Lynx Ransomware: The Evolution of INC Ransomware into a Potent Cyber Threat
Palo Alto Networks has discovered a new ransomware threat actor dubbed “Lynx” that is actively targeting organizations in various sectors across the U.S. and UK. This new malware is not entirely new, though; it is, in fact, a rebranding of INC ransomware, a ransomware family that surfaced in August 2023.
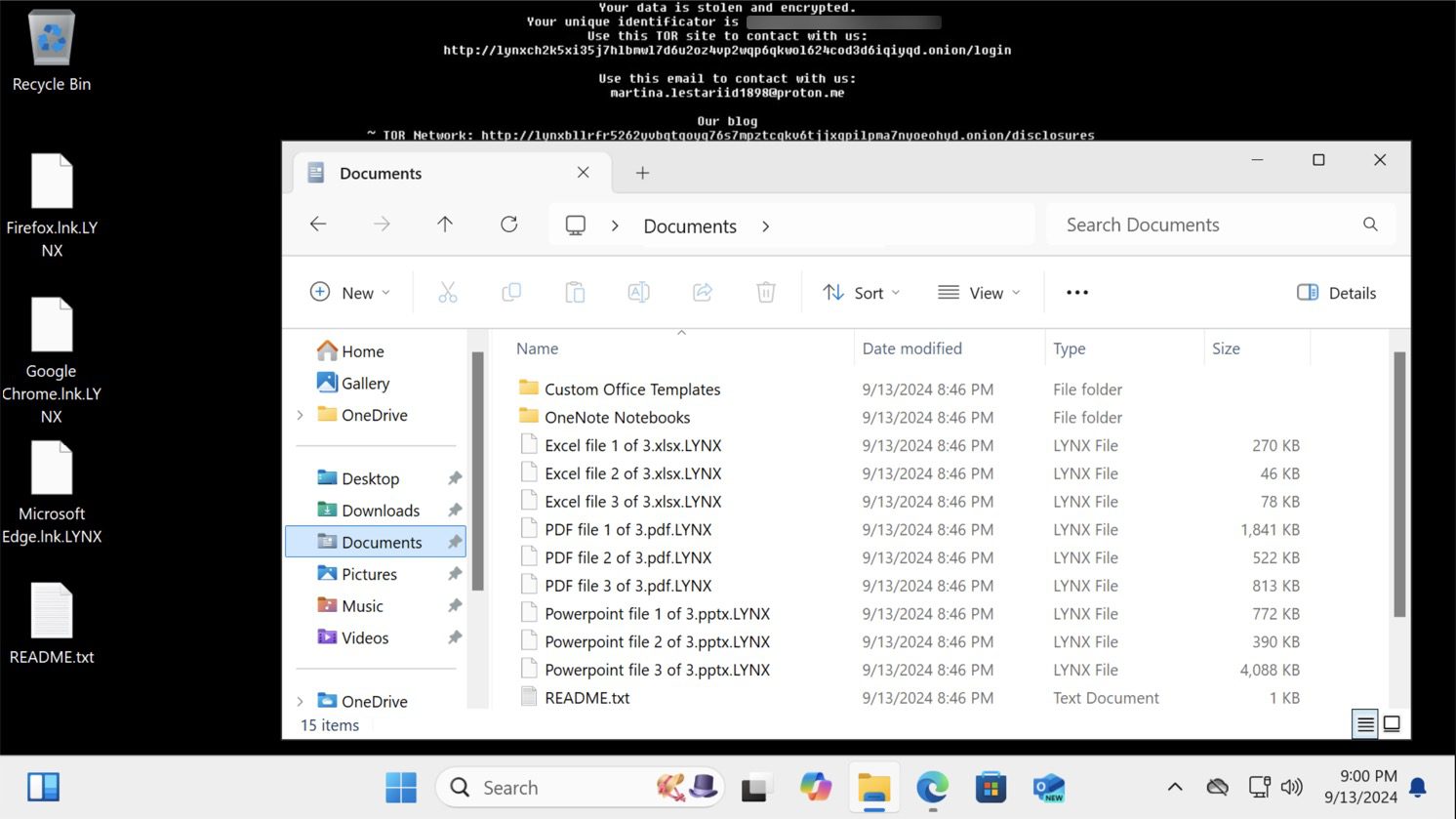
Since its emergence, Lynx ransomware has made waves, targeting a wide array of sectors, including retail, real estate, architecture, and financial services. This variant operates as ransomware-as-a-service (RaaS), making it available to other cybercriminals who wish to deploy it in their attacks. The malicious actors behind Lynx ransomware have employed sophisticated techniques, including double extortion tactics, where they exfiltrate victims’ data before encrypting it. If the ransom is not paid, the stolen data may be leaked or sold on the dark web.
Lynx ransomware’s lineage can be traced directly to INC ransomware, with which it shares an estimated 48% of its code. This close resemblance was confirmed by using the open-source tool BinDiff to compare both malware strains. Palo Alto Networks found that many of the core functions—around 70.8%—were reused, making it clear that the Lynx developers heavily relied on INC’s codebase.

Code similarity between INC and Lynx ransomware as shown by BinDiff | Image: Palo Alto Networks
This reliance on preexisting ransomware code is not unusual in the world of cybercrime. As the report points out, “By leveraging preexisting code and building upon the foundations laid by other successful ransomware, threat actors can save time and resources,” allowing them to launch attacks more quickly and efficiently. This reuse of code has led to the rapid proliferation of ransomware families, a trend likely to continue as more source code becomes available on underground markets.
One of the most dangerous aspects of Lynx ransomware is its implementation of double extortion. Victims not only face encrypted files but also the risk of their sensitive data being exposed. The group behind Lynx has claimed to have breached numerous companies, displaying pilfered data on a public website. While they assert they avoid government institutions, hospitals, and non-profit organizations, their attacks still represent a significant threat to many industries.
Palo Alto Networks emphasized the wide range of vectors through which Lynx ransomware is deployed, including phishing emails, malicious downloads, and the sharing of resources on hacking forums. As such, organizations must be vigilant in defending against these multifaceted threats.
The technical analysis of Lynx ransomware revealed its use of advanced encryption algorithms, including AES-128 in CTR mode and Curve25519 Donna, making it exceptionally difficult to decrypt without paying the ransom. It is designed to target Windows systems and has been observed using the Restart Manager API (RstrtMgr) to enhance its encryption efficiency, a technique also used by other notorious ransomware families like Conti and Cactus.
Moreover, Lynx ransomware is designed with flexibility in mind, allowing attackers to customize their execution through various command-line arguments. This enables them to tailor the attack to their specific needs, whether encrypting particular directories, network drives, or services.

Command-line options present in the malware | Image: Palo Alto Networks
The emergence of Lynx ransomware underscores the ever-evolving nature of cyber threats. Organizations need to stay vigilant and proactive in their cybersecurity measures to mitigate the risk posed by such threats.





