Latin America Under Siege: Phishers Weaponize Fake Suspended Domains
Latin American businesses and individuals, beware! An orchestrated phishing scheme has surfaced, exploiting the illusion of suspended web pages to deliver a nasty payload of malware. Security experts at SpiderLabs recently uncovered this threat, and what they found is a chilling testament to the ingenuity of cybercriminals.
The Scheme: A Digital Decoy
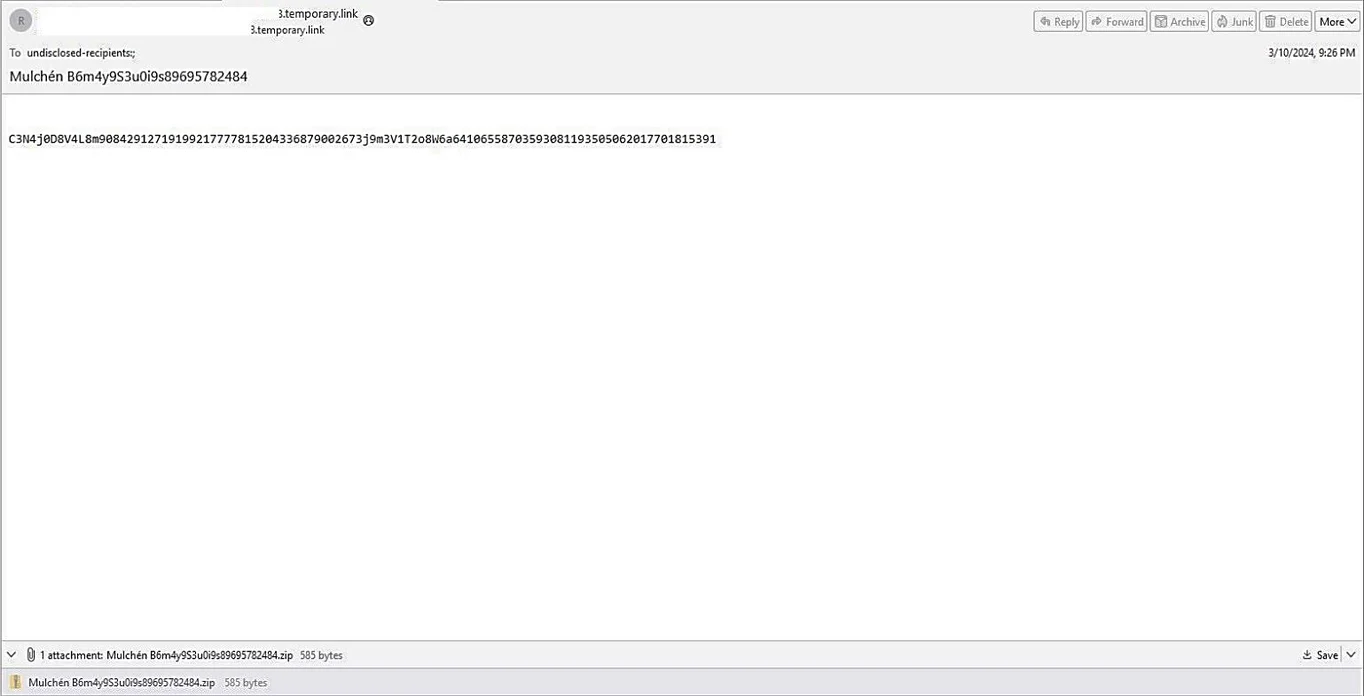
Phishing email sample with zip file attachment | Image: SpiderLabs
The campaign commences with a seemingly innocuous phishing email, containing a ZIP file that masquerades as an invoice. Upon extraction, recipients find an HTML file that, rather than leading to legitimate content, serves as a gateway to a malicious download. SpiderLabs’ analysis reveals that the email employs a clever ruse, using the domain ‘temporary[.]link’ in the email address and leveraging Roundcube Webmail in the User-Agent header—both characteristics commonly exploited in phishing activities.

