Malicious Stealer Campaign Exploits Windows SmartScreen Flaw (CVE-2024-21412)
A stealthy cyber campaign is leveraging a critical flaw in Microsoft Windows SmartScreen, the built-in security feature designed to protect users from malicious downloads. This vulnerability, tracked as CVE-2024-21412, has been weaponized by multiple threat actors to deliver information-stealing malware, bypassing the usual security warnings that would alert users to potential danger.
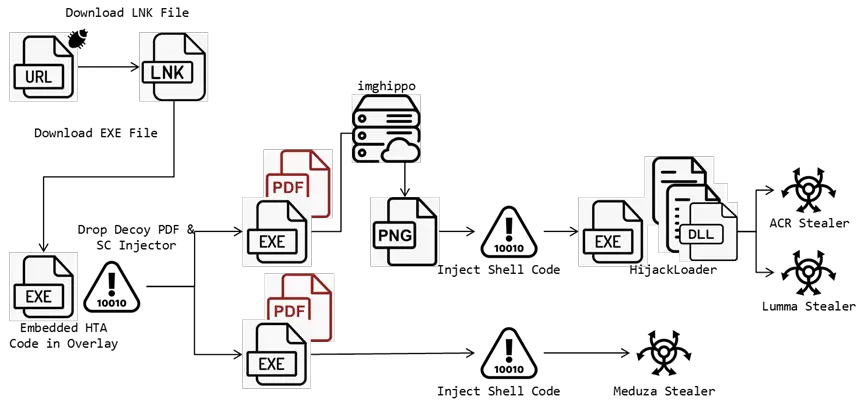
FortiGuard Labs, the threat intelligence arm of Fortinet, has identified a sophisticated attack chain The attack begins with victims being lured into clicking a crafted link to a URL file designed to download an LNK file. This LNK file subsequently downloads an executable containing an HTA script. Upon execution, the script decodes and decrypts PowerShell code to retrieve the final URLs, decoy PDF files, and a malicious shell code injector. These files aim to inject the final stealer like Meduza and ACR into legitimate processes, initiating malicious activities and exfiltrating stolen data to a command and control (C2) server.
In this attack chain, two types of injectors were identified. The first uses an image file to obtain shell code, with low detection rates on VirusTotal as of mid-July. After anti-debugging checks, it downloads a JPG file from “hxxps://i.imghippo[.]com/files/0hVAM1719847927[.]png,” then uses the Windows API “GdipBitmapGetPixel” to access the pixels and decode the bytes to retrieve the shell code. It then calls “dword ptr ss:[ebp-F4]” to the entry point of the shell code, which obtains all APIs from a CRC32 hash, creates a folder, and drops files in “%TEMP%.” These dropped files, identified by typical bytes “\x49\x44\x41\x54\xC6\xA5\x79\xEA,” are known as HijackLoader.
The second injector decrypts its code from the data section and uses a series of Windows API functions—NtCreateSection, NtMapViewOfSection, NtUnmapViewOfSection, NtMapViewOfSection again, and NtProtectVirtualMemory—to perform shell code injection.
These stealers are designed to siphon a wide range of sensitive information, leaving victims vulnerable to identity theft, financial fraud, and corporate espionage. The threat actors have designed various injectors to evade detection and use different PDF files to target specific regions, including North America, Spain, and Thailand.
The exploitation of CVE-2024-21412 has been ongoing for several months, despite a patch being released by Microsoft in February. This indicates a persistent and evolving threat that requires constant vigilance and proactive measures to mitigate. Organizations must prioritize patching vulnerabilities, deploying advanced threat detection systems, and educating users about the risks of interacting with unknown links and files.
Related Posts:
- Cybercriminals Escalate Attacks Exploiting Microsoft SmartScreen Flaw (CVE-2024-21412)
- New DarkGate Malware Campaign Exploits 0-day CVE-2024-21412 Flaw
- CVE-2024-21351 & CVE-2024-21412: Two 0-days flaws in Microsoft February 2024 Patch Tuesday
- Researchers Published PoC Exploit for Windows Zero-Day CVE-2023-36025 Vulnerability
- New variant of Mispadu Stealer is Exploiting CVE-2023-36025 Vulnerability





