Linux Systems Targeted: Open-Source Pupy RAT Exploited in Attacks Across Asia
A potent Remote Access Trojan (RAT), known as Pupy, is being actively weaponized in attacks targeting Linux systems across Asia, including South Korea. Security researchers at AhnLab Security Emergency Response Center (ASEC) have recently uncovered sophisticated operations utilizing Pupy along with a new variant called Decoy Dog.

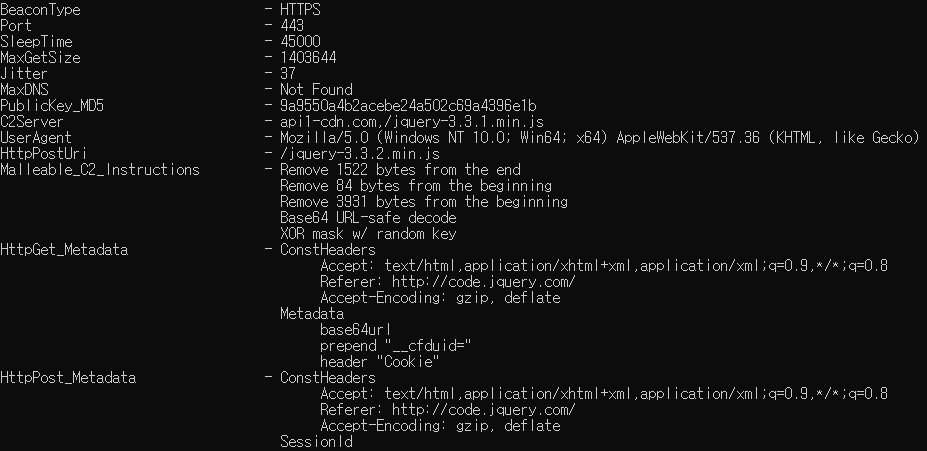
Cobalt Strike believed to have been distributed by the same threat actor | Image: ASEC
Pupy RAT, an open-source malware originally published on GitHub, is versatile, supporting multiple platforms including Windows, Linux, Mac OSX, and Android. Its design is based on C and Python, allowing for widespread adoption and modification by malicious actors. Unlike conventional RATs, Pupy provides extensive capabilities for command execution, file manipulation, and information theft, including screen captures and keylogging.
A distinguishing feature of Pupy RAT is its support for post-exploitation modules, which enable attackers to conduct further harmful activities such as privilege escalation, credential theft, and lateral movement within compromised networks. For Linux systems, Pupy RAT typically masquerades as normal processes like “/usr/sbin/atd” to evade detection.
The analysis highlights the emergence of Decoy Dog, an advanced version of Pupy RAT, which has recently been implicated in sophisticated attacks against corporate networks in Russia and Eastern Europe. This iteration represents a significant evolution in the malware’s capability, emphasizing the ongoing threat to Linux systems—a platform often considered more secure against such attacks.
Pupy RAT has been actively involved in cyberattacks across Asia, with notable activities in Taiwan, Hong Kong, Singapore, Japan, and Thailand. These attacks have persisted from 2021 to the present, often using malware strains distributed under names like “nptd” or “kworker”. Attack vectors include spear phishing and websites disguised as legitimate software download pages.
Concerningly, Pupy has sometimes been found sharing command and control (C2) servers with Cobalt Strike, a commercial penetration testing toolkit frequently abused by cybercriminals.
In South Korea, Pupy RAT continues to be a significant threat, with instances of the malware being distributed alongside other well-known backdoors such as PlugX. Such activities date back to as early as 2019, with recent distributions noted on a now-defunct Korean Windows utility-sharing website.
Pupy RAT exemplifies the dual-edged nature of open-source software in cybersecurity. While it provides a platform for learning and development, it also serves as a potent tool for cybercriminals. The continual adaptation and use of Pupy RAT, especially its deployment on Linux systems, is a clear indicator of the need for robust cybersecurity measures. Organizations must prioritize regular system updates, vulnerability assessments, and educating users about potential phishing attempts to mitigate these threats effectively.





