Mariana Trench: security focused static analysis platform targeting Android
Mariana Trench
Mariana Trench is a security-focused static analysis platform targeting Android. The tool provides an extensible global taint analysis similar to pre-existing tools like Pysa for Python. The tool leverages existing static analysis infrastructure (e.g, SPARTA) built on top of Redex.
By default, Mariana Trench analyzes dalvik bytecode and can work with or without access to the source code.
Sources and Sinks
Under the context of taint analysis [1], “sources” usually mean sensitive data that originates from users. For example, sources can be users’ passwords or locations. “Sinks” usually mean functions or methods that use data that “flows” from sources, where the term “flow” is generally defined under the context of “information flow” [2].
An operation, or series of operations, that uses the value of some object, say x, to derive a value for another, say y, causes a flow from x to y
As an example, sinks can be a logging API that writes data into a log file.
What does Mariana Trench do?
A flow from sources to sinks indicate that for example user passwords may get logged into a file, which is not desirable and is called an “issue” under the context of Mariana Trench. Mariana Trench is designed to automatically discover such issues.
Usage
The usage of Mariana Trench can be summarized in three steps:
- Specify customized “sources” and “sinks”. (See Customize Sources and Sinks)
- Run Mariana Trench on an arbitrary Java repository (with the sources and sinks specified in Step 1), whether it be a repository for an Android application project or for a vanilla (or plain old) Java project.
- View the analysis results from a web browser. (For steps 2 and 3 see Getting Started)
Exploring Results
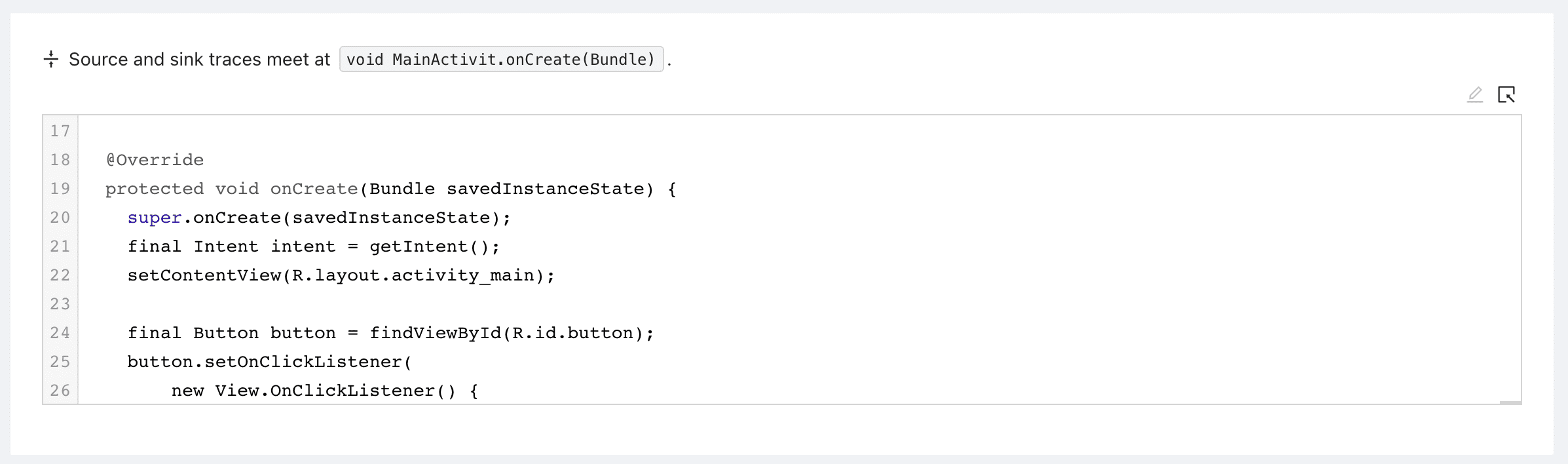
Let’s focus on the remote code execution issue found in the sample app. You can identify it by its issue code 1 (for all remote code executions) and the callable void MainActivity.onCreate(Bundle). With only 4 issues to see it’s easy to identify the issue manually but once more rules run, the filter functionality at the top right of the page comes in handy.
