LightSpy Malware Strikes macOS: Your Mac Could be the Target
Researchers at Huntress have revealed a critical development in the LightSpy malware threat landscape. Previously focused on iOS and Android, this newly analyzed macOS variant confirms cybercriminal interest in compromising Apple systems. This calls for a heightened focus on macOS security measures, especially for organizations with a mixed-device environment.
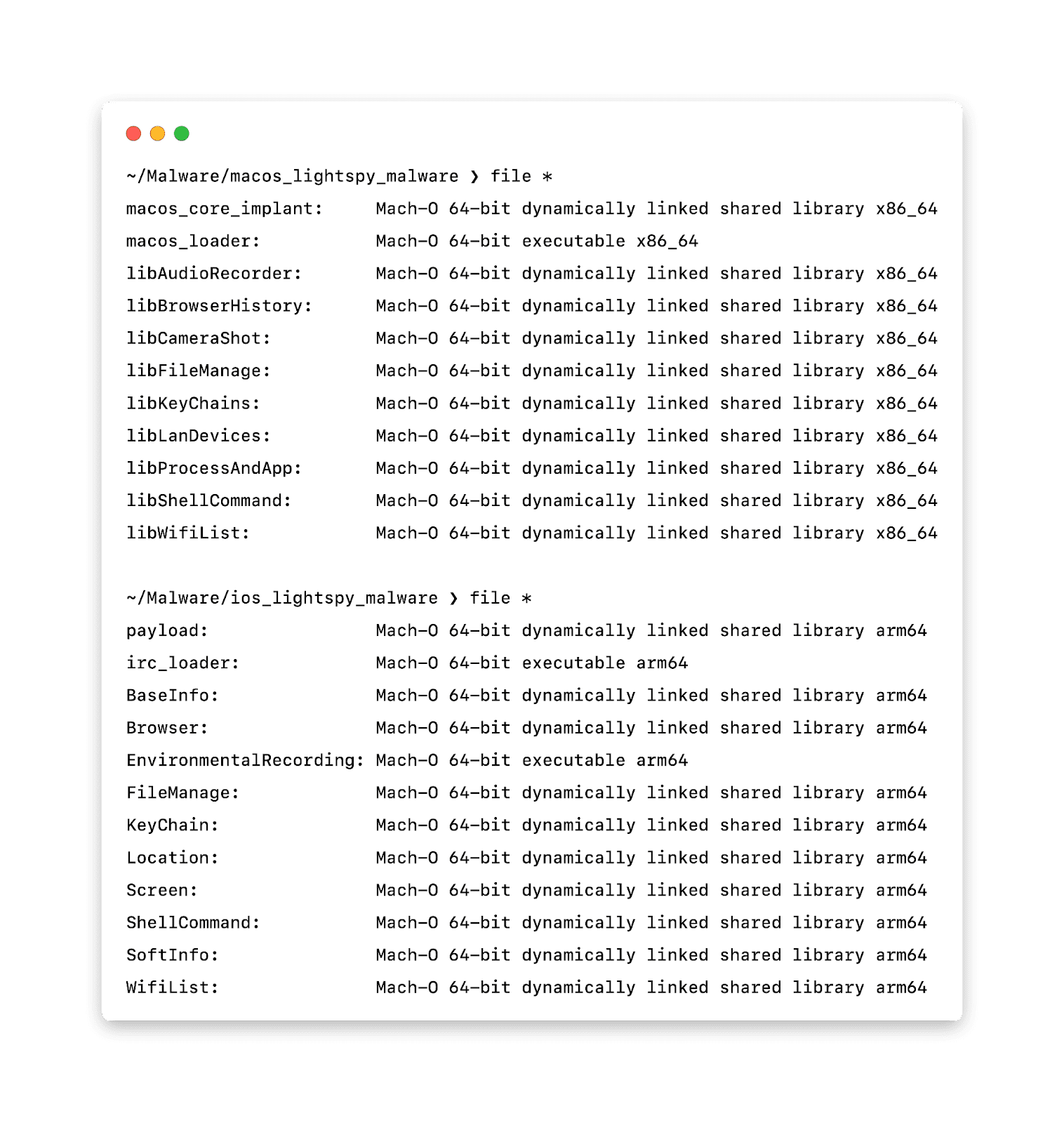
Initially, the BlackBerry analysis suggested that a new VirusTotal upload of the LightSpy mobile spyware was an iOS implant. Major publications like Forbes, HackerNews, and Mashable echoed this claim, which led to widespread misinformation about the nature of the threat. However, Huntress researchers have clarified that the malware sample is designed exclusively for macOS, specifically targeting Intel macOS devices or Apple Silicon devices running Rosetta 2.
Technical Breakdown of the macOS Variant
Architecture and Operation

The LightSpy macOS variant is compiled for the x86_64 architecture, which is fundamentally incompatible with the ARM architecture used in iPhones. This malware employs a multi-stage attack process:
- Stage 1: Dropper – The initial dropper sets up the infection by downloading a core implant dynamic library (dylib), similar to DLLs on Windows platforms.
- Stage 2: Implant – The core implant is responsible for loading various plugins that enhance the functionality of the malware, conducting espionage, and maintaining persistence.
- Stage 3: Plugins – These additional payloads are tailored to perform specific tasks, thereby extending the capabilities of the malware.
Operational Security and Development Practices
The macOS version of LightSpy showcases improved operational security and mature development practices. It utilizes a plugin manifest for updating plugins, which helps lower static detections and provides flexibility in operations. Despite these improvements, the malware still leaves traces that facilitate anti-analysis efforts, such as developer artifacts found within the binaries.
Differences from the iOS Version
Unlike its iOS counterpart discovered in 2020, the macOS variant appears more refined, with modifications that suggest a distinct evolution in the malware’s development. For instance, it does not collect data specific to mobile devices like IMSI or IMEI numbers and uses a different method for gathering device information.
Security Implications and Recommendations
The discovery of the macOS variant of LightSpy is a critical reminder of the need for continuous vigilance and adaptation in cybersecurity defenses. macOS users, often perceived as less vulnerable to malware, are clearly at risk from sophisticated spyware like LightSpy. Recommendations for users and administrators include:
- Regular Updates: Keep all systems and software up to date to mitigate vulnerabilities.
- Enhanced Monitoring: Implement advanced monitoring solutions to detect unusual activities indicative of malware operations.
- Use of Detection Tools: Employ YARA and Sigma rules, as provided by Huntress researchers, to detect potential usage of this malware variant.



