Leak: NSA and US Army can capture Tor, I2P, VPNs to monitor Monero users
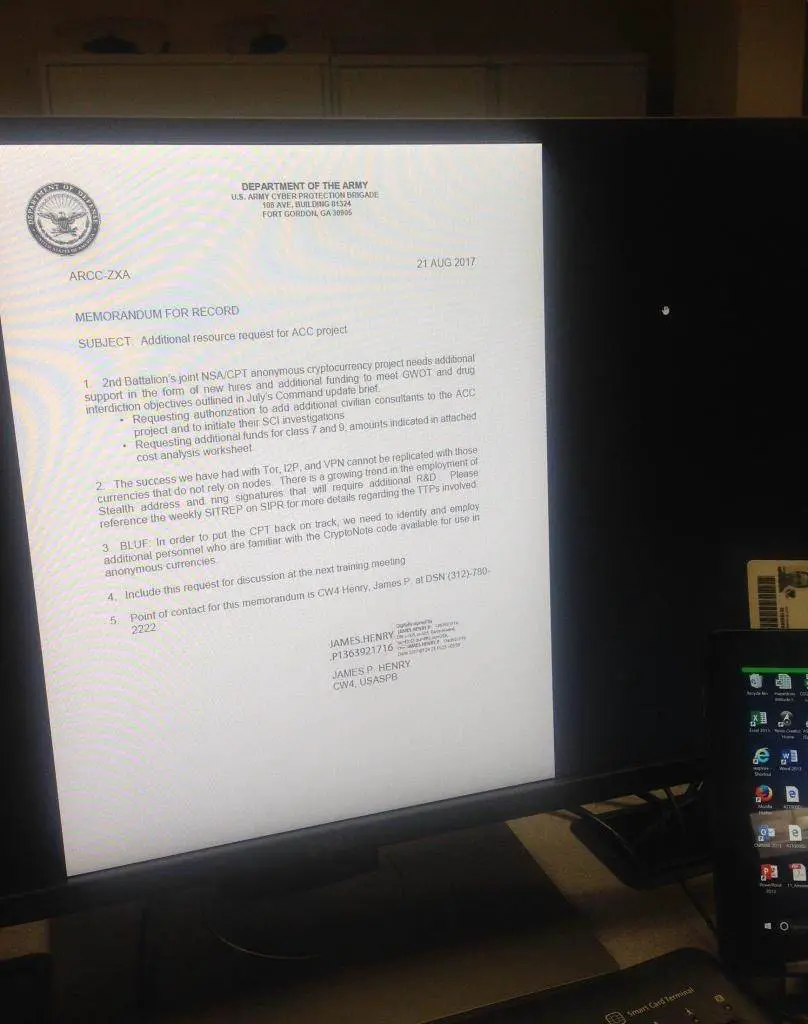
According to securityaffairs media reported on February 5 that a piece of online memorandum photos reveal some of the sensitive information of the US Army Network Protection Team (CPT) and the U.S. National Security Agency (NSA): These include disclosure of Tor, I2P, VPN users, and tracking Monroe coin joint project.
Anonymous networks are crucial to combat censorship and ensure freedom of expression, so researchers pay particular attention to the intent of these tracking activities.
The researchers found that the memorandum clearly pointed out the difficulties in leaking CryptoNote-based cryptocurrencies.
CryptoNote is an application-layer protocol implemented in several decentralized and privacy-oriented digital currency schemes that requires the allocation of additional resources to track Monero (XMR), Anonymous Electronic Online Coin (AEON), DarkNet Coin (DNC), Fantomcoin (FCN) And Bytecoin (BCN) and other anonymous cryptocurrencies.
U.S. authorities have pointed out that Monero may be the primary cryptocurrency among underground criminals. In addition, relevant security experts said US intelligence also uses internal resources to conduct surveillance activities on the blockchain.

After DeepDotWeb researchers verified the evidence from some stakeholders, the memorandum information is likely to be true. However, Tor, I2P, and VPN do not seem to be fully mastered by intelligence agencies. Although attackers have proposed and implemented techniques to expose users, these technologies are not very effective for monitoring operations.
According to a document disclosed by Edward Snowden, the NSA can screen VPN solutions based on vulnerable VPN protocols such as PPTP, but VPNs that rely on OpenVPN may not be affected. It is unclear who disclosed the memo, but speculation is likely to be deliberately released.
Source: SecurityAffairs