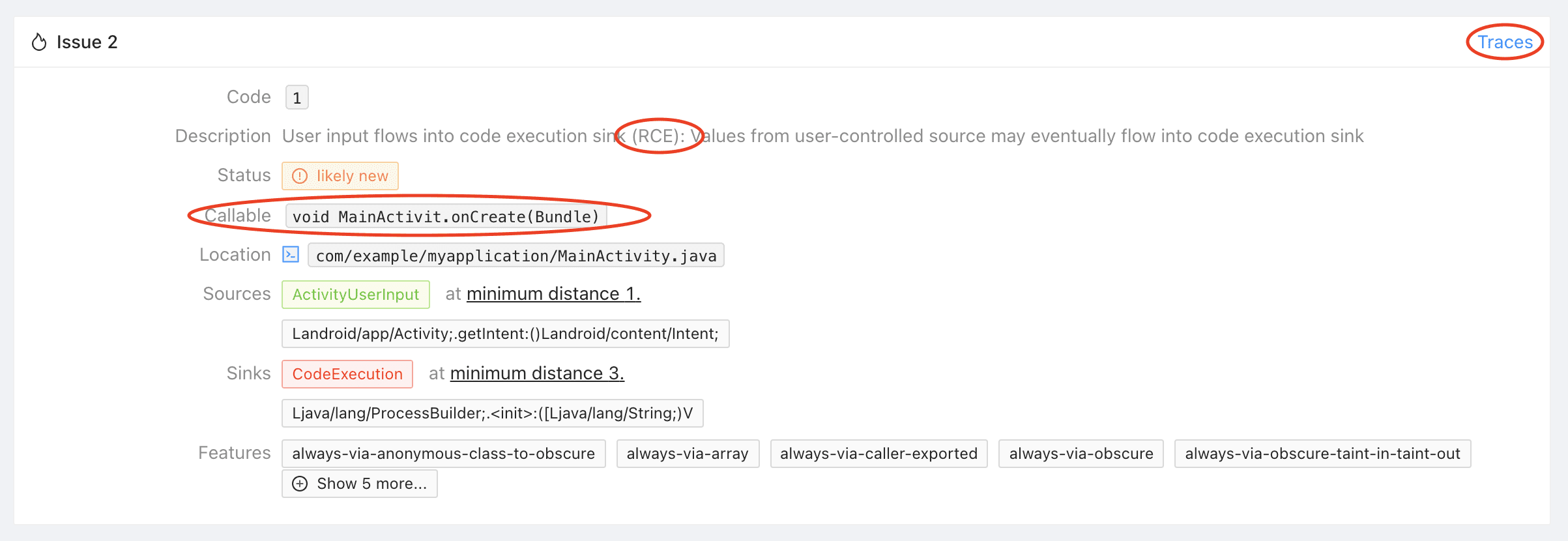
The issue tells you that Mariana Trench found a remote code execution in MainActivity.onCreate where the data is coming from Activity.getIntent one call away and flows into the constructor of ProcessBuilder 3 calls away. Click on “Traces” in the top right corner of the issue to see an example trace.
The trace surfaced by Mariana Trench consists of three parts.
The source trace represents where the data is coming from. In our example, the trace is very short: Activity.getIntent is called in MainActivity.onCreate directly.
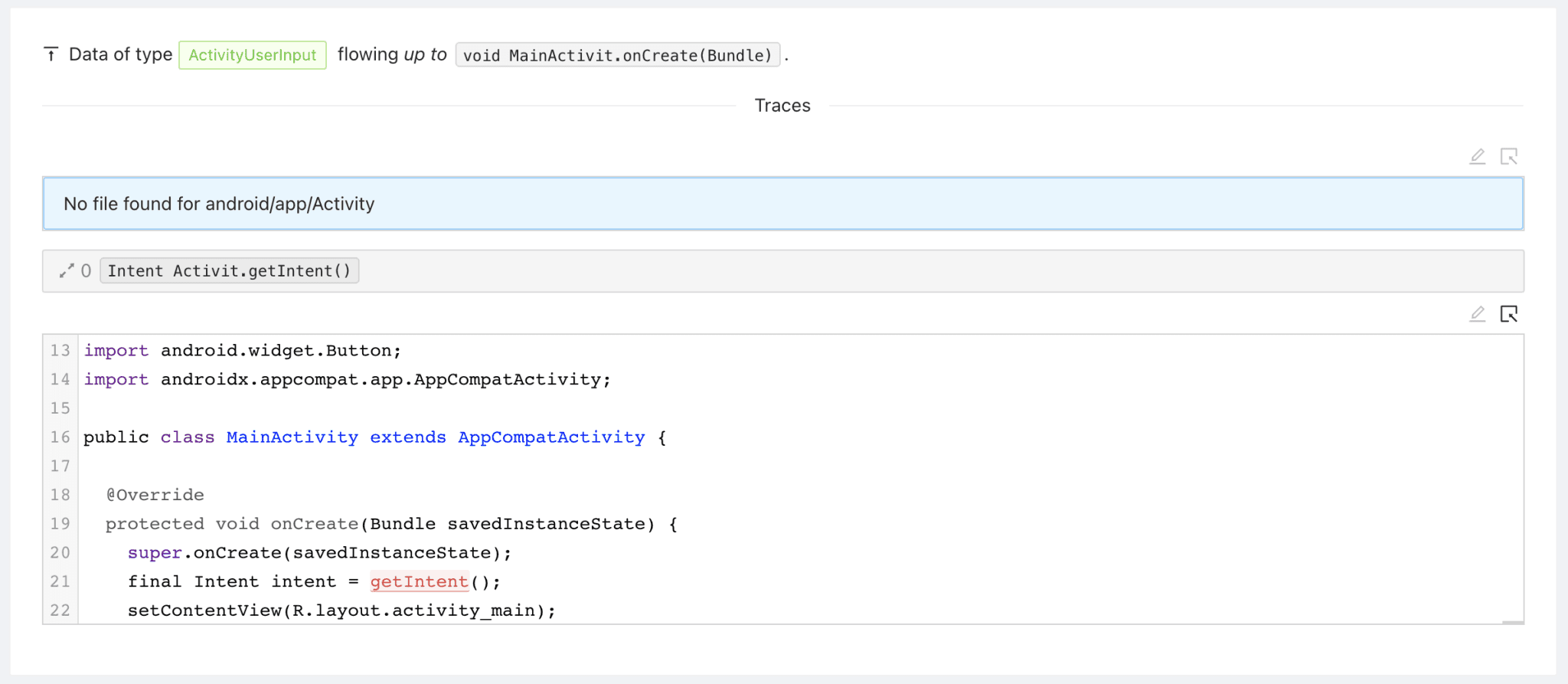
The trace root represents where the source trace meets the sink trace. In our example, this is the activities onCreate method.

