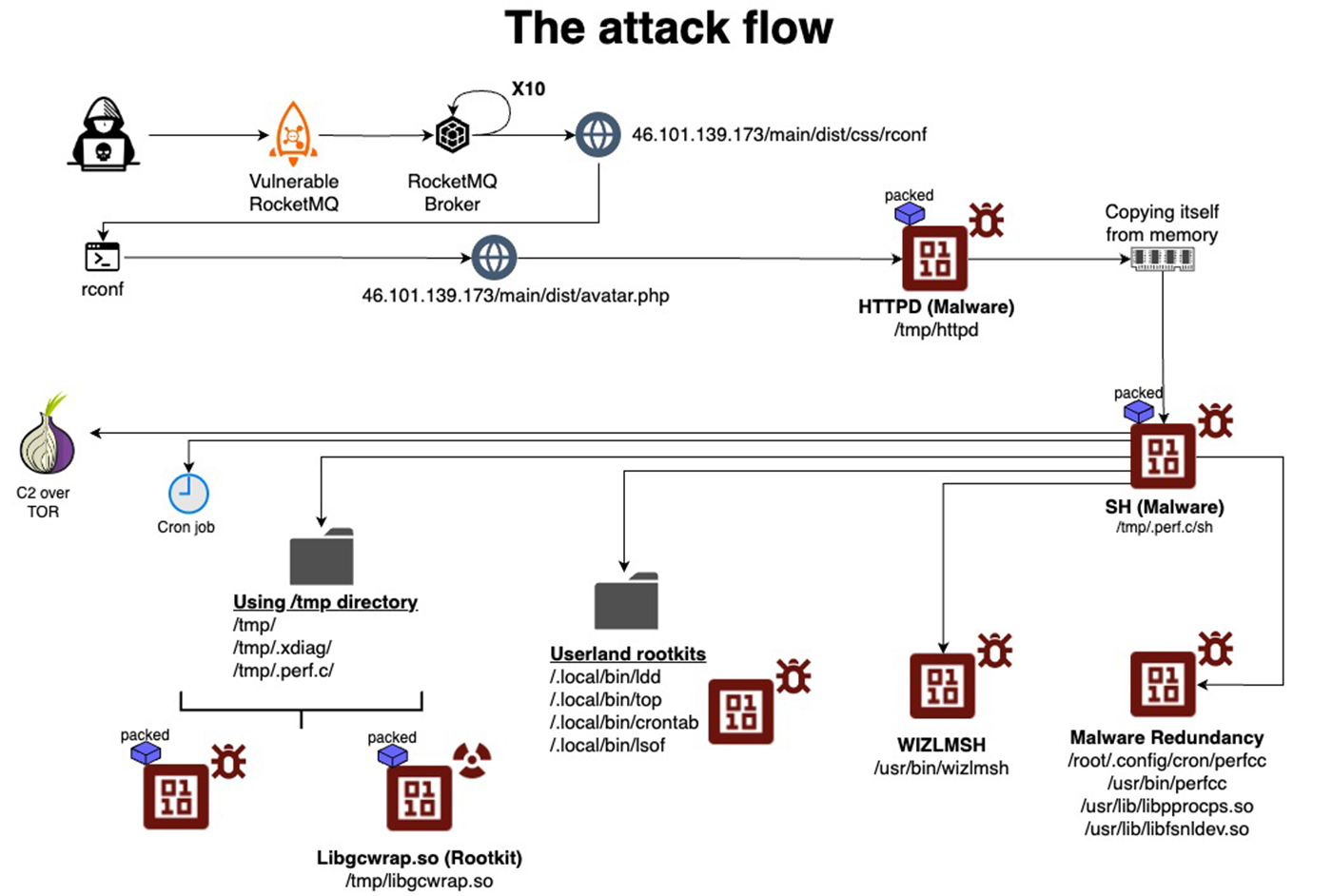
The entire attack flow | Image: Aqua Nautilus
In a recent report by Aqua Nautilus researchers Assaf Morag and Idan Revivo, the Linux server community has been alerted to the presence of a particularly stealthy and dangerous malware: perfctl. Active for the past 3-4 years, this malware has exploited over 20,000 types of server misconfigurations, potentially impacting millions of Linux servers worldwide.
The perfctl malware is designed with resilience in mind. Once it compromises a server, the malware can lie dormant when the server is in use, only activating when it detects idle periods. According to Aqua Nautilus, “when a new user logs into the server, it immediately stops all ‘noisy’ activities, lying dormant until the server is idle again.” This allows the malware to avoid detection during typical system checks.
Perfctl uses rootkits to further conceal its activities, masking its presence from system utilities. It exploits vulnerabilities, including the Polkit vulnerability (CVE-2021-4043), to escalate privileges and gain deeper control over the infected system. It even copies itself to various directories under deceptive names, such as libpprocps.so and libfsnkdev.so, to ensure persistence and disguise itself as a legitimate process.
One of the key purposes of perfctl is to hijack system resources for cryptomining, specifically utilizing Monero (XMRIG) cryptominers. The malware aggressively drains the infected system’s CPU power, often going unnoticed due to its clever masking of activity. According to the report, in all observed cases, “the cryptominer is packed and encrypted, communicating with cryptomining pools via the TOR network.” This adds an extra layer of obfuscation, making it even more difficult to track the illicit activity.
Perfctl goes beyond just cryptomining—it also opens backdoors on infected servers, allowing threat actors to maintain control and potentially deploy additional payloads, such as proxy-jacking software. The malware’s ability to persist is particularly alarming, as it modifies essential server files like ~/.profile to ensure that it reactivates even after reboots. The report highlights the malware’s persistence, noting that it “modifies the ~/.profile script, ensuring the malware runs first during user login”
Despite its widespread impact, perfctl remained elusive for years. Numerous reports have surfaced in online forums such as Reddit and Stack Overflow, where developers reported unusual system behavior linked to the malware. Many of these reports pointed to high CPU usage and performance issues, but few linked the issues to perfctl specifically, as its name is designed to blend in with common Linux system processes.
Detecting perfctl is no easy feat, but Aqua Nautilus provides some critical recommendations. Admins should inspect suspicious binaries, especially those in directories like /tmp, /usr, and /root. It’s also essential to monitor processes for high resource usage and to capture network traffic for TOR-based communications.
As Linux servers continue to power critical infrastructure worldwide, administrators must remain vigilant, update systems regularly, and watch for signs of compromise to mitigate the risks posed by perfctl.
Related Posts:
- Cryptojacking Campaign Exploits Atlassian Confluence CVE-2023-22527 Vulnerability
- Hackers are actively exploiting PHP RCE vulnerability (CVE-2024-4577)
- Log4j Campaign Exploited to Deploy XMRig Cryptominer
- Openfire Bug (CVE-2023-32315) Exploited to Deploy Kinsing Malware and Cryptominer
- RedTail Cryptominer Malware Targets PAN-OS Vulnerability