Mac Users Beware: Atomic Stealer Strikes Again

Bitdefender researchers have uncovered a new, stealthy variant of the infamous Atomic Stealer malware specifically targeting macOS users. This updated version uses sophisticated techniques to hijack passwords, browser data, cryptocurrency wallets, and other sensitive information. If you’re a Mac user, it’s crucial to understand this evolving threat and how to protect yourself.
A New Variant Emerges from the Shadows
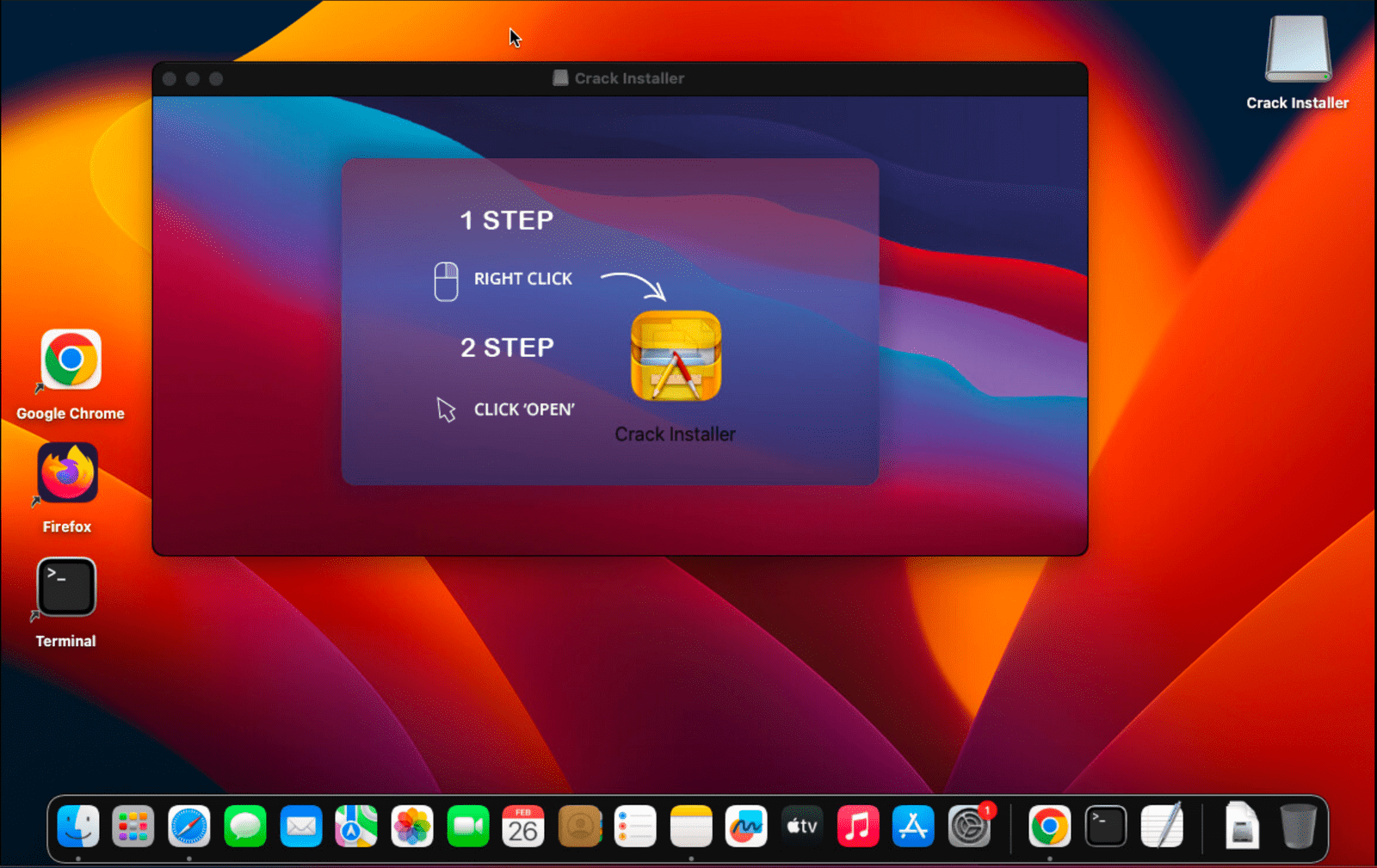
Image: Bitdefender
Bitdefender has unearthed multiple macOS disk image files, each surprisingly small at 1.3 MB, harboring a new variant of the AMOS (Atomic) Stealer. This discovery is significant, not only for its implications on macOS security but also for the insights it provides into the evolving tactics of cyber adversaries. The new variant, like its predecessors, focuses on covert operations, employing a Python script to remain undetected while executing its nefarious activities.
How the Attack Unfolds
- The Disguise: The initial entry point is a deceptively small disk image file (DMG). Threat actors know many people assume smaller files are less dangerous, potentially allowing the malware to bypass initial security checks.
- Social Engineering Trap: Once opened, the DMG prompts the user to ‘right-click and open’ an included application. This attempts to override Apple’s Gatekeeper security, which normally warns against unsigned software.
- Hidden Python Payload: Upon execution, the embedded app drops a Python script – a less common tactic for Mac malware – that carries out the core malicious activity. Python can be harder for traditional security tools to analyze, providing an extra layer of stealth.
- The Password Ruse: In an audacious move, the malware masquerades as a system update, prompting the user to enter their Mac account password. If entered, your most important login credential is immediately compromised.

Image: Bitdefender
- File Hunt with Enhanced Efficiency: What sets this variant apart is its sophisticated use of Python and Apple Script code to pilfer sensitive information from victims. The malware meticulously targets browser data, crypto-wallet extensions, and files with specific extensions from the Desktop and Documents directories. It doesn’t stop there; the Atomic Stealer also goes as far as to steal the local user account password through a deceptive system update prompt, showcasing the depth of deceit employed by its operators.The inclusion of Apple Script is a notable evolution in the malware’s arsenal, allowing it to execute a more developed script for collecting sensitive files, including those from the Safari browser’s cookie store. This method not only underscores the malware’s adaptability but also its focus on maximizing the extraction of valuable information from compromised systems.
Cryptocurrency: A Prime Target
In line with the growing interest in cryptocurrency, the Atomic Stealer has sharpened its focus on crypto wallets and related data. By targeting specific directories associated with popular crypto wallets like Electrum, Coinomi, Exodus, and Atomic, the malware underscores the financial motivations driving its deployment. This approach not only threatens the privacy and security of individuals but also poses a significant risk to their financial assets.
The Challenge of Detection and Mitigation
The discovery of this new variant of Atomic Stealer highlights the ongoing challenge of detecting and mitigating malware threats on macOS, a platform often mistakenly perceived as being more secure than others. Bitdefender’s revelation of the malware’s tactics, techniques, and procedures (TTPs) is a crucial step in combating this threat. By sharing Indicators of Compromise (IoCs) and employing advanced detection capabilities, Bitdefender is leading the charge in protecting users from this stealthy adversary.