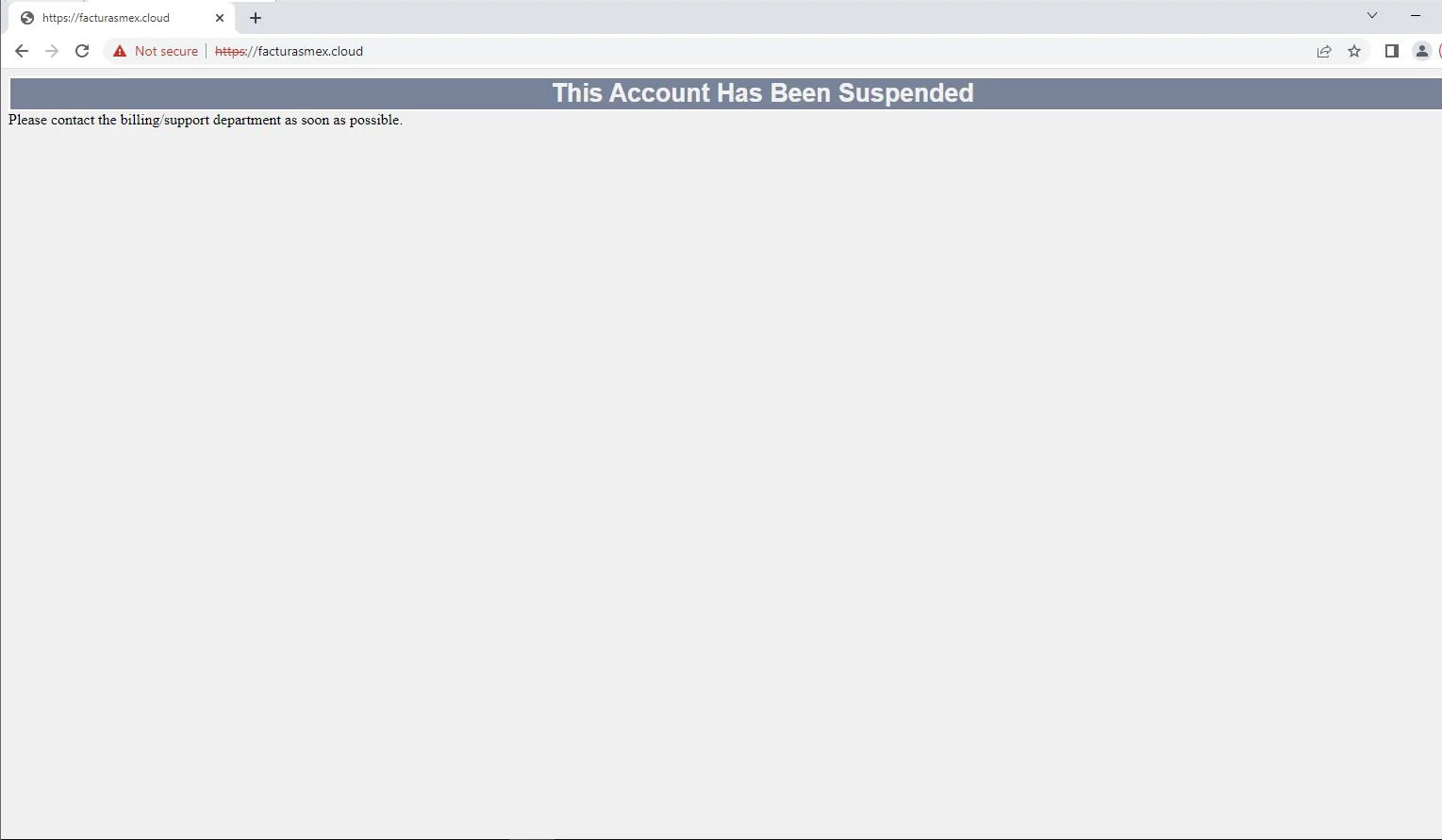
Suspended page when access in a different region | Image: SpiderLabs
The attached HTML file hides its nefarious intentions through a concatenated URL that ordinarily points to a suspended page. However, the plot thickens upon delving deeper into the URL’s origins, hosted on an IP suggestive of prior malicious use. The domains involved, marked by their youth (approximately one-year-old), employ Cloudflare’s name servers, with registrant contacts traced back to Mexico. This geographic specificity plays a pivotal role in the scam’s execution.
The Payload: A Multi-Stage Attack
Should individuals from Mexico attempt to access the URL, they’re redirected to a captcha page, ostensibly designed for human verification. This step leads to a further URL that prompts the download of an RAR file laden with malicious intent. The file contains a PowerShell script engineered to harvest sensitive information from the victim’s machine, including the computer’s name, operating system details, and antivirus presence.
SpiderLabs’ analysis doesn’t stop there. Within the script, several base64 encoded strings conceal additional malevolent URLs. Decoding one such string unveils a request that seeks to ascertain the user’s country, potentially to tailor subsequent attacks. Another decoded string reveals a URL pointing to Dropbox, from which a ZIP file packed with suspicious files can be downloaded. This ZIP file, a mix of newly modified and notably older files, includes an executable AutoIt file, a hallmark of the “Horabot” campaigns previously observed by cybersecurity experts.
This campaign’s ingenuity lies not only in its use of obfuscated code and PowerShell scripts—tools often leading to malware downloads—but also in its geographical targeting. By employing newly created domains that exhibit different behaviors based on the user’s location, the threat actors aim to evade detection while honing in on their intended victims.
Old Dog, New Tricks
This elaborate phishing campaign bears a chilling resemblance to previous “Horabot” attacks, showing that cybercriminals are always adapting and evolving their tactics.
Protecting Yourself
- Think Twice: Be incredibly cautious of emails with attachments, even if they seem to come from a legitimate source.
- Verify Before You Click: If a link looks suspicious, don’t let curiosity get the better of you. Hover your mouse over it to see the true destination or contact the supposed sender directly.
- Beware of Errors: Don’t dismiss “suspended” pages as harmless. If something feels off, especially if it arrived in your inbox, trust your instincts.
- Stay Updated: Make sure your antivirus and security software are running and updated to catch the latest threats.