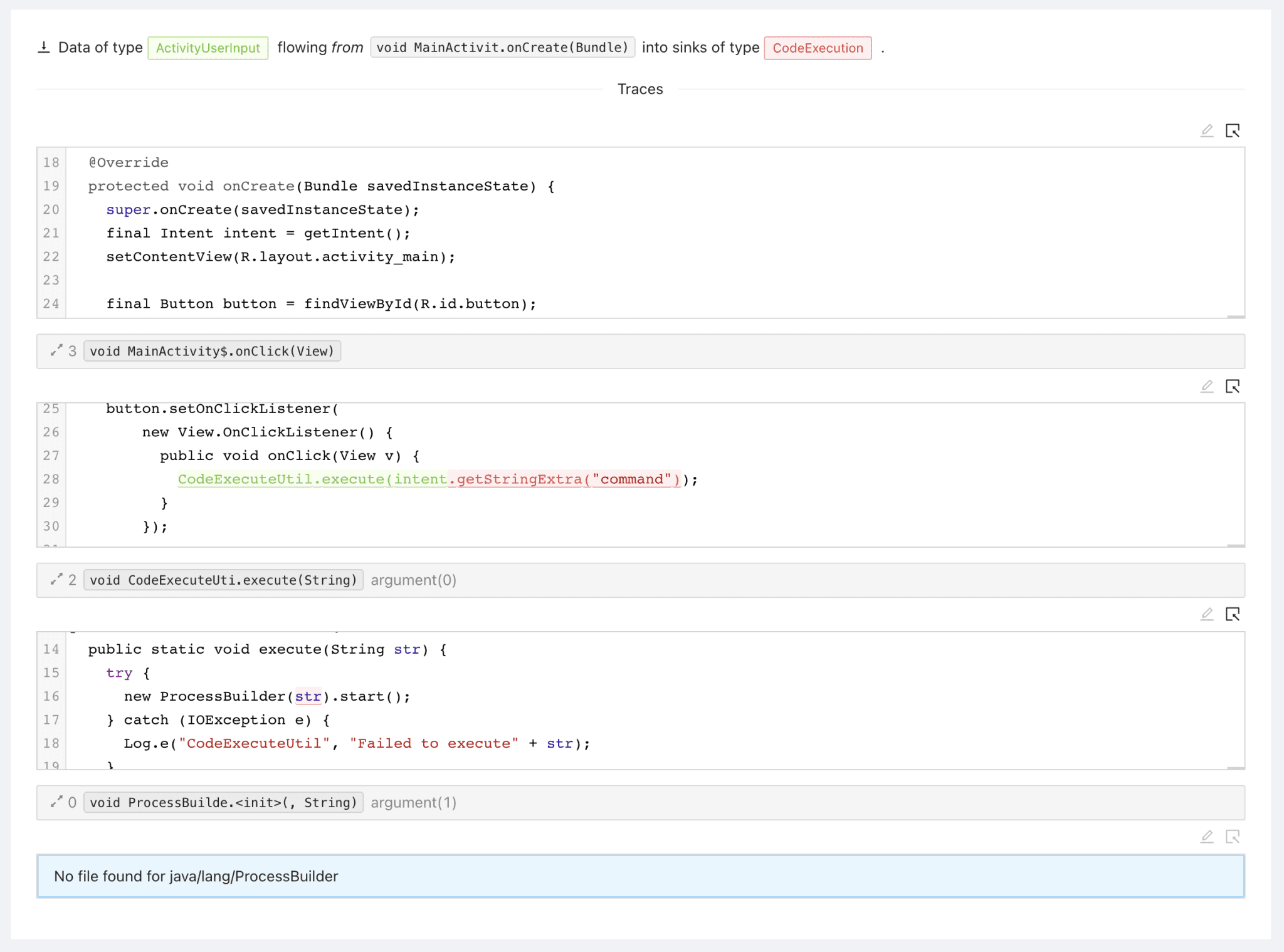
The final part of the trace is the sink trace: This is where the data from the source flows down into a sink. In our example from onCreate, to onClick, to execute, and finally into the constructor of ProcessBuilder.
Install
Copyright (c) 2013-present, Facebook, Inc.





