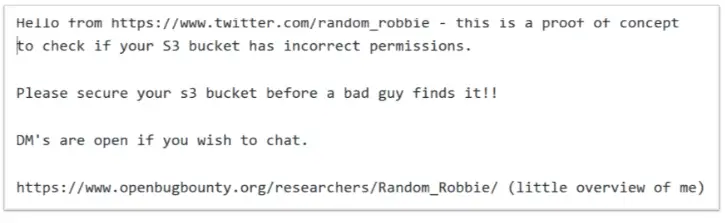
It is worth noting that Diachenko was not the first to discover the two buckets. Diachenko said that when he discovered the two buckets, they already contained a file called “poc.txt” with security information.
 Image: kromtech
Image: kromtech
From the contents of the document, it was created by a security researcher named Robbie Wiggins on February 28 this year. For nearly a year, Wiggins has been scanning AWS S3 buckets on the Internet and has left this information in insecure buckets. Wiggins has been doing so to remind bucket owners that they should take protective measures before data is destroyed.
The good news is that the company has responded to this issue and the insecure AWS S3 bucket has been properly protected.
Experts at Kromtech Security Center discovered that due to two unprotected Apache Airflow server instances, Universal Records cloud data storage contractor Agilisium unexpectedly exposed the company’s internal FTP credentials, AWS configuration details (access keys and passwords), and Internal source code details (SQL password).
Apache Airflow is a platform for programmatically writing, scheduling, and monitoring workflows based on Python. By default, Airflow is completely open. This is usually stated on the first line of the security document, which means that the user must perform some setup steps to protect the server. Obviously, Agilisium skipped these steps and inadvertently exposed everything.
After contact with Universal Music, the company responded quickly and solved the problem.





