Maikspy Spyware spreads through adult games and targets Windows and Android users
Trend Micro announced in its blog post on Tuesday (May 8th) that its mobile threat response team has discovered a malware family named “Maikspy”, a dual platform that can steal sensitive personal data from victims. Spyware. Specifically, it targets Windows and Android users. The original version dates back to 2016 and is disseminated through adult game applications named after the American adult movie actress.
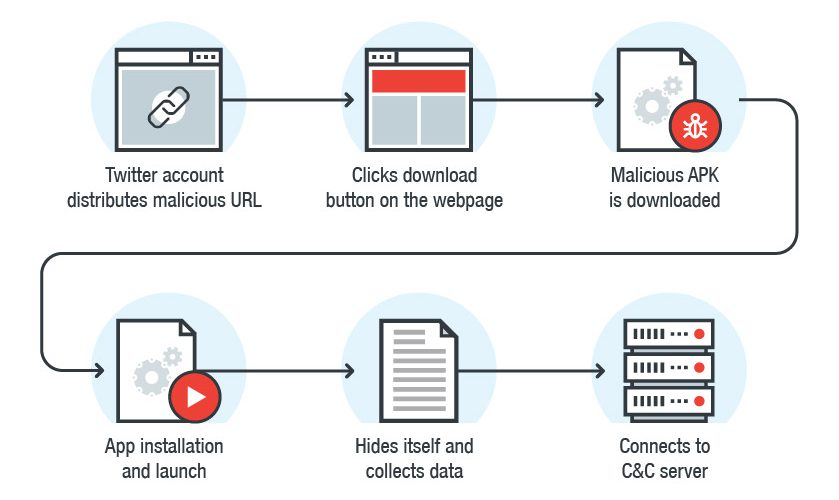
An analysis of the latest Maikspy variant shows that a malicious application for the spread of spyware – an adult game application called “Virtual Girlfriend” – will pass through an adult game site (miakhalifagame[.] Com) is downloaded. Trend Micro found that a Twitter account is actively promoting the game and sharing links to malicious websites through short links.
The latest sample was discovered in March of this year. This Maikspy variant (detected by Trend Micro as AndroidOS_MaikSpy.HRX) is targeted at Android users. Advertising campaigns use “virtual girlfriend” adult games to lure victims to visit malicious websites controlled by attackers.

When the victim opens a short link to the domain on Twitter, a page showing a gender selection button appears. After selecting OK, the other lets the victim select their “first girlfriend” and guides them to the download page.
When the downloaded APK file is installed and started, it will send the Unix timestamp of the infected device to the phone number containing the Swedish code (0046769438867). Trend Micro believes that this is probably the ID registration for the device.
The malicious application first checks for the required permissions and then continues to execute its routines:
- Steal phone number
- Stealing account information
- Steal a list of installed application names
- Stealing contacts
- Steal SMS
The stolen information will be written in .txt or .csv format before being uploaded to the Command and Control (C&C) server.
After stealing and uploading the above data, the malicious application will check the command (CMD) from the C&C server every 60 seconds.
For Maikspy’s Windows variant (WORM_INFOKEY.A) released in April 2017, users will be tricked into downloading a MiaKhalifa.rar file containing the files. README.txt provides the victim with instructions on how to turn off anti-virus software and how to open the network. Only if the victim follows the instructions, the attacker can steal and upload data to the C&C server.
Source, Image: TrendMicro






