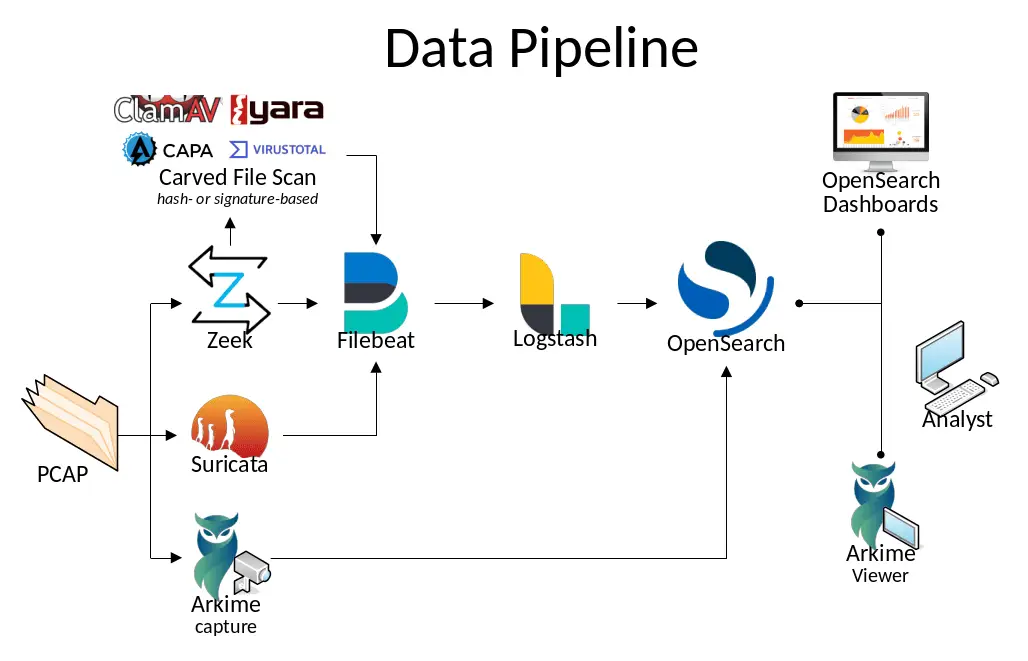
In today’s complex cybersecurity landscape, effective network traffic analysis is crucial for detecting and mitigating potential threats. Malcolm, a powerful network traffic analysis tool suite, stands out as an innovative solution designed to streamline and enhance this process. By processing network traffic data in the form of packet capture (PCAP) files or Zeek logs, Malcolm offers an extensive range of features tailored to meet the needs of both large-scale security operations centers (SOCs) and smaller network environments.
Key Features and Benefits
- Seamless Data Ingestion: Malcolm effortlessly processes network traffic data in the form of full packet capture (PCAP) files and Zeek logs. This flexibility allows for both real-time analysis of live traffic and retrospective investigation of historical data.
- Advanced Data Enrichment: Malcolm enriches raw network data with valuable context, including GeoIP mapping, hardware manufacturer lookups, asset identification, and JA3 fingerprinting. This enriched data provides a comprehensive view of network activity and facilitates more effective threat hunting and investigation.
- Robust Analysis Tools: Malcolm offers a dual approach to network traffic analysis. OpenSearch Dashboards provides an intuitive interface with pre-built visualizations for quick insights, while Arkime (formerly Moloch) offers deep-dive packet analysis and powerful search capabilities.
- Streamlined Deployment: Built on a scalable Docker container architecture, Malcolm can be rapidly deployed in a variety of environments, from large-scale security operations centers (SOCs) to individual workstations for incident response engagements.
- Enterprise-Grade Security: Malcolm prioritizes data security with robust encryption protocols for all communications, ensuring the confidentiality and integrity of your network traffic data.
- Open Source and Extensible: Built upon a foundation of well-established open-source tools, Malcolm benefits from a vibrant community of contributors and offers the flexibility to integrate with your existing security ecosystem.
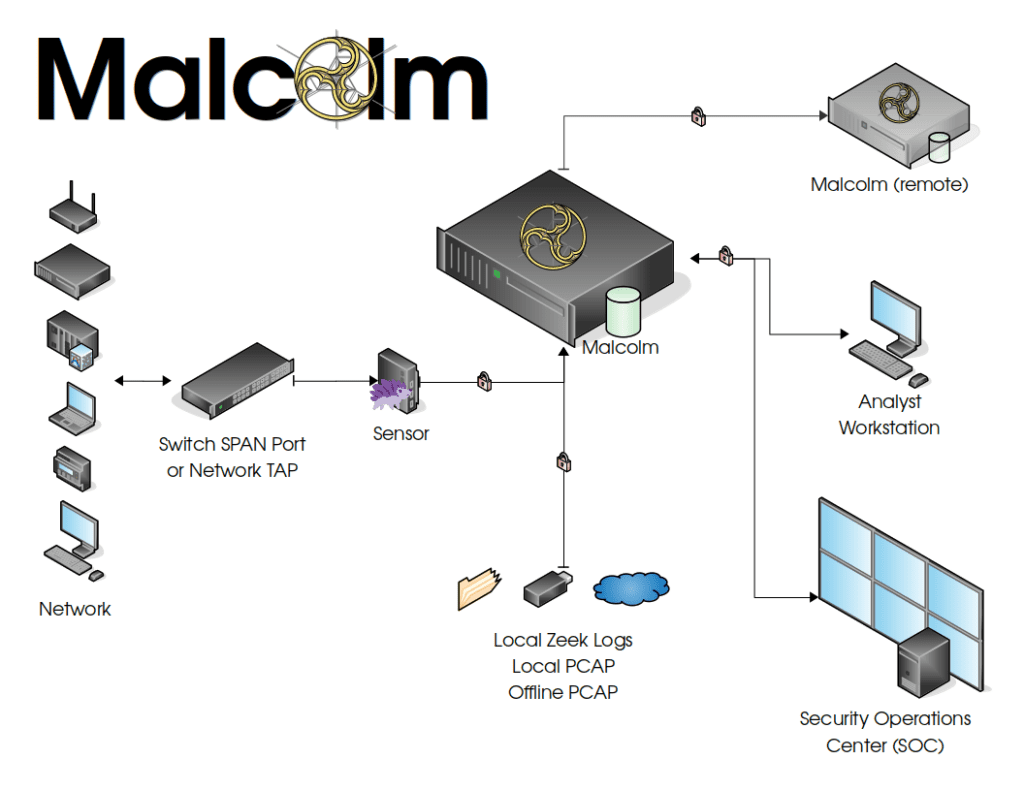
Use Cases
Malcolm’s comprehensive feature set makes it a valuable tool for a wide range of use cases:
- Threat Detection and Investigation: Malcolm’s powerful analysis tools enable security teams to quickly identify anomalies, pinpoint malicious activity, and investigate potential threats.
- Incident Response: In the event of a security incident, Malcolm can provide critical forensic evidence, helping incident responders understand the scope and impact of the attack.
- Network Performance Monitoring: Malcolm’s insights into network traffic patterns can help network administrators identify bottlenecks, optimize bandwidth usage, and improve overall network performance.
- Industrial Control Systems (ICS) Security: Malcolm’s ongoing development focuses on expanding support for ICS protocols, providing critical visibility into these sensitive environments.
For more information, visit the Malcolm documentation and explore how to use it.